Quick answer: A vulnerability assessment reviews and assesses the risks of security weaknesses in an organization’s information and security systems.
There are more than 180,000 known security vulnerabilities, and more are discovered each year. With so many possibilities for infrastructure weakness and system attacks, it’s no surprise that cybercrime has increased significantly in the past few years. When conducted regularly and correctly, vulnerability assessments can act as a preventative measure against these increasing security threats.
Even with premium security defenses, an organization’s information and security systems can be attacked, hacked or hijacked by cybercriminals. Our guide will show you why it’s important to invest in vulnerability assessments, how they work and their different functions.
What is a Vulnerability Assessment?
A vulnerability assessment refers to the process of reviewing and assessing all the possible security weaknesses in the infrastructure of an information system. This type of assessment is used to identify vulnerabilities and then prioritize and mitigate them to minimize security threats. These assessments also uncover and understand vulnerabilities within an organization’s physical environment. The objectives of a vulnerability assessment can be broken down into three main ideas:
- Identify all vulnerabilities
- Document vulnerabilities for future identification and solutions
- Provide guidance for developers creating threat solutions
Vulnerability assessments should be performed regularly, especially when new equipment is installed, ports are added or services are introduced. Additionally, vulnerability assessments can prevent system attacks on new and old devices due to threats like:
- Injection attacks, including XSS attacks and SQL attacks
- Weak default settings like guessable administration passwords and usernames
- Malware and malware attacks
- Faulty authentication tools and devices
- Unencrypted data
For at-risk organizations — including banks, government systems, and those with access to personal information, like healthcare facilities — vulnerability assessments can help identify and reduce weaknesses before they are exploited by hackers.
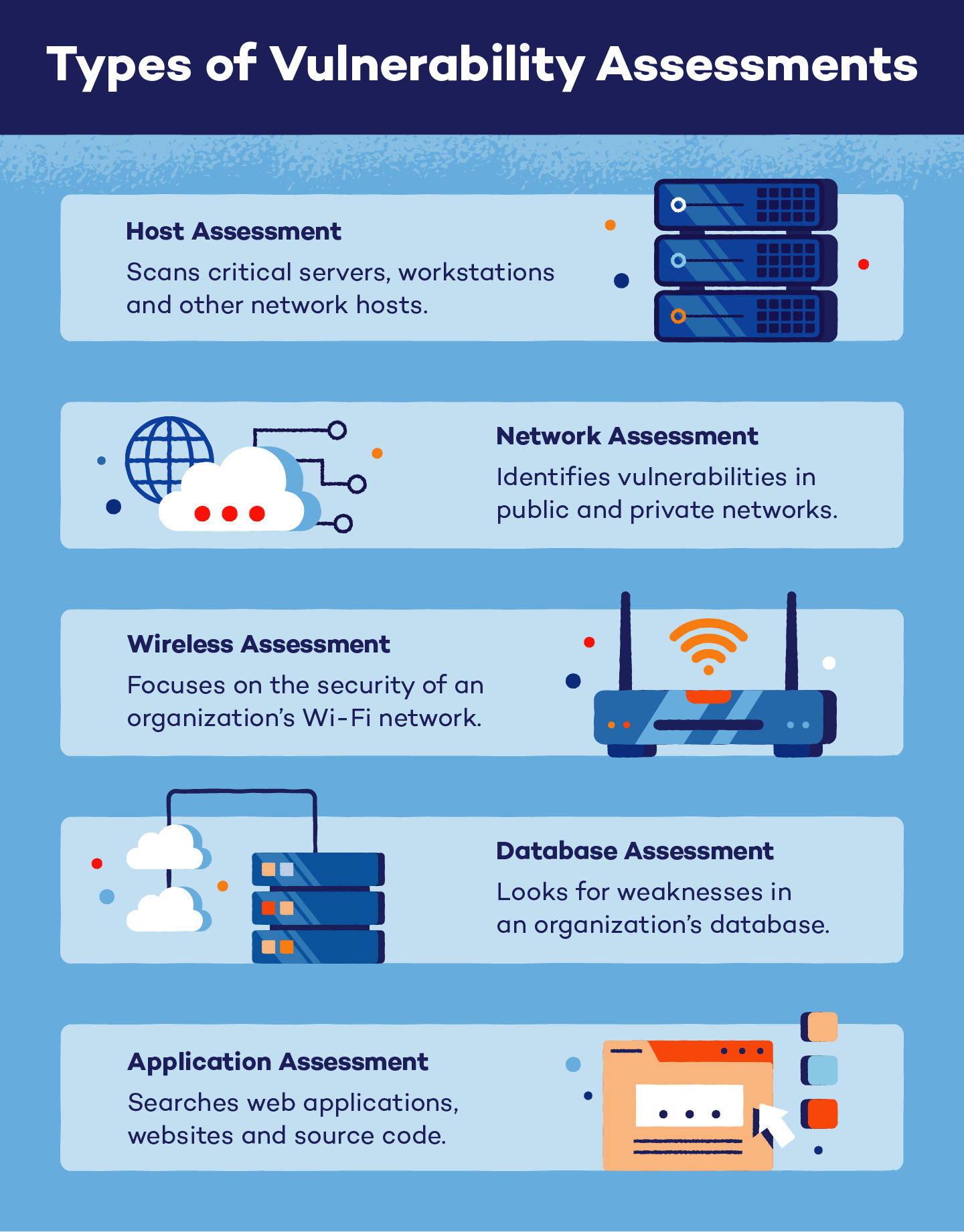
Types of Vulnerability Assessments
Different types of vulnerability assessments use individual tools to identify system and network weaknesses. Independent systems may need to use a variety of assessments in order to identify all their possible vulnerabilities.
