You’ve probably heard of companies having massive data breaches and thought, “How did that happen?” or “What if I had been affected?” A data breach can be scary, as it’s a type of security violation where confidential data is exposed or stolen without authorization. They can also have serious outcomes like payment card fraud or even identity theft.
Here’s a deeper look into how data breaches can affect you, how they happen and how to prevent them.
What Is a Data Breach?
A data breach is a security incident where private, confidential or sensitive information is exposed or stolen by someone without authorization. They happen for various reasons, from human error to malicious attacks, and the consequences can be significant. Anyone is at risk of a data breach, especially if their accounts aren’t protected.
Data breaches can result in:
- Stolen credentials
- Identity theft
- Compromised assets
- Payment card fraud
- Third-party access to your accounts
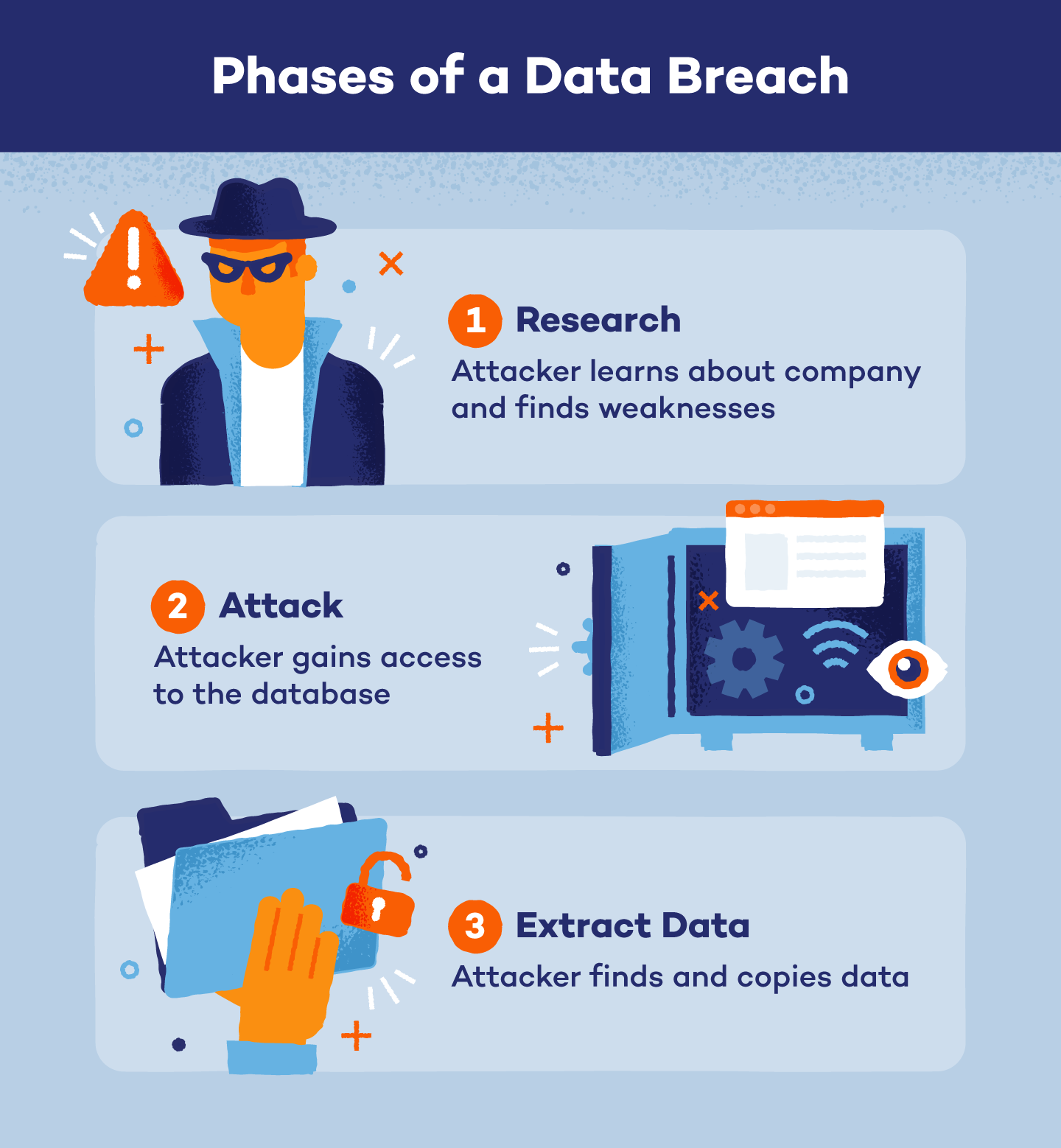
Phases of a Data Breach
Unlike what your imagination may suggest, a malicious data breach looks less like someone dressed in all black sneaking into a building with a flash drive and more like people in a remote location scheming about how to hack into a database.
