Botnets have become one of the biggest threats to security systems today. Their growing popularity among cybercriminals comes from their ability to infiltrate almost any internet-connected device, from DVR players to corporate mainframes.
Botnets are also becoming a larger part of cultural discussions around cyber security. Facebook’s fake ad controversy and the Twitter bot fiasco during the 2016 presidential election worry many politicians and citizens about the disruptive potential of botnets. Recently published studies from MIT have concluded that social media bots and automated accounts play a major role in spreading fake news.
The use of botnets to mine cryptocurrencies like Bitcoin is a growing business for cyber criminals. It’s predicted the trend will continue, resulting in more computers infected with mining software and more digital wallets stolen.
Aside from being tools for influencing elections and mining cryptocurrencies, botnets are also dangerous to corporations and consumers because they’re used to deploy malware, initiate attacks on websites, steal personal information, and defraud advertisers.
It’s clear botnets are bad, but what are they exactly? And how can you protect your personal information and devices? Step one is understanding how bots work. Step two is taking preventative actions.
How Do Botnets Work?
To better understand how botnets function, consider that the name itself is a blending of the words “robot” and “network”. In a broad sense, that’s exactly what botnets are: a network of robots used to commit cyber crime. The cyber criminals controlling them are called botmasters or bot herders.
Size Matters
To build a botnet, botmasters need as many infected online devices or “bots” under their command as possible. The more bots connected, the bigger the botnet. The bigger the botnet, the bigger the impact. So size matters. The criminal’s ultimate goal is often financial gain, malware propagation, or just general disruption of the internet.
Imagine the following: You’ve enlisted ten of your friends to call the Department of Motor Vehicles at the same time on the same day. Aside from the deafening sounds of ringing phones and the scurrying of State employees, not much else would happen. Now, imagine you wrangled 100 of your friends, to do the same thing. The simultaneous influx of such a large number of signals, pings, and requests would overload the DMV’s phone system, likely shutting it down completely.
Cybercriminals use botnets to create a similar disruption on the internet. They command their infected bot army to overload a website to the point that it stops functioning and/or access is denied. Such an attack is called a denial of service or DDoS.
Botnet Infections
Botnets aren’t typically created to compromise just one individual computer; they’re designed to infect millions of devices. Bot herders often deploy botnets onto computers through a trojan horse virus. The strategy typically requires users to infect their own systems by opening email attachments, clicking on malicious pop up ads, or downloading dangerous software from a website. After infecting devices, botnets are then free to access and modify personal information, attack other computers, and commit other crimes.
More complex botnets can even self-propagate, finding and infecting devices automatically. Such autonomous bots carry out seek-and-infect missions, constantly searching the web for vulnerable internet-connected devices lacking operating system updates or antivirus software.
Botnets are difficult to detect. They use only small amounts of computing power to avoid disrupting normal device functions and alerting the user. More advanced botnets are even designed to update their behavior so as to thwart detection by cybersecurity software. Users are unaware they’re connected device is being controlled by cyber criminals. What’s worse, botnet design continues to evolve, making newer versions harder to find.
Botnets take time to grow. Many will lay dormant within devices waiting for the botmaster to call them to action for a DDoS attack or for spam dissemination.
Vulnerable Devices
Botnets can infect almost any device connected directly or wirelessly to the internet. PCs, laptops, mobile devices, DVR’s, smartwatches, security cameras, and smart kitchen appliances can all fall within the web of a botnet.
Although it seems absurd to think of a refrigerator or coffee maker becoming the unwitting participant in a cyber crime, it happens more often than most people realize. Often appliance manufacturers use unsecure passwords to guard entry into their devices, making them easy for autonomous bots scouring the internet to find and exploit.
As the never-ending growth of the Internet of Things brings more devices online, cyber criminals have greater opportunities to grow their botnets, and with it, the level of impact.
In 2016, a large DDoS attack hit the internet infrastructure company Dyn. The attack used a botnet comprised of security cameras and DVRs. The DDoS disrupted internet service for large sections of the country, creating problems for many popular websites like Twitter and Amazon.
Botnet Attacks
Aside from DDoS attacks, botmasters also employ botnets for other malicious purposes.
Ad Fraud
Cybercriminals can use the combined processing power of botnets to run fraudulent schemes. For example, botmasters build ad fraud schemes by commanding thousands of infected devices to visit fraudulent websites and “click” on ads placed there. For every click, the hacker then gets a percentage of the advertising fees.
Selling and Renting Botnets
Botnets can even be sold or rented on the internet. After infecting and wrangling thousands of devices, botmasters look for other cybercriminals interested in using them to propagate malware. Botnet buyers then carry out cyber attacks, spread ransomware, or steal personal information.
