A root certificate is a trusted digital certificate issued by a certificate authority (CA) that serves as the foundation for verifying the authenticity of other certificates in a public key infrastructure (PKI). It establishes trust by enabling secure connections, such as HTTPS, by validating the chain of trust between a website and its visitors.
Root, intermediate and SSL certificates — oh, my! These are terms you may have heard while browsing online. But what is a root certificate, and how does it differ from other digital certificates?
When browsing the internet, you probably don’t consciously think about data integrity, privacy protection and end-entity authentication. But even if you’re not thinking about online security, root certificates and the SSL system are.
Explore the role of root certificates in online security, how they work with intermediate and SSL certificates and why they’re essential for protecting your data.
What Is a Root Certificate?
A root certificate is a digital certificate issued by a root certificate authority (CA), the trusted entity responsible for authenticating and issuing SSL certificates. These certificates are foundational to the TLS/SSL system, enabling secure communications over the internet by validating the authenticity of websites and services.
Sometimes referred to as a trusted root certificate, the root certificate is central to the trust model within the public key infrastructure (PKI). It uses a private key — a highly secure form of encryption — to sign other digital certificates. This signature signals to browsers and devices that the certificate is legitimate, streamlining the authentication process without requiring multiple verification steps.
Root certificates are stored in root stores across devices, which contain pre-installed certificates that validate and support secure browsing. These SSL root certificates ensure seamless trust and security across browsers and operating systems, forming the backbone of online data integrity and protection.
What Are Certificate Chains?
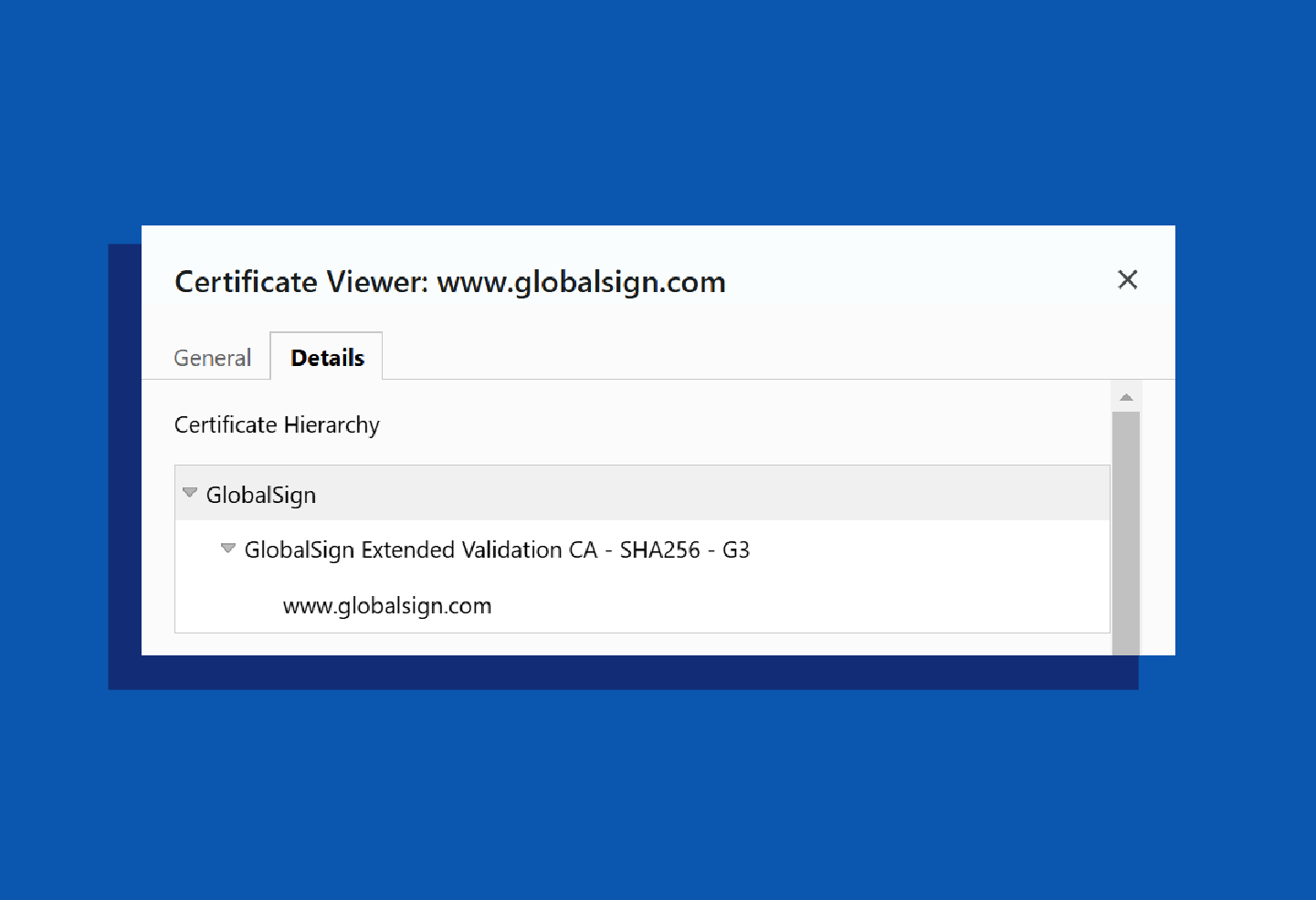
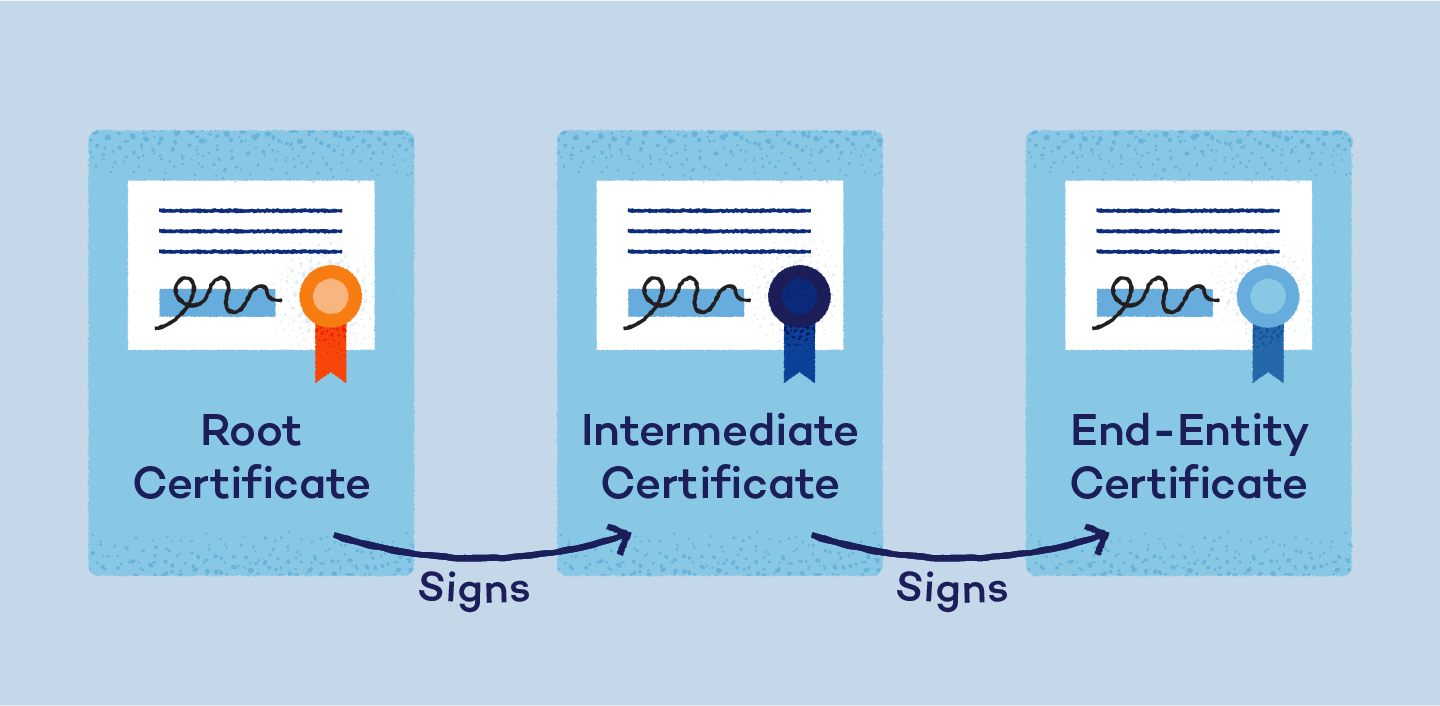
Certificate chains, also known as chains of trust, are the hierarchical links that connect a root certificate to the end-entity certificate used to secure a website or service. These chains validate the authenticity of an SSL certificate by tracing its lineage back to a trusted root certificate. This ensures each step in the chain is verified, providing secure connections for users.
