A social media threat involves malicious activities targeting users through social platforms, such as phishing scams or identity theft. Attackers may impersonate legitimate contacts or companies to gain access to your personal information or spread harmful content.
Social networks provide a space for people to interact, learn from each other and share bits and pieces of their life. While there’s little limit to what is shared online, sharing too much information can lead to harmful consequences.
Social media threats are found on any social network, so you should be aware of what they are and what they look like to avoid them. One in four individuals who lost money to fraud since 2021 reported that it began on social media. These scams affect the privacy of your account, making it important to take security precautions to protect yourself and your personal data.
Learn more about different social media attacks and threats and how to be a safer social media user.
What Is a Social Media Threat?
A social media threat encompasses actions that jeopardize an individual’s or organization’s social media account. As many social media users post or share personal details online, attackers can easily use this information to exploit or blackmail them.
These threats emerge in different forms, including impersonations, online harassment and malware. Below are some of the most common threats on social media that attackers use to gain access to your information.

1. Identity Theft
Identity theft is a common social media threat that can happen to anyone who shares images or personal information online. Impersonation happens when someone uses public information and pictures to create a fake online profile and either pretend they are that person or create a new persona entirely.
Identity theft is extremely harmful if the impersonator gains access to your bank accounts or tricks others into sending them money. It also includes gaining access to your social media accounts and posting content to scam sites, which puts other users at risk of being taken advantage of.
2. Cyberbullying
Sixty-seven percent of internet users have seen hate speech online, with 74% under 35 years old. Cyberbullying includes harmful and damaging posts, messages or content shared either directly to a user or publicly. It can also happen anonymously.
To better protect yourself against online harassment and other social media cyberattacks, keep your account in private mode and be selective of your online followers or friends. Report instances of cyberbullying to the social media platform to get any malicious posts flagged and removed.
Many social networks, like Instagram, have community guidelines in place that have a no-tolerance policy for actions that fall under the cyberbullying umbrella.
3. Fake Giveaways
Many brands are turning to social networks to promote their products and services. Giveaways are cost-effective and reach a wider audience with promoted posts.
To grow awareness, brands often promote giveaways of their products to followers. According to Easypromos, nearly 93% of brands surveyed run giveaways on their social networks to gain more traffic and clicks to their site.
While these giveaways may seem too good to be true, sometimes they really are. Scammers will create fake brand profiles that promote giveaways for followers to enter and submit their personal information. Since October 2017, Facebook has deleted 27.67 billion fake accounts.
4. Likejacking
Likejacking is a crafty social media security risk that hackers use to force users to click the “like” button on a post or page without them knowing they did it.
For instance, you might see an interesting image or video that requires you to click on it to view more information. What you don’t know is that the scammers hid a “like” button behind the image or video so you can’t see it. You’ll then start seeing more of these images pop up and overload your social feeds.
5. Phishing Scams
Phishing is a method scammers use to collect personal information through online messages, emails, links and spoofed websites. These messages appear to be sent by a professional company or trusted source, like a bank or credit card company.
Hackers send phishing messages to trick you into sending over contact information like password details or credit card account information. These messages may contain malicious links that can give hackers access to your devices or infect them with a virus.
Never reply to these types of messages or click suspicious links unless you requested the link or recognize the phone number or email address they come from. For example, check your bank’s customer service phone number or email to make sure it matches. Contact customer service directly to confirm they sent the message to you.
