As cloud-based enterprises and remote workers continue to grow in popularity, the need to implement zero-trust security models has never been more relevant. But what is zero trust security?
In short, zero trust security is a model founded on the assumption that no user or device can be trusted and must be verified — including internal and external users and devices. Because 82% of cyber breaches occur due to some type of human error or misuse, this type of security model helps ensure that only authorized personnel are permitted to access information systems of all types.
Our complete guide to zero trust security will help you enhance your security and protect your data — even with protection services like VPNs already in place.
What is Zero Trust Security?
Zero trust security is a cybersecurity framework for enterprise organizations that allows account-based network access to authorized and authenticated users only. It is also referred to as zero trust architecture or zero trust network access.
The main tenant of the zero trust framework is that any user, device or system cannot be trusted by default. To access enterprise data, a user must be authenticated and approved by a verified trust broker. Access is granted with a least-privelege approach, meaning users are given the least level of access needed to accomplish tasks.
A zero-trust approach to security includes:
- Users: includes authentication of user access, least-privilege policies, and user integrity verification
- Applications: removes implicit trust and implements continuous monitoring
- Infrastructure: all infrastructure pieces — including routers, cloud-based systems, Internet of Things models, and more — must abide by a zero-trust model.
Why Is Zero Trust Important?
Zero trust is important because it can add value and improve security capabilities regardless of an organization’s network setup.
Although zero trust can be used in any network setup, it is particularly valuable for organizations and networks that are cloud-based or rely on remote work. Many of these types of enterprise organizations originally used firewalls and VPN-protected network access, but login credentials could be compromised or hacked.
With zero trust, this is nearly impossible. Some of the benefits of a zero trust security network include:
- Increased security
- Reduced entry point opportunities for data breaches
- Efficient troubleshooting opportunities
- Native scaling abilities found in cloud-based networks
- Efficient data-sharing capabilities
Without a zero-trust network, organizations may be at risk of dangerous cyberattacks led by unauthorized hackers.
How Does Zero Trust Work?
First and foremost, zero trust operates under the assumption that every system connection and endpoint is a threat. This causes a zero trust network to:
- Log and inspect all internal and external traffic
- Control attempted access to networks
- Keep network resources secure
- Verify all sources and resources
With no network perimeter, users are required to authenticate their identity before they are offered granular access. However, unlike VPNs and internet-based cloud access, zero trust does not grant access to all data – it only grants access to data needed for that particular user to complete their task.