There are three main types of certificates in a certificate chain:
- Root certificate: This is the foundational certificate that establishes trust. It’s stored in root stores across devices and is responsible for signing intermediate certificates.
- Intermediate certificate: This certificate acts as a middleman, extending trust from the root certificate to end-entity certificates. Using intermediates adds an extra layer of security by limiting direct exposure of the root certificate.
- End-entity or server certificate: This is the SSL certificate issued to a website or service. It ensures secure communication between the website and its visitors by encrypting data and authenticating the server’s identity.
The certificate chain process activates when a browser attempts to authenticate a website. Here’s how it works:
- A certificate signing request (CSR) is generated.
- The root certificate generates a private key.
- The CSR is sent to a CA.
- The CA uses the private key to sign an SSL certificate.
- The browser verifies the certificate’s trustworthiness based on the root signature.
Can There Be Multiple Intermediate Certificates?
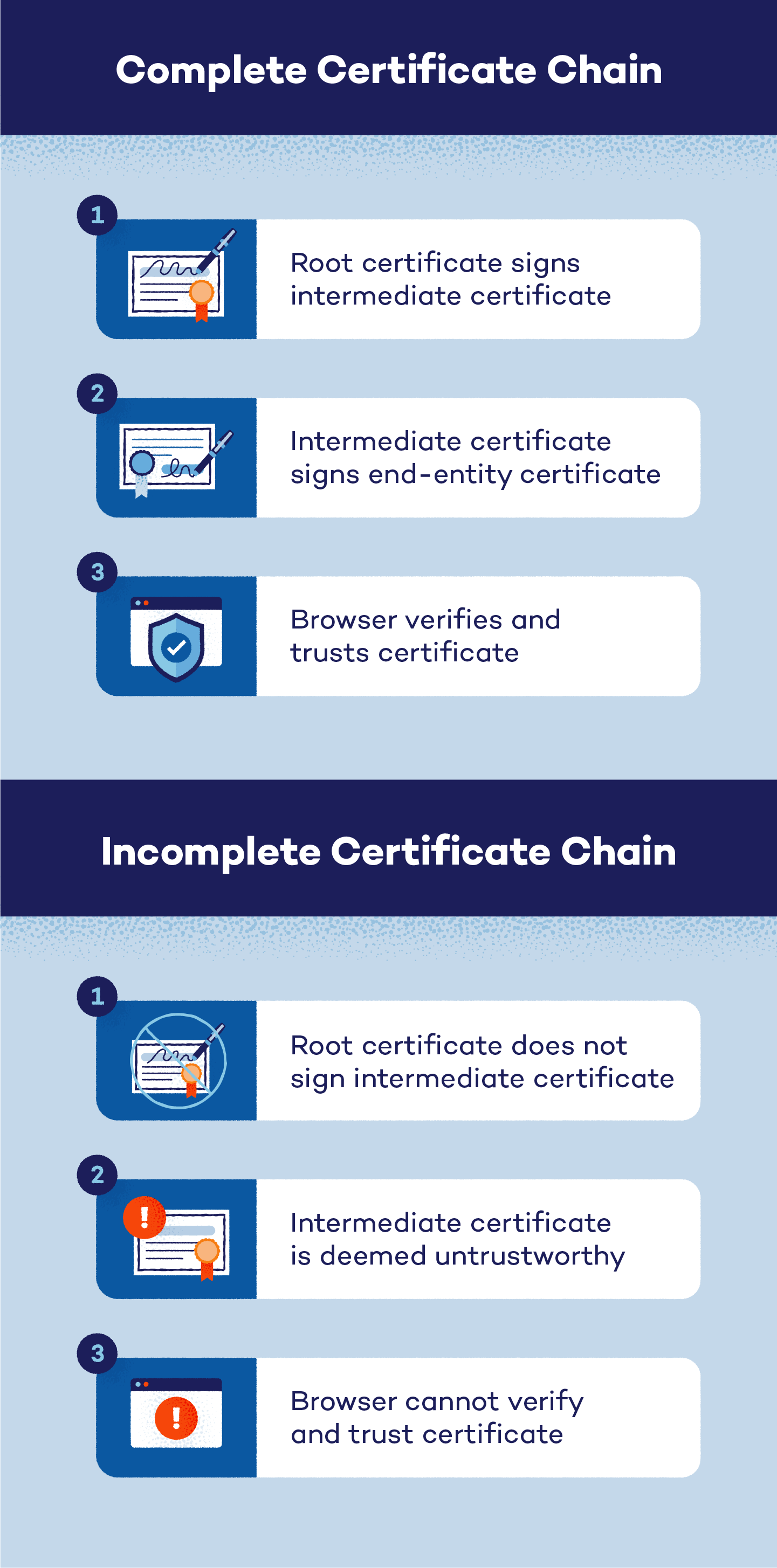
Yes, there can be multiple intermediate certificates between a trusted root and its end entity. Many CAs have begun allowing intermediate certificates to verify and authenticate requests before connecting them to a root certificate.