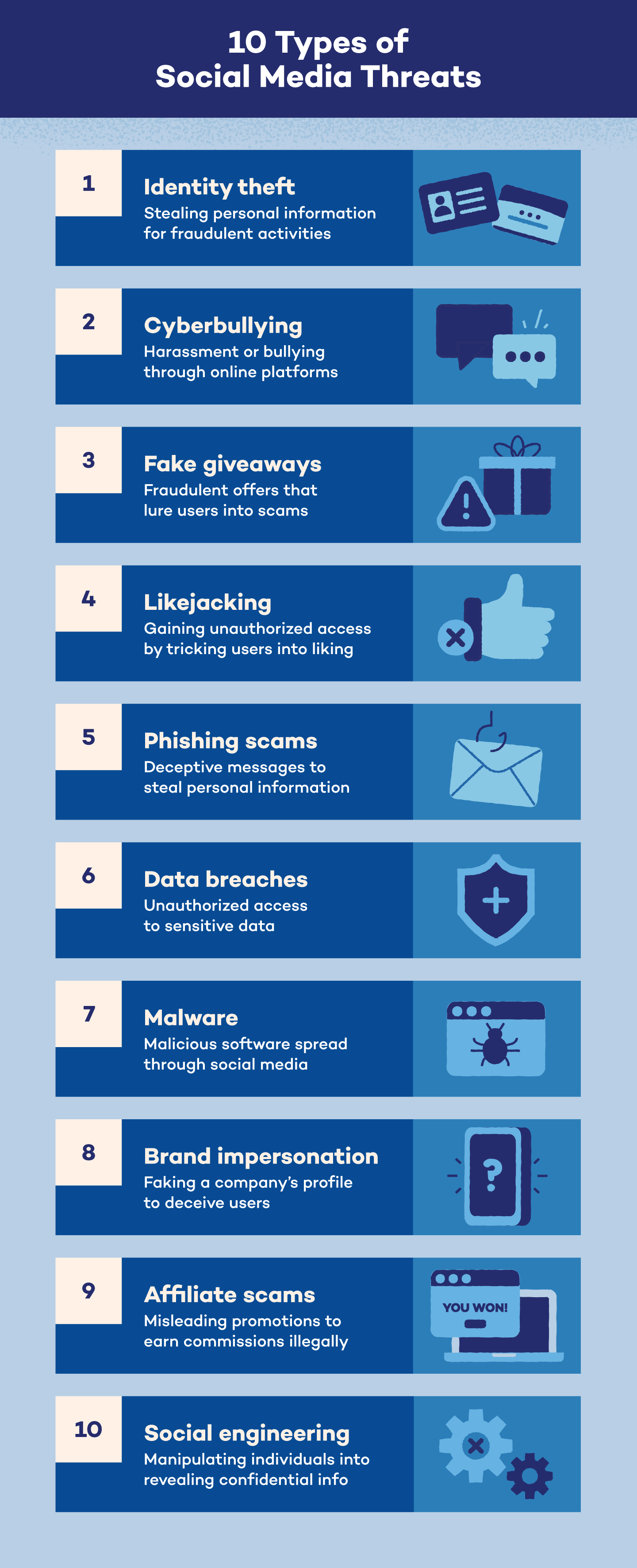
6. Data Breaches
A data breach is a harmful cyberattack that occurs when a hacker gains access to confidential information. Data breaches can affect any size or type of organization or business — the NPD breach in August 2024 compromised 2.9 billion records.
For individuals, this includes access to Social Security numbers, credit card accounts and health care information. For larger organizations, this can include client lists or employee health information.
If someone accesses these types of data illegally, the target organization may face serious legal trouble. If the data breach causes a violation of any compliance mandates, the affected organization could receive fines and litigation. Depending on the severity of the breach, the company could even lose the right to operate.
7. Malware
Malware is designed as a code or file that transfers over to a user’s computer to infect it or steal personal information.
Malware pops up in all forms, but it’s especially popular to use with fake news posts or videos. The scammer’s goal is for the user to click on the falsified news story, which is riddled with a malware virus that can compromise the user’s device or social media account.
Malware can also show up in fake websites or domains. You may be asked to download a file to access the site, but the file is actually malware, and by downloading it you’ve given the virus (and the person who created it) access to your device.
For example, let’s say a site has a video that “requires” a software update to view it. Double-check that the site is legitimate before downloading anything. If you’re not sure, it’s best to leave the site to avoid any possibility of malware.
8. Brand Impersonation
Not even brands are safe from social media threats. Scammers might create a social media account to impersonate a brand and contact customers under the guise that they are a legitimate company.
The attacker’s goal is to either receive personal information from recipients, like account login details, or share messages that harm the brand’s reputation.
9. Affiliate Scams
Some companies create affiliate programs to contract social media influencers to post content about the company, and in return earn commission on products or services they sell through their affiliate link.
Companies use affiliate marketing to drive traffic to their website and earn revenue. However, you will likely come across affiliate marketing content that isn’t real.
Scammers may post content that appears to be an advertisement offering a free gift card, requiring you to enter your personal email address to receive it. But instead of receiving the gift card, you get an unending amount of spam emails, some of which may even contain malware.
10. Social Engineering
Social engineering is a tactic cybercriminals use to manipulate individuals into divulging confidential information. In the context of social media, attackers might pose as legitimate employees or internal contacts within the company. They often craft convincing stories or use fake identities to gain the trust of actual employees.
