Wardriving definition: Wardriving is the act of driving around with a laptop or mobile device to locate and map out unsecured or poorly secured Wi-Fi networks. Hackers often use this technique to exploit vulnerabilities in wireless networks for unauthorized access.
Wardriving originated in the early 2000s, evolving from the hacking portrayed in the film “WarGames,” where the main character dials random phone numbers to find connected computers. In 2001, this concept advanced into wardriving, where individuals map unsecured Wi-Fi networks to exploit vulnerabilities. Although wardriving itself is not illegal, the data obtained can lead to unauthorized access, which breaches privacy laws.
As of 2024, the average cost of a data breach in the U.S. reached $9.36 million. This figure reflects the increasing financial burden of cyberattacks, driven by factors like compromised sensitive data, legal fees and lost business. It makes detecting and preventing wardriving vital in order to secure networks against such widespread vulnerabilities. Learn everything about wardriving and how to avoid attacks.
What Is Wardriving?
Wardriving is a practice that involves driving around in a vehicle to scan for and map out wireless networks. The wardriving definition refers to the act of searching for and mapping out Wi-Fi networks using specialized equipment or software to identify their locations and signal strengths.
Wardrivers may intend to only find a single network or every network within an area. Once networks are located, wardrivers will record the locations of vulnerable networks and may submit the information to third-party websites and apps to create digital maps.
There are three primary reasons wardrivers look for unsecured Wi-Fi:
- To steal personal and banking information
- To use your network for criminal activity that you, as the owner of the network, would be liable for
- To find a network’s security flaws
But just like the dark web is not all bad, not all wardrivers act maliciously — ethical hackers use wardriving to find vulnerabilities so they can improve overall security.
What Is a Wardriving Attack?
A wardriving attack involves using wardriving techniques to exploit vulnerabilities in wireless networks. In essence, attackers use various tools and technologies to scan for and map out Wi-Fi networks in a specific area so they can identify unsecured or poorly secured networks — and exploit them!
Once the networks are identified, attackers might attempt to gain unauthorized access through various means, such as exploiting weak passwords or outdated encryption protocols. It can lead to a range of security breaches, from unauthorized access to sensitive information to potentially using the network for illegal activities. In more sophisticated attacks, the collected data can be used to plan more targeted and damaging intrusions.
How Wardriving Attacks Work
Wardriving on a small scale can be done with a simple app on a smartphone. Larger attacks, however, usually require an entire rig with software and hardware specifically designed for the attack.
Let’s explore the technologies involved to understand the different methods wardrivers use.
Wardriving Software
Wardriving software helps detect and log wireless networks. These programs scan for available Wi-Fi signals, recording details like network names, signal strengths and encryption types. Attackers can use this data to map out the network landscape and potentially identify vulnerable networks.
Wardriving Antenna
A wardriving antenna enhances the range and sensitivity of wireless network detection. By using a more powerful or directional antenna, wardrivers can detect networks from greater distances and in challenging environments, making it easier to locate and map networks that would otherwise be missed with standard equipment.
Bluetooth Wardriving
Bluetooth wardriving is a variation of the technique that focuses on detecting Bluetooth devices rather than Wi-Fi networks. It scans for Bluetooth signals to get information about nearby devices and their activities.
Raspberry Pi Wardriving
Raspberry Pi wardriving involves using a Raspberry Pi, a small and affordable computer, as the central unit for wardriving activities. By equipping it with appropriate software and antennas, users can create a versatile and portable wardriving setup.
Is Wardriving Illegal?
The legality of wardriving can differ based on local laws and the purpose behind the activity. In many places, simply scanning for wireless networks is not illegal, as it generally falls under the category of passive network discovery. However, the legality shifts if you use wardriving with malicious intent, such as attempting to access or exploit networks without permission.
In the United States, wardriving itself is not explicitly illegal under federal law. The primary legal issues stem from the Computer Fraud and Abuse Act (CFAA), which makes unauthorized access to computer systems and networks illegal. So if a hacker uses the gathered information to gain unauthorized access to a network, it would be a violation of CFAA.
It’s best to consult local laws and regulations regarding wardriving and network security, as legal interpretations can vary and penalties for unauthorized access can be severe.
How to Prevent Wardriving Attacks
Wardrivers typically engage in this type of hacking with criminal intent. While some wardriving practices are harmless, there’s also the potential for hackers to utilize your network to commit online crimes with the connection registered to you or steal personal data with the purpose of exploitation. In either case, it’s best practice to protect your Wi-Fi network from these types of breaches.