The CA will sign an intermediate certificate with a private key, passing along its trust. After an intermediate certificate receives a CA’s trust, it can use its own private key to sign an end-entity certificate. During this process, there can be more than one intermediate certificate placed between a trusted root and its end entity.
If needed, an intermediate certificate bridges the root certificate and the end-entity certificate. This trust model ensures that only verified, trustworthy sites are accessible. If the chain’s root cannot be validated, the browser will reject the certificate to protect the user.
Chained Roots vs. Single Roots
There are two main types of root certificates: chained roots and single roots. While both are trusted and capable of issuing other digital certificates, they differ in their structure and use.
- Chained roots are part of a certificate chain and rely on intermediate certificates to sign and validate end-entity certificates. This layered approach adds flexibility and security, as it limits direct exposure of the root certificate.
- Single roots , on the other hand, operate independently without intermediates, directly signing end-entity certificates. This simpler structure is often used in smaller or closed systems where streamlined authentication is sufficient.
Key differences between these roots include their installation processes, certification stability, expiration protocols and the types of digital signatures they use.
Root and Intermediate Certificates: The Difference
Both root and intermediate certificates help browsers reach the same goal: verify and trust certificates. However, these certificate types have a few major differences:
- Value: Root certificates are automatically trusted by browsers and hold the highest value in the trust chain, while intermediate certificates, as intermediaries, are less valued in the trust chain.