Laws surrounding botnets and cybercrime continue to evolve. As botnets become bigger threats to internet infrastructure, communications systems, and electrical grids, users will be required to ensure their devices are adequately protected from infection. It’s likely cyber laws will begin to hold users more responsible for crimes committed by their own devices.
Botnet Structures
Botnet structures usually take one of two forms, and each structure is designed to give the botmaster as much control as possible.
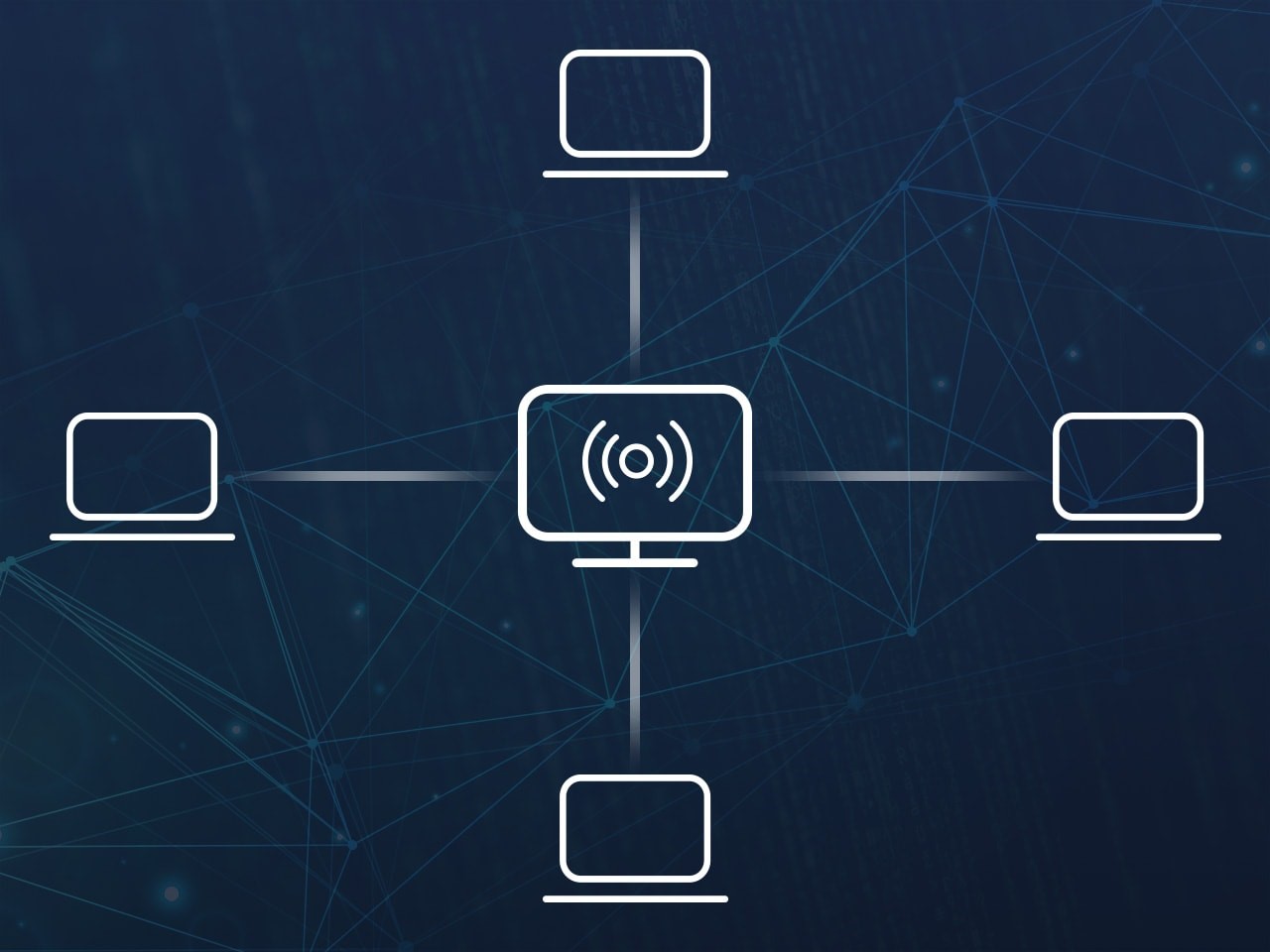
Client-server model
The client-server botnet structure is set up like a basic network with one main server controlling the transmission of information from each client. The botmaster uses special software to establish command and control (C&C) servers to relay instructions to each client device.