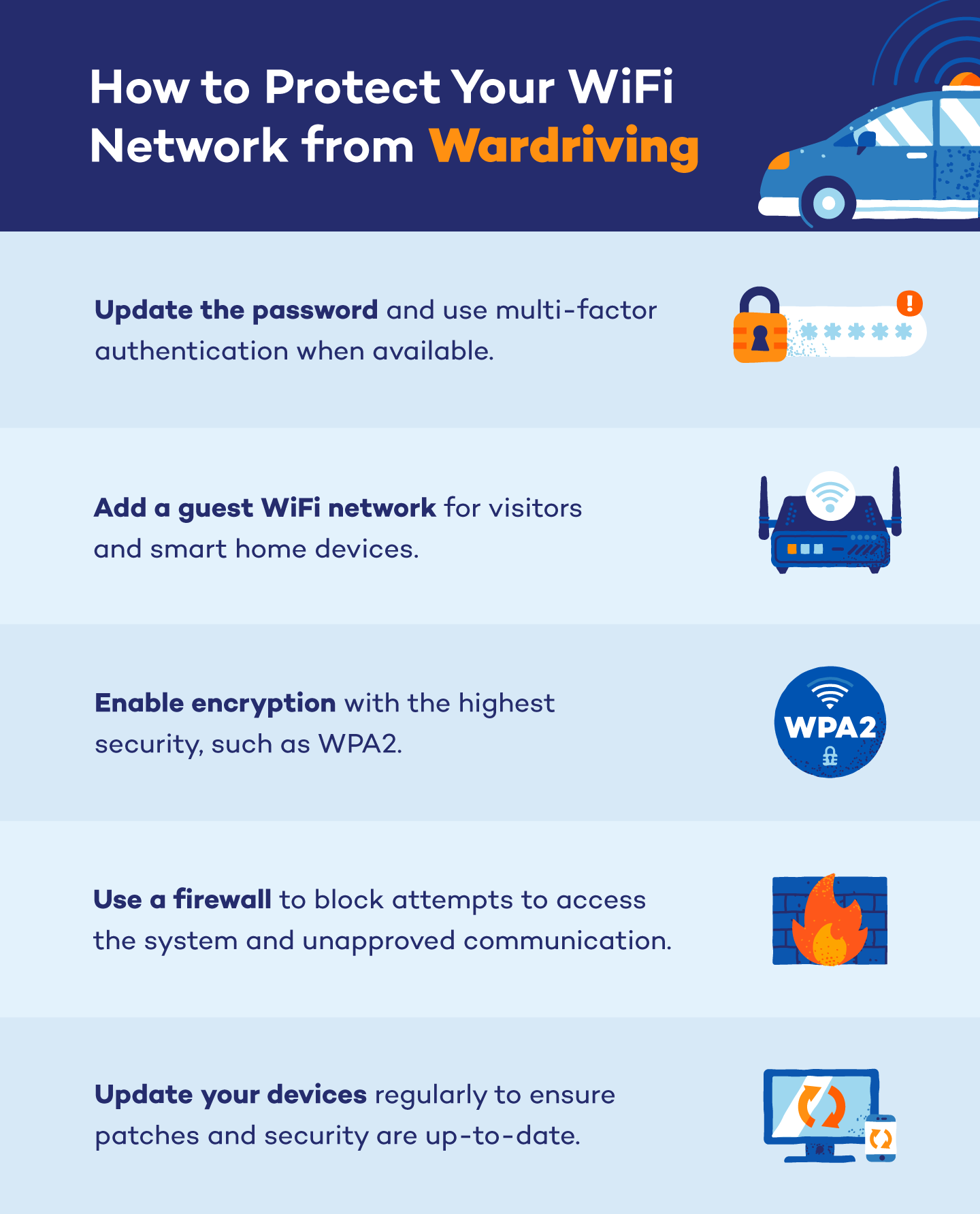
Follow these wardriving cybersecurity practices to stay safe:
- Enable encryption: Choose the highest network security protocol when opting for WEP, WPA and WPA2, and never leave your network open or without a security protocol.
- Update your password: Change the default password on your router and use multi-factor authentication when available.
- Add a guest network: Set up a guest Wi-Fi network for visitors and smart technologies that connect to the internet to limit the access of those less-secure devices.
- Use a firewall: Firewalls block unapproved communication and any attempts to access your system.
- Update your devices: Always install updates to ensure the most up-to-date patches and security on your hardware and software.
- Review your network settings: In addition to ensuring your router uses WPA3 encryption and has a strong password, make sure it doesn’t have unnecessary features like remote management disabled.
- Use a VPN: Encrypt your internet traffic and hide your IP address by using a reputable VPN service to secure your connection.
How Panda Security Helps Protect Against Wardriving Attacks
While wardriving is less common today than it was in 2001, the problem persists. Although ethical hackers use the process to find network vulnerabilities, there is still the possibility for the more dangerous alternative — those trying to exploit weaknesses to extract data or perform illegal activities. Always protect your devices using responsible digital habits, such as an efficient antivirus and the privacy of VPN software.
Wardriving FAQ
Still have doubts about wardriving? Here are answers to some common questions about this cyberthreat to help you understand it further.
Is Wardriving Illegal?
Wardriving itself is not necessarily illegal, but using the information gathered for unauthorized access or malicious purposes can be a violation of laws like the Computer Fraud and Abuse Act (CFAA) in the U.S. or privacy regulations in the EU.
What Does a Wardriver Do?
A wardriver scans for and maps out wireless networks using specialized tools to gather information about network locations, signal strengths and security configurations.
What Is Warchalking?
Warchalking is a method used to mark locations with symbols to indicate the presence and security status of wireless networks, similar to how wardrivers map network locations.
Is Wardriving a Type of Wireless Piggybacking?
Wardriving is not exactly the same as wireless piggybacking, though they are related. Wardriving is all about scanning and mapping wireless networks, while wireless piggybacking refers to unauthorized access and use of those networks. Wardriving can lead to piggybacking by identifying vulnerable networks.







