Whale phishing is a cyberattack that specifically targets high-level executives (CEOs and CTOs) within an organization, aiming to steal sensitive information or authorize fraudulent financial transactions by impersonating trusted individuals.
Have you ever received an email from a trusted sender who really turned out to be an online phisher? If so, you’re not alone. Even large organizations like Snapchat and Seagate have fallen victim to whale phishing attacks.
When it comes to whaling, corporate email addresses and high-level employees are often the targets of these sophisticated phishing schemes. While premium protection services work well against smaller, at-home attacks, whaling attacks can slip through a bigger organization’s defenses if employees and possible targets are unaware of their possibility.
But what exactly is whaling in cybersecurity? Is there more to it than just being a cyberattack? We will answer all such questions and share some ways to detect whaling attacks so you can fortify your cyber defenses.
What Is Whale Phishing?
A whaling attack, or CEO fraud, targets high-level executives like CEOs and CFOs. Unlike regular phishing scams, whaling attacks are highly personalized and leverage sophisticated tactics to trick victims.
Instead of mass emails, attackers meticulously research their targets, gathering details like names, titles and even ongoing company projects. This intel fuels the creation of believable emails that impersonate trusted sources, often senior colleagues or business partners.
These cyberattacks try to manipulate executives into surrendering sensitive information, authorizing fraudulent payments or granting access to internal systems — all with the potential for significant financial gain for the attackers.

How Whaling Attacks Work
We’ve seen how whaling attacks target high-level executives and use sophisticated tactics to bypass security awareness training. Let’s break down the three main steps hackers use to pull off executive phishing:
Research and selection
Imagine a fisherman carefully choosing bait for a specific type of fish. In whaling attacks, the attackers are like those fishermen.
They spend time researching their targets, often by scouring the internet (company websites, social media) or even compromising low-level employee accounts to gather intel. Here’s what they might be looking for:
- Names and titles of CEOs, CFOs or other high-ranking officials
- Details about ongoing company projects or recent news
- Information about the target’s personal interests or professional network
With this intel, they can select the perfect “whales” to target and craft a convincing attack.
Crafting believable emails
Once the attackers have their target, they create a spoofed email that seems to come from a legitimate source. They might impersonate:
- A senior colleague, like the CEO or another executive
- A trusted business partner the target has worked with before
- Even someone outside the company, like a fake lawyer or consultant
Hackers use whaling social engineering techniques to carefully craft emails that are relevant to your situation. For example, the attacker might:
- Mention a specific project the target is working on and request urgent information.
- Reference a recent news article or event related to the target’s industry.
- Use personal details they’ve found online to build trust (e.g., “I hope your recent vacation to New York was enjoyable.”).
Tricking the target
These emails often create a sense of urgency or pressure to get the target to act quickly. They might include:
- Requests to click on a link to access a document or download an attachment (often containing malware that steals credentials or infects the computer)
- Instructions to wire money urgently (often to a fraudulent account)
- Pressure to respond quickly without double-checking details
Using a combination of stolen information, impersonation and urgency, whaling attacks attempt to trick even the most security-conscious executives into giving away sensitive information or granting access to company systems.
Whaling Attack Examples
Here are some common scenarios bad actors use in whaling cyberattacks:
- Fake mergers and acquisitions: The attacker impersonates someone high up in the company (CEO, CFO) and initiates contact with another executive or a trusted business partner. They might claim to be negotiating a confidential merger or acquisition and request sensitive financial documents or wire transfers to expedite the deal.
- Urgent requests from familiar faces: The attacker spoofs the email address of a colleague, advisor or client the target knows and trusts. The email might contain a fabricated story about needing immediate help with payment, document transfer or login credentials due to a technical issue or lost phone.
- Data exfiltration through fake internal communication: Attackers may gain access to a low-level employee’s email account and use it to target other employees within the company. They might pose as a manager or HR representative and request employee information (like payroll data) under the guise of a legitimate internal process.
These tactics, often combined with sophisticated social engineering techniques, make whaling attacks highly effective in compromising sensitive information and causing significant financial loss. Organizations must implement robust security measures and educate employees about the risks of these attacks.
How to Detect a Whaling Attack
Since whaling attacks have a higher return possibility, they are more strategically planned and can be difficult to detect. You can detect most whale phishing attacks through these signs:
- Spoofed and urgent emails: Many whaling attacks will use spoofed emails with urgent messages to begin an assault. These emails will look almost identical to trusted organizational emails, giving them an air of credibility that can spur action.
- Infected links, attachments and landing pages: Suspicious links, attachments and landing pages are used to deposit malware onto vulnerable devices. They can be embedded in the body of a spoofed email or text message.
- High-value targets: Whaling attacks will often target high-value individuals in an organization. These targets may have direct access to credentials or company funds.
- Impersonation: If a whaling attack does not target a CEO or COO, hackers may choose to impersonate them instead. Impersonators then target lower-level employees who may have access to servers or other sensitive information.
If one or more of these signs are present in a cyberattack, you may have the makings of a perfect storm for a whaling attack.

6 Ways to Defend Against Whaling Attacks
While whaling may be a more sophisticated phishing attack, there are still ways to prepare for and defend against it. Here are six defense tactics and whaling cyber awareness measures you can use:
- Conduct regular security training on phishing tactics, social media safety and red flags for everyone — from CEOs to interns.
- Make multi-factor authentication (MFA) mandatory, especially for wire transfers, access to sensitive data and email/data verification processes.