While the client-server model works well for taking and maintaining control over the botnet, it has several downsides: it’s relatively easy for law enforcement official to location of the C&C server, and it has only one control point. Destroy the server, and the botnet is dead.

Peer-to-peer
Rather than relying on one centralized C&C server, newer botnets have evolved to use the more interconnected peer-to-peer (P2P) structure. In a P2P botnet, each infected device functions as a client and a server. Individual bots have a list of other infected devices and will seek them out to update and to transmit information between them.
P2P botnet structures make it harder for law enforcement to locate any centralized source. The lack of a single C&C server also makes P2P botnets harder to disrupt. Like the mythological Hydra, cutting off the head won’t kill the beast. It has many others to keep it alive.
Botnet Prevention
It should be clear by now that preventing botnet infection requires a comprehensive strategy; one that includes good surfing habits and antivirus protection. Now that you’ve armed yourself with the knowledge of how botnets work, here are some ways to keep botnets at bay.
Update your operating system
One of the tips always topping the list of malware preventative measures is keeping your OS updated. Software developers actively combat malware; they know early on when threats arise. Set your OS to update automatically and make sure you’re running the latest version.
Avoid email attachments from suspicious or unknown sources
Email attachments are a favorite source of infection for many types of viruses. Don’t open an attachment from an unknown source. Even scrutinize emails sent from friends and family. Bots regularly use contact lists to compose and send spam and infected emails. That email from your mother may actually be a botnet in disguise.
Avoid downloads from P2P and file sharing networks
Botnets use P2P networks and file sharing services to infect computers. Scan any downloads before executing the files or find safer alternatives for transferring files.
Don’t click on suspicious links
Links to malicious websites are common infection points, so avoid clicking them without a thorough examination. Hover your cursor over the hypertext and check to see where the URL actually goes. Malicious links like to live in message boards, YouTube comments, pop up ads, and the like.
Get Antivirus Software
Getting antivirus software is the best way to avoid and eliminate botnets. Look for antivirus protection that’s designed to cover all of your devices, not just your computer. Remember, botnets sneak into all types of devices, so look software that’s comprehensive in scope.
With the Internet of Things increasing, so too does the potential for botnet size and power. Laws will eventually change to hold users more responsible for the actions of their devices. Taking preventative action now will protect your identity, data, and devices.






18 comments
Thanks for publishing this helpful article
Thank you for the information!
I’m making a presentation of botnets in Albanian language.
Hi, Ervish!
We are glad to know the information has been useful. Good luck with the presentation! We are sure you will be ok. ?
Kind regards,
Panda Security.
Excellent description of security issue I have been trying to articulate for years. All devices with various OS on network show same symptoms I.e. no admin priviligess despite GUI info. I am uning Panda currently but infection is self protecting by blocking installation of some security software, removing .dll files that I assume are critical to repair. Given the fact that I am client to botnet host, even security programs that are capable of detecting issue throw feedback, “unable to unlock ( or delete);file. Attempts to manually take ownership and delete either fail or lock entire c\ drive.
It actually appears as if a 2nd OS ( Windows 10 eg.) is installed and original locked. Either that or a wholesale trade out of drivers, and cfg. Type files (;and built in admin) installed. Reset of OSmdoes not help and new devices infected before finish setting up.
Help appreciated beyond expressable thanks if you can offer actual fix. Problem seems to be both on network and on devices.
Hi William,
Please contact support on https://www.pandasecurity.com/support/#homeusers
Thanks for reading us!
Kind regards,
Panda Security.
How does bots malware spreads in comouter?
Hi Alnadzmer!
A bot is a type of malware that allows a hacker to take control of the targeted computer. Also known as ‘Web robots, bots are usually part of a network of infected machines, known as a “botnet”, controlled by cyber criminals called ‘”botmasters”.
After taking control of your system, a bot can carry out a variety of automated tasks which can show strange messages, slow down your system or even crash it. With bots, a hacker can steal your confidential information by sending spams, deny certain services on the internet, and even engage in ‘click fraud’. To protect yourself from a bot attack, make sure you have turned on the ‘automatically update’ settings on your system. Install the most effective antivirus software.
and use common sense!!
We hope this helps! Thanks for reading us!
Kind regards,
Panda Security.
Very USeful
Thank you so much for this instructive informations
Thanks for reading us!
Very crisp and clear explanation. Thank you very much
Which Botnet can Access the credentials and cookies and stuff from all browser and send to the botnet owner
can you help me with it
I’ve just read the book “We are Anonymous”. The book told about several DDoS attacks using botnets, one of them larger than 30,000 bots (owned by a guy nicknamed “Civil”). What way use the botmaster to command so many bots in a while?