This means that access is only permitted:
- On a limited basis
- Under the right circumstances
- After authentication is approved
This type of access is referred to as least-privilege access, and it occurs for every connection — even if prior access was granted. Additionally, authorization is approved or disproved based on an organization’s static and dynamic security policies.
If an organization is interested in adopting a zero-trust model, it must agree to:
- Implement the model across the organization
- Assign access rights based on roles
- Establish security policies for authorization
- Identify vulnerabilities
- Segment networks to prevent breach movement
- Protect virtual workloads
Once an organization has agreed to and implemented these expectations, it can move forward with installing and utilizing zero trust security.
What Are The Principles of Zero Trust Security?
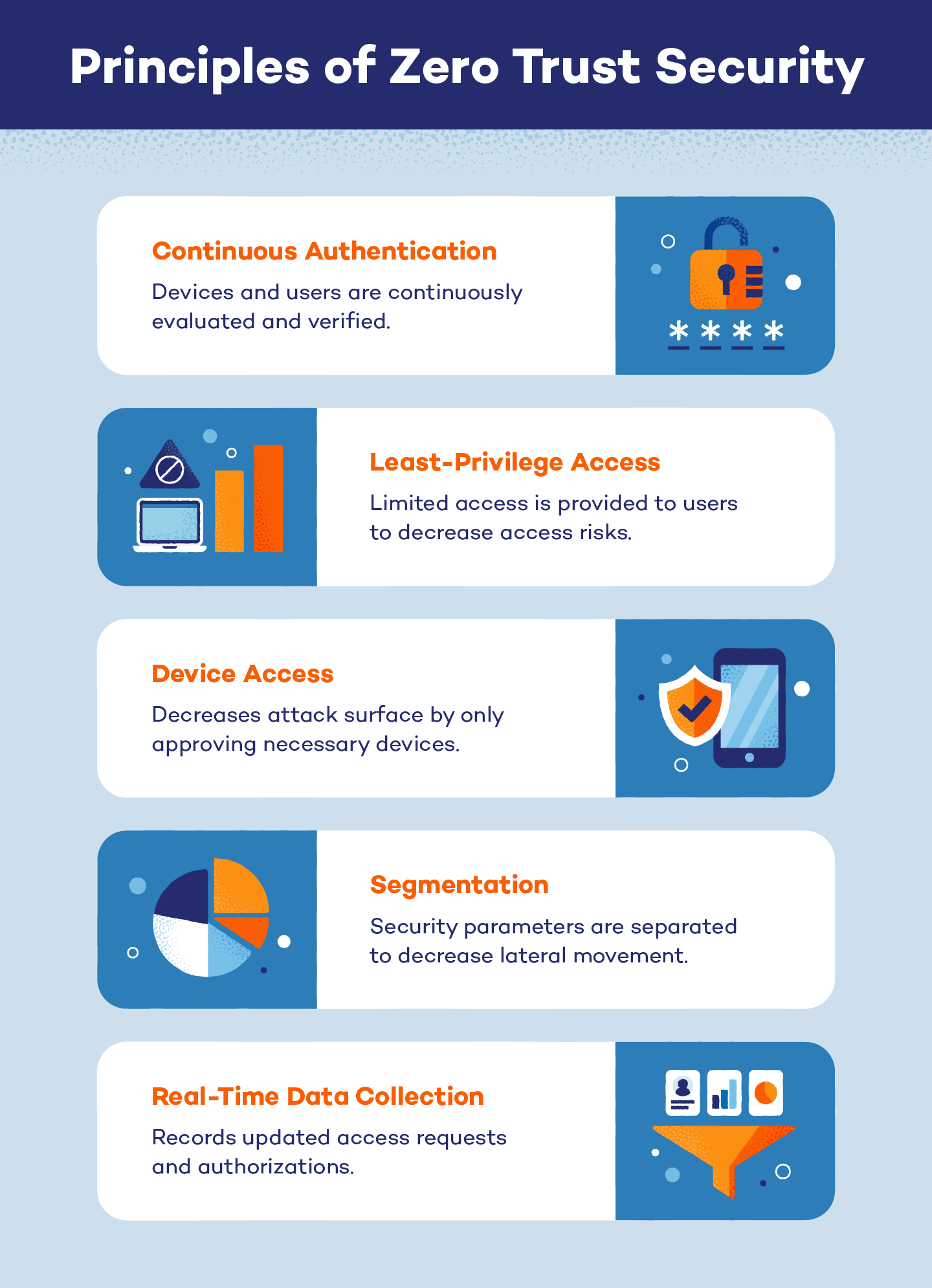
Because zero trust security operates under the assumption that every internal and external user is a threat, five core principles govern the model’s success.
1. Continuous Authentication
Even if a user or device has previously been authenticated by a system, it must continue to undergo evaluation each time it attempts to access a system. Additionally, many zero trust models choose to use multi-factor authentication (MFA) where users and devices must prove their identity using multiple pieces of evidence.
2. Least-Privilege Access
When users are authenticated and granted system access, least-privilege access only provides them with the amount of access they need to successfully complete a task. This lowers the probability of an unauthorized user accessing sensitive information or complex system processes.
3. Device Access
Zero trust systems also control the access a device is granted. By controlling the number of devices attempting to access a system, authenticating only necessary devices and assessing the health of each, a system’s attack surface is minimized.
4. Segmentation
To prevent hackers from moving laterally across a network, zero-trust models implement segmentation. Segmentation separates a system’s security perimeters into smaller zones, forcing users to receive system access and authorization for each perimeter they wish to cross.
5. Real-Time Data Collection
Because the zero trust model requires continual authorization, it is constantly receiving real-time data. This allows the system to stay up-to-date with authorizations and access requests, limiting and eliminating saved authorizations.
Zero Trust Use Cases
The popularity of the zero-trust security model continues to grow as cloud-based applications and the need for remote organizational access also grow. However, zero trust security may not be necessary for every business or system.
A few common, zero-trust use cases include:
- Teams with requests for secure third-party access
- Teams requesting remote cloud access
- Internet of Things security
- Datacenter and systems segmentation
Additionally, zero trust security is required for systems with:
- Multi-cloud models
- Unmanned devices
- Legacy systems
- SaaS applications
These systems risk being attacked by ransomware or internal threats, which can be combatted or dissolved with zero-trust architecture in place.