- Issuance: Root certificates can directly issue other digital certificates. Intermediate certificates, on the other hand, require a CA certificate signature to sign end entities.
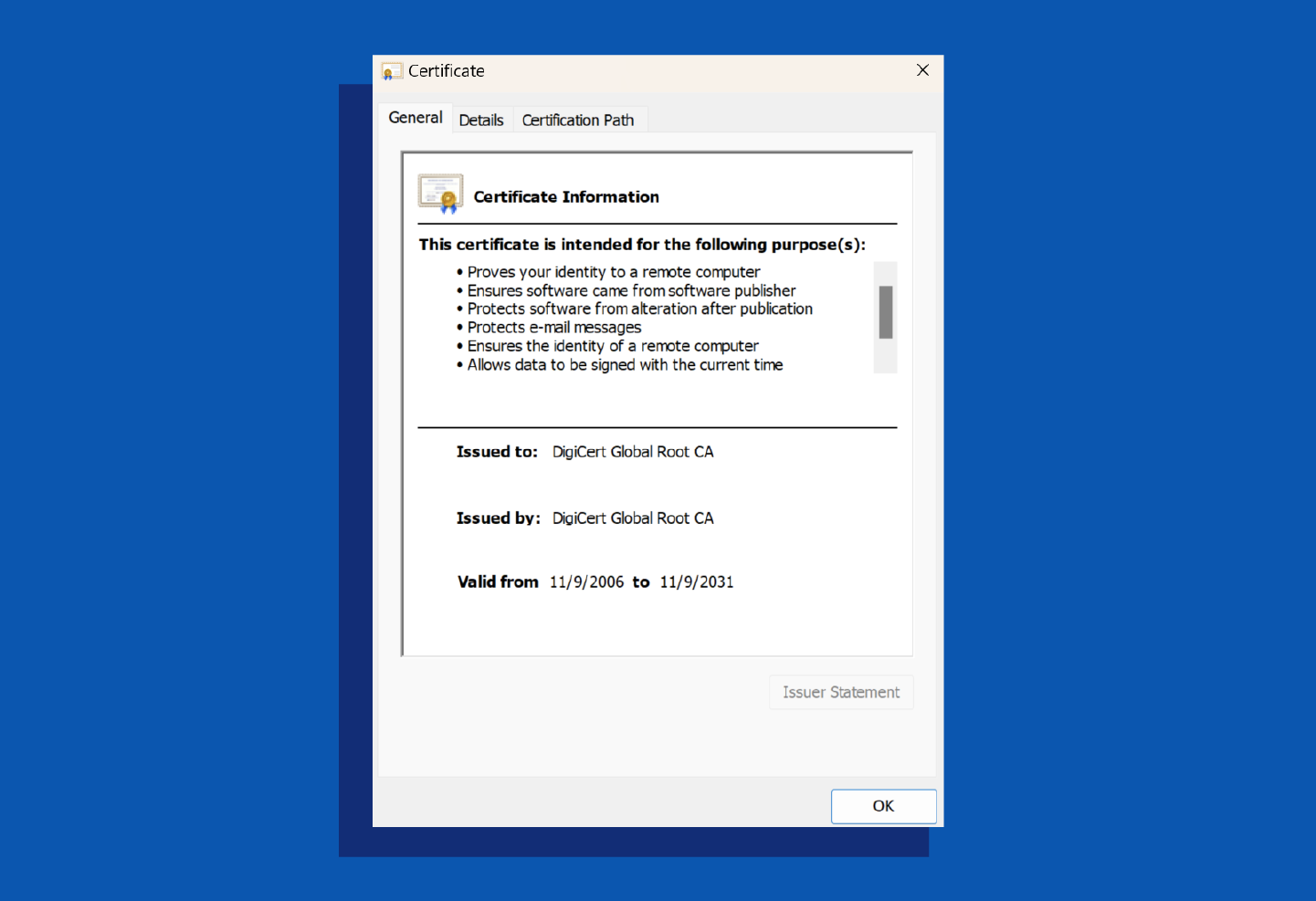
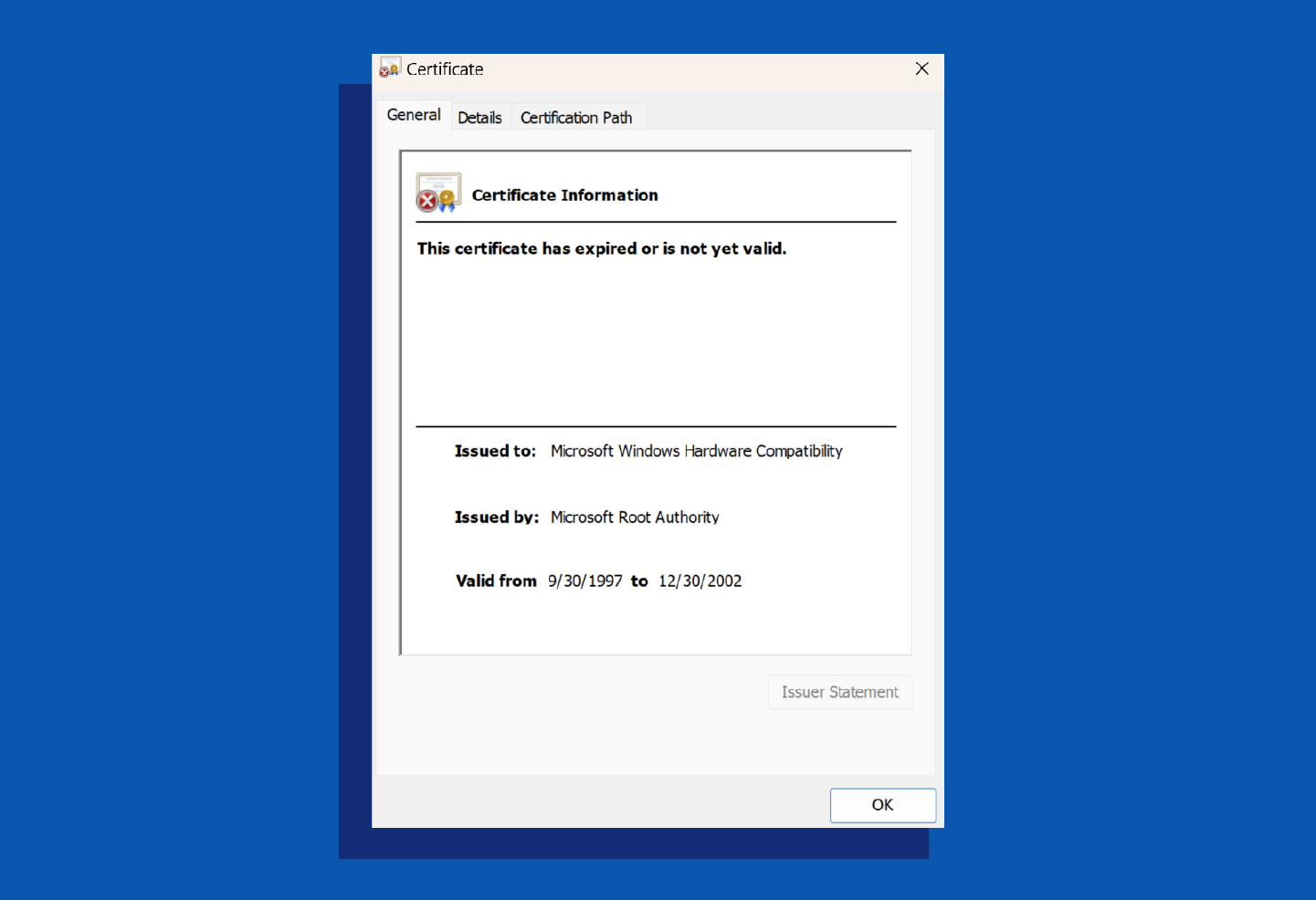
- Name: Root certificates are self-signed, with identical “Issued to” and “Issued by” fields. Intermediate certificates are cross-signed, showing different issuers and users.
- Certification path: Root certificates appear at the top of the trust model and can issue certificates without intermediaries. Intermediate certificates follow root certificates in the certification path and may include multiple intermediaries.
- Signature: Root certificates use highly secure private keys to sign intermediaries, while intermediate certificates use single keys to sign end-point certificates.
- Damages: Damage to an intermediate certificate requires removal to prevent further issues. Root certificate damage is far more dangerous, as it can compromise an entire system. Root certificates are often kept offline to reduce this risk.
- Expiration: Root certificates have long validation periods, lasting 10 to 20 years. Intermediate certificates expire more quickly, typically within one to two years.
Common Challenges With Root Systems
Root systems play an important role in digital security, but they come with challenges that can impact their efficiency and reliability. Here are some of the most common issues:
- Increased complexity of installation: The installation process for root systems often requires specialized knowledge and careful configuration to ensure trust across devices and browsers. Missteps in the setup can lead to compatibility issues or untrusted certificates, making proper installation a critical yet complex task.
- Less stability of the root: Because root certificates serve as the foundation of a certificate chain, any instability — whether due to improper handling or cyberthreats — can compromise the entire system. This makes maintaining and securing root certificates essential for ensuring ongoing trust and functionality.