However, not every data breach is malicious. Some are the result of human error or negligence, but we’ll go over that more in the next section. Here are the three stages of an intentional data breach.
1. Research
In the very beginning of a data breach, an attacker picks a target, usually a company or organization with access to personal data, and researches how they can infiltrate their target’s database. The attacker gathers information like employee information, financial records and security budgets. They also look for vulnerabilities like weak passwords, outdated software or unprotected network connections.
2. Attack
Taking what they’ve learned from their research, the attacker can now attack the data system. Here are some common ways attackers gain access to company systems or networks:
- Stolen credentials: Compromised usernames and passwords can be collected through the dark web, phishing, brute force attacks or even physical theft of devices to impersonate legitimate users and gain access to systems.
- Phishing emails: Attackers also use personal information from their research, like job titles or coworkers’ names, to trick their targets into providing credentials or clicking a malicious link that downloads malware onto their computer.
- Malware: Hackers use malicious software to secretly infect and take control of a victim’s computer or network to steal data.
- Vulnerability exploitation: The attacker uses any vulnerabilities like weak passwords, misconfigurations or unpatched systems found within a company’s computer system to gain access.
- Denial of service (DoS) attacks: This attack overwhelms a website with excessive fake traffic until it’s unavailable to actual users. It’s a distraction from other security weaknesses so attackers can carry out data breaches.
3. Extract Data
Once the attackers have gained access to the target’s system or network, they can locate and extract valuable or sensitive data, including personal information, financial records or any other data that could be sold on the dark web. The extracted data is then copied or transferred to the attacker’s own servers where they can control and exploit it. Oftentimes a company won’t know its data has been stolen until a third party like law enforcement, service providers or customers report the breach.
How Data Breaches Happen
Data breaches can be a type of cybercrime if done maliciously, but it can also be an unintentional error from someone with authorized access to the data. Here are the causes of data breaches:
- Malicious insiders: People with access to the database intentionally misuse their access privileges to steal or leak sensitive information.
- Malicious outsiders: Someone from outside the organization attacks a database via phishing, malware, vulnerability attacks or denial of service (DoS) attacks.
- Accidental insiders: Individuals with authorized data access accidentally expose data due to mistakes or lack of security measures. This is technically classified as a data leak since it’s an internal mistake; however, it still has the same consequences for those affected, and the company may still face legal ramifications.
Major Data Breaches and Their Consequences
Unfortunately, data breaches happen regularly, and every company without appropriate security measures in place is at risk. Check out these recently reported data breaches and their consequences:
- T-Mobile: In 2023, T-Mobile was the victim of two data breaches. The first data breach affected over 37 million people, and the second affected over 800 people. Personal information including names, contact details, account PINs, Social Security numbers, birthdays and government IDs were compromised.
- ChatGPT: A vulnerability in ChatGPT’s open-source library caused a data breach in March of 2023. The breach exposed 1.2% of ChatGPT Plus subscribers’ names, payment addresses, email addresses, credit card expiration dates and the last four digits of credit card numbers during a nine-hour window.
- Roblox: Almost 4,000 attendees of the Roblox Developer Conference had personal data including physical addresses, names, email addresses, dates of birth and phone numbers breached in July of 2023.
Data Breach Prevention
Companies with your personal data are responsible for safeguarding it, and you could still be a victim of a data breach even if you follow data security best practices. However, you can make it harder for attackers to use your devices or passwords to gain access to databases with these tips:
- Update software: Regularly updating your software ensures you have the latest security patches and fixes potential vulnerabilities attackers could exploit so you can avoid getting hacked.
- Encrypt data: Encryption converts your data into unreadable code so attackers have a harder time accessing or understanding your information. Some ways to encrypt your data include password managers, file encryption software or cloud storage.
- Upgrade devices: Keeping your devices up to date ensures you have the latest security features and protection against known vulnerabilities. You don’t always need the latest model, but you should upgrade when the manufacturer no longer supports your current software.
- Use strong passwords: Strong, unique passwords for each account makes it harder for attackers to guess or crack your credentials. Passwords should be at least eight characters (but the longer, the better) and have a combination of numbers, symbols and uppercase and lowercase letters.
- Implement multi-factor authentication: An additional verification step, like a unique code sent to your phone, is required for logging into your accounts with multi-factor authentication, making it more difficult for attackers to get into your account even if they have your password.
Data breaches can have serious consequences. Follow security best practices and use Panda Security’s antivirus software to further protect your accounts.