Host Assessments
A host assessment focuses on critical servers, workstations and other network hosts. Although ports and services may be scannable with network assessments, a host assessment is able to highlight past patch history and the host’s settings.
Network Assessments
A network assessment is used to identify possible network vulnerabilities. These can be performed for both wired and wireless networks. These assessments help prevent security attacks that target private and public networks as well as network-accessible information.
Wireless Assessments
The focus of a wireless assessment is an organization’s Wi-Fi network. Insecure wireless networks, including those with rogue access points, can lead to attacks on an organization’s infrastructure. These assessments also verify that an organization’s network is securely set up with HTTPS.
Database Assessments
Database assessments scan an organization’s database for vulnerabilities. Malicious attacks, like SQL injections, target databases with misconfigurations, rogue databases and weak development testing (DevTest). These assessments also help organizations identify where personal information across an infrastructure needs to be classified.
Application Assessments
An application assessment scans web applications, websites and source code for incorrect software downloads, broken configurations and other security vulnerabilities. These are often automated scans for front-end code and infrastructure.
Vulnerability Assessment vs. Penetration Test
Vulnerability assessments and penetration tests are not the same, but because vulnerability assessments can also include a penetration test, they can easily be confused. These dual assessments are often known as vulnerability assessment/penetration tests or VAPTs, but these tests do not need to be performed together every time.
Penetration testing is specifically used to find weaknesses in an organization’s personnel and procedures, and it is an additional process that can be added to a vulnerability assessment. Penetration testing also attempts to damage an application or network by exploiting possible weaknesses in a controlled environment in order to prove that vulnerabilities actually exist.
Penetration testing uses both automatic and manual maneuvers when testing vulnerabilities. These weaknesses are then analyzed by researchers so specific protections and defenses can be created. However, penetration testing is not sufficient on its own and should be followed up with a full vulnerability assessment.
| Vulnerability Assessment | Penetration Tests |
|---|---|
| Usually uses automated techniques | Uses both automated and manual techniques |
| Can be performed without a penetration test | Should be followed up by a vulnerability assessment |
| Identifies weaknesses | Exploits weaknesses |
| Focuses on network and system scans | Focuses on personnel and procedure scans |
| Automatic remediation report | Manual prevention and defense report |
Performing a Vulnerability Assessment: 4 Stages of Identifying Vulnerabilities
If you are performing a vulnerability assessment without a penetration test, there are four main stages.
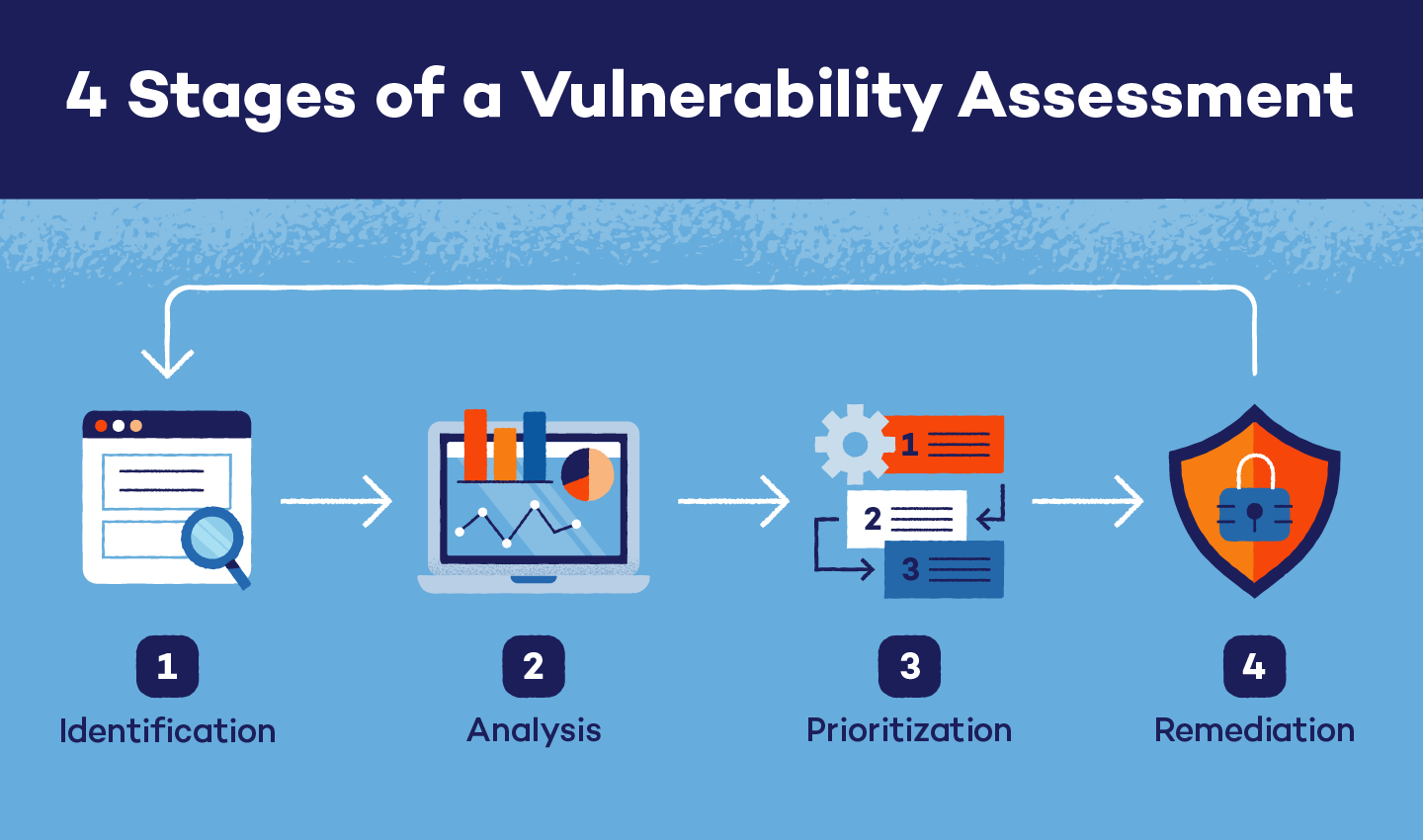
1. Asset and Vulnerability Identification
Identification is the first stage when performing a vulnerability assessment. Before beginning a scan, you need to identify your scannable assets, including popular tools like mobile devices, Internet of Things devices and cloud-based programs. Then, your infrastructure is scanned by automated tools or manually by security analysts. A vulnerability assessment report is populated and it outlines the identified weaknesses.
2. Analysis