Once they’ve established credibility, they’ll request sensitive personal information about you, such as login credentials or contact details. This type of deception can lead to unauthorized access to user accounts, personal data breaches and further exploitation of both the company and its users.
How Do Social Media Threats Occur?
Social media cybersecurity threats occur when a user’s personal information and details are accessed online by hackers and scammers. Fraudsters tend to attack accounts that have little security and users who aren’t aware of the dangers of cyberattacks.
Hackers often use tactics like social engineering, manipulating you into clicking harmful links or revealing personal data. Additionally, weak passwords or lack of two-factor authentication make accounts easy targets. Once inside, attackers can steal data, spread false information or use the account for malicious activities.
How Do You Prevent Social Media Threats?
The best way to prevent social media risks from knocking on your digital door is by knowing how to spot them and being proactive about your online safety. Below are a few ways to ward off social media threats:
- Ad blockers: Most organizations recommend or request that employees use ad blockers online, and it’s a good idea outside of work, too. Ad blockers eliminate random pop-ups that could contain malware.
- Filter friend requests: Never accept a friend request from someone you don’t know, even if you have mutual friends. It’s one of the best ways to avoid social media threats of violence like cyberbullying.
- Update passwords frequently: Updating your login credentials regularly and choosing strong passwords will decrease the chances of a hacker figuring out your password. With that, never share your passwords with anyone.
It’s also best practice to keep educating yourself and others about online threats and scams, as attackers constantly update their tactics to keep tricking unsuspecting users.
Be cautious about clicking on suspicious links, even if they come from friends. Cybercriminals often hack accounts and send messages that appear to be from trusted contacts. These messages may or may not seem unusual or out of character, so it’s important to verify with the friend directly before clicking on any links or downloading attachments. This simple step can help protect against falling victim to scams or malware.

6 Tips for Using Social Networks Safely
Whether you touch base on social media periodically or use it every day, it’s important to practice safe online habits and protect yourself from hackers and spammers. Below are several tips to better protect yourself, your kids and your devices.
1. Install a Security Solution
Install a security solution, like antivirus software, with proactive technologies on the computer. You’ll be protected against malicious codes that spread through these networks, even if no previous attack has been launched.
2. Keep Your Computer Up-to-Date
Users must be aware of and resolve all the vulnerabilities that affect the programs installed on the computer.
Keep up with software updates for your internet browser and other programs on your computer. These updates include security fixes to keep hackers from accessing your information. Some programs even offer the option of automatic updates if you tend to forget.
3. Don’t Share Confidential Information
If you access forums and chats to exchange information, talk, etc., remember not to provide confidential information like email addresses or login credentials.
If you do accidentally share login information, immediately update it with a strong password to avoid someone signing in to your account. Update your passwords regularly for the best protection.
4. Teach Children About Social Media
Children must know what information they shouldn’t share. That means parents must know the social networks their children access and teach them how to safely engage.
Promoting open communication about using social media can help your child feel more comfortable. Be open to their questions and concerns, and discuss how to have a healthy relationship with social networks.
5. Only Provide Necessary Information in Your Profile
When creating user profiles, only provide the information necessary. If it requests private data like an email address or age, choose the private profile mode to prevent other users from seeing the information, to ensure no users other than yourself and the administrator access your data.
6. Report Crimes
If you observe inappropriate or criminal behavior (like attempts to contact children, inappropriate photos, modified profiles, etc.), you must inform the social network administrators.
Improve Your Social Media Security With Panda Security
Online protection is important to us, and that’s why Panda Security provides cybersecurity services and tools that are used to prevent cyberattacks and threats to your devices. Panda Security’s antivirus software not only protects against viruses but also protects your data, passwords and browsing history.







1 comment
Great article! Social media threats are definitely a growing concern in today’s digital age. It’s crucial for users to be aware of the potential risks and take proactive measures to protect themselves and their personal information.
The section on phishing attacks was particularly informative. Phishing has become increasingly sophisticated, and it’s alarming how easily users can be tricked into revealing sensitive data. The tips provided, such as being cautious of suspicious links and verifying the authenticity of emails and messages, are essential reminders for everyone using social media platforms.
I also appreciate the emphasis on strong passwords and the importance of regularly updating them. Many people underestimate the significance of a secure password and tend to reuse the same weak passwords across multiple accounts, which puts them at a higher risk of being compromised. The suggestion of using a password manager to generate and manage complex passwords is an excellent recommendation.