- Lack of root expiration control: Root certificates often have validation periods lasting decades, but this long lifespan can create challenges for managing updates and deprecations. Without clear expiration control, outdated or compromised root certificates may remain in use, increasing the risk of security vulnerabilities.
Root Certificate FAQ
We provide answers to a few common questions about root CA certificates in the context of digital security.
What Does a Root Certificate Do?
Root certificates verify that software and website users are who they say they are. Trusted roots are crucial to the digital authentication process and online security.
Where Can I Find the Root Certificate?
Finding the root certificate depends on which browser you are using, but there are a few general steps.
- Click the lock icon next to the URL in your browser.
- Select Connection is secure .
- Choose Certificate is valid .
- In the pop-up box, verify the issuer, validity period, and type of certificate in both the general and details tabs.
Is a Root Certificate Necessary?
A root certificate is necessary because it is used to verify the authenticity of other intermediate and end-entity certificates. Without a root certificate, a system is left either unprotected or unusable.
Improve Your Security While Browsing the Web With Panda
Securing your online accounts and ensuring safe browsing experiences are essential in today’s digital world. With Panda Dome , you can protect your devices from threats while ensuring root certificates and other security measures are working to keep your data safe.
Panda Dome offers real-time protection against malware , phishing and other online dangers, so you can browse with confidence. Take control of your online security today and safeguard your digital life.