- Implement data loss prevention (DLP) solutions that monitor emails for suspicious activity and block spoofed addresses or malicious content.
- Tighten social media privacy and upskill employees (especially high-value targets) in robust social media privacy settings.
- Restrict access to personal information, and be mindful that both personal and professional accounts can be targeted by attackers.
- Invest in anti-phishing resources and subscribe to services offered by organizations like the Anti-Phishing Working Group (APWG).
In short, vigilance, education and technology working together are essential for safeguarding sensitive information and protecting the bottom line.
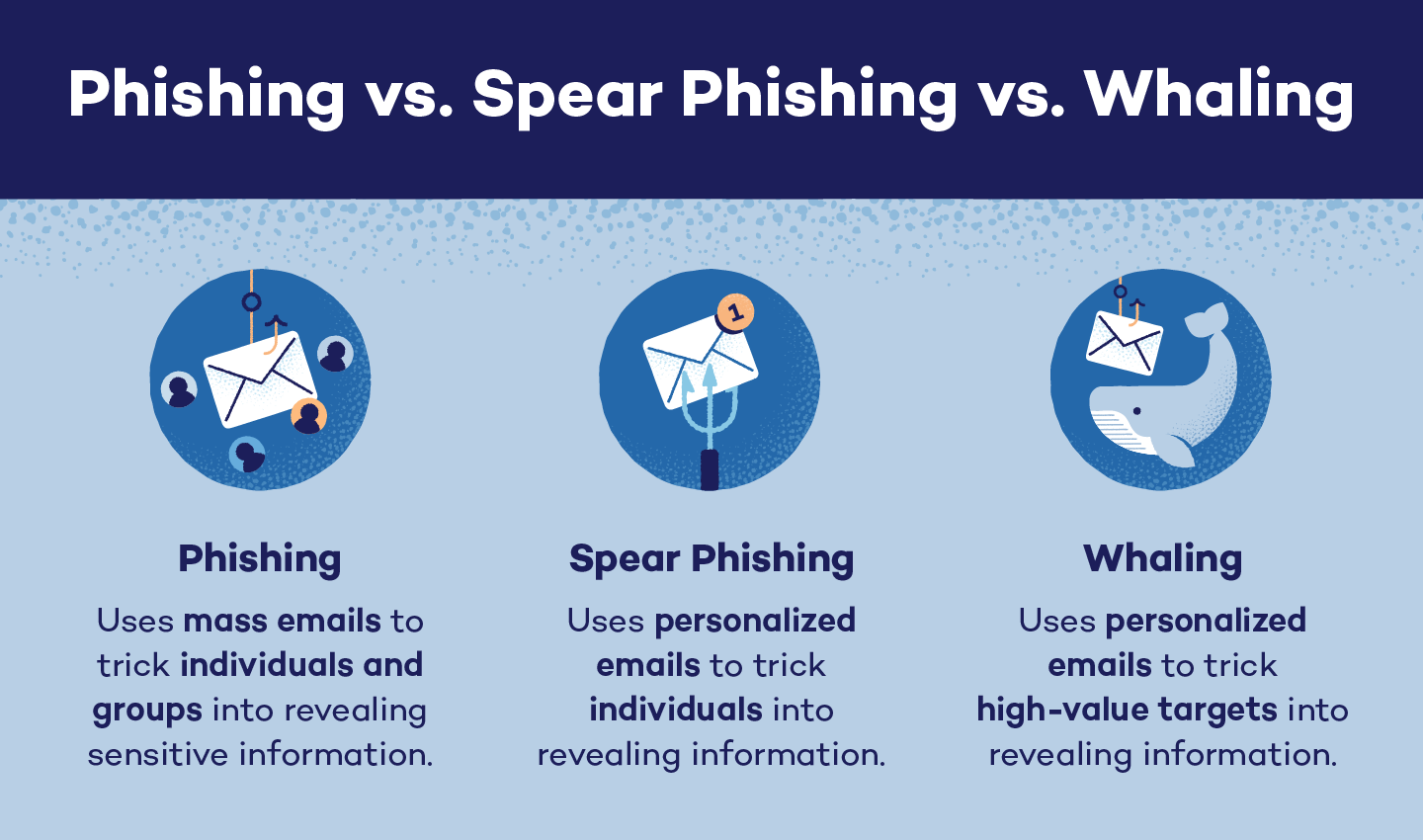
Phishing vs. Spear Phishing vs. Whaling
Phishing, spear phishing and whaling cyberattacks can easily be confused because they’re from the same family of cyberattacks. However, they are different, and each type of attack uses specific tactics.
Phishing attacks refer to the broad category of phishing schemes. These can be amateur or sophisticated attacks, and they target a variety of different entities — including individuals, groups and organizations. Phishing attacks try to fool or convince someone to take action, which can be as simple as clicking on a link or as intricate as wiring funds to a bank account.
Spear phishing lies under the umbrella category of phishing, however, spear phishing attacks usually target specific individuals rather than groups. These attacks will use specific information — like notices of current events, financial records or organizational happenings — to gain trust.
Whaling is a specific type of spear phishing attack. While spear phishing can target any individual, whaling targets high-value individuals who are more likely to have access to data or funds. Similar to spear phishing attacks, whaling attacks use tactical emails that are personalized to convince individuals to act. Whaling attackers will not send mass emails and may even use follow-up calls to appear more legitimate.
Phishing scams can be scary, and whaling attacks are a particularly sneaky kind. To keep your information secure, choose unique passwords and use a VPN to safely and securely browse the internet.