In the analysis stage of a vulnerability assessment, the goal is to find the source and cause of each weakness. In order to identify the root cause, the components of the infrastructure that are responsible for each vulnerability must be verified and further analyzed. The analysis stage also checks for improperly installed or updated systems.
Vulnerability scanners — and their integrated databases of known vulnerabilities — can pinpoint possible system weaknesses, vulnerable devices and at-risk software to help complete this stage. Because many vulnerabilities are publicly reported, they can be quickly identified and their root cause analyzed.
3. Risk Assessment and Prioritization
After you have identified and analyzed your organization’s vulnerabilities, it’s time to conduct a risk assessment and determine prioritization. Your first stage should have provided assessment reports, which can then be used to determine which vulnerabilities are most dangerous to an organization.
During a risk assessment, security analysts assign each vulnerability a severity score, and higher numbers indicate weaknesses that should be addressed as soon as possible. Vulnerabilities are ranked based on a variety of factors, including:
- The systems affected
- The information put at risk
- Ease of attack or compromise
- Potential infrastructure and organizational damage
4. Remediation and Mitigation
The final stage when performing a vulnerability assessment is remediation and mitigation. This stage is usually performed by security professionals and operations teams, and it is dedicated to finding ways to alleviate weaknesses while developing plans to decrease the chance of reappearing vulnerabilities. While creating remediation and mitigation plans, professionals should focus on two factors:
- Severity: After prioritization, teams should address the most severe vulnerabilities first. Eventually, teams should be able to create and release fixes for each vulnerability detected, but early remediation centers around the most dangerous weaknesses.
- Vulnerability Exposure: Determining if a vulnerability is public-facing or internet-facing should also be a main concern for remediation professionals. Internet-facing vulnerabilities are easier for cybercriminals to reach, so these weaknesses should be mitigated first followed by employee-owned devices and those storing sensitive information.
If system patches or vulnerability fixes are released, the vulnerability assessment process should begin again. It is important to run an assessment when any type of new system or patch is installed in order to quickly identify, analyze, prioritize and remedy any new vulnerabilities.
Vulnerability Assessment Tools
Frequently, vulnerability assessment tools are automated processes that can be used by anyone from cybersecurity experts and threat hunters to the at-home worker. These tools scan systems for existing vulnerabilities and new, unreported weaknesses. Plus, each assessment tool has a specific purpose based on the type of assessment it is meant to perform.
Types of vulnerability assessment tools:
- Web application scanners
- Protocol scanners
- Network scanners
- External and internal vulnerability scanners
- Environmental scanners
In addition to the type of assessment each tool performs, they have their own features that a user needs to consider. When you’re choosing an assessment tool, keep these in mind:
- Frequency of updates
- Ability to minimize false positives and negatives
- Integration capacity with other assessment and security tools
- Actionable results
While vulnerability assessments are a necessary part of the cybersecurity process, there are additional precautions you can take to keep your infrastructure protected. Investing in a VPN can help protect your public and private network browsing, while an antivirus can help keep both mobile and static devices secure.