How To Implement Zero Trust
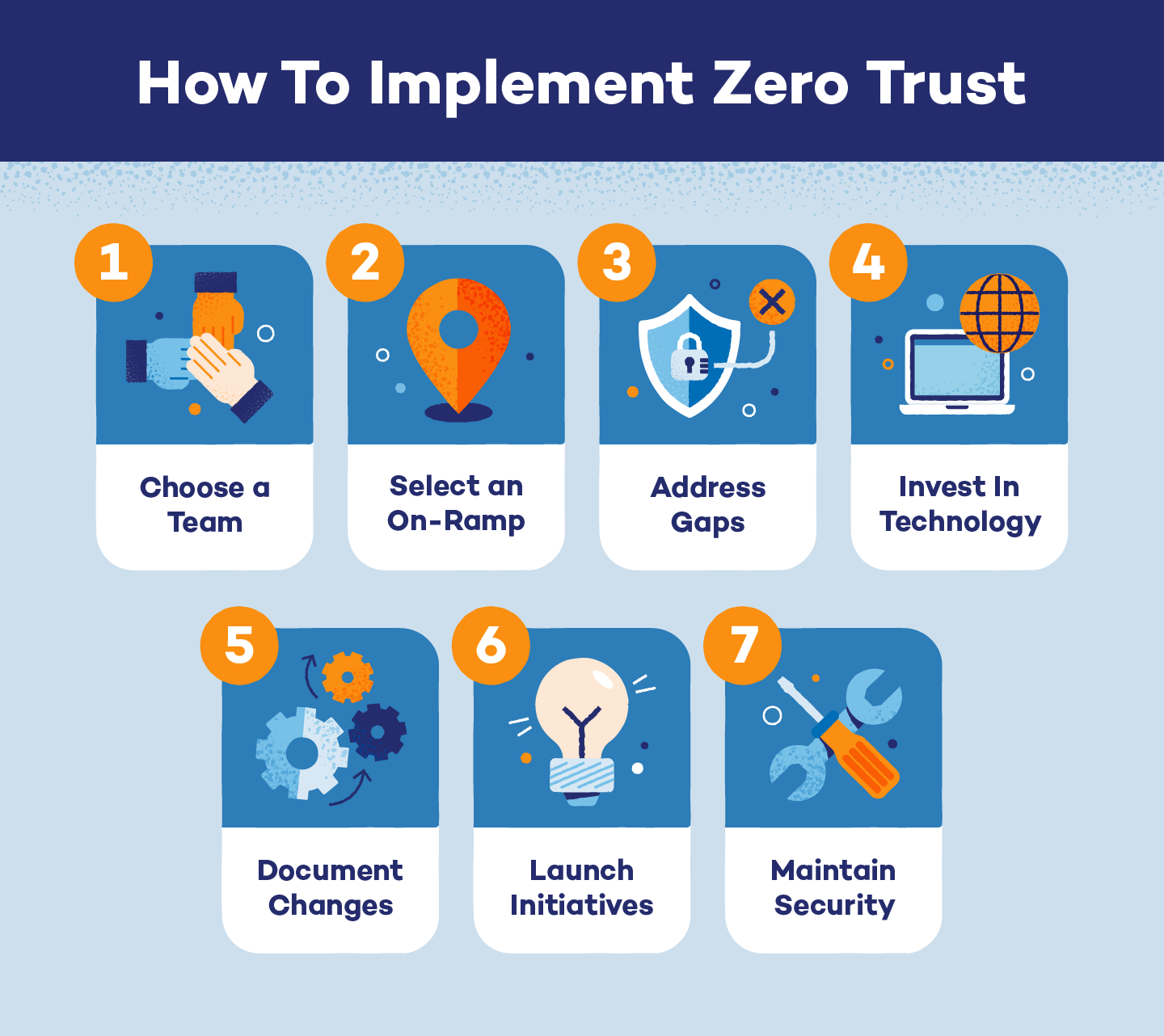
If you’re considering implementing a zero-trust security model within your organization, there are some important steps you need to take.
- Create a zero-trust team. This team will educate your organization and themselves on updated zero-trust news and technology. They will also help implement and upkeep your model.
- Select an on-ramp. These on-ramps for launch include user and device identity, applications and data, and the network itself.
- Assess and address security gaps. Your organization may have some zero trust security controls already in place. Assess where they are missing and fill them in accordingly.
- Invest in technology. If your systems are not designed for zero trust security, you may need to invest in new technologies to support your new security system.
- Document necessary operations changes. Modification and automation of processes should be documented and implemented, along with changes to necessary personnel.
- Launch initiatives. Launch your zero-trust security model for your organization.
- Maintain security. Identify where gaps still exist, what process could be updated and implement any changes to help maintain your new security model.
With security designed for all devices and operating systems, Panda Security helps protect more than 30 million users daily — including those with a zero-trust security model in place. Even after asking “What is zero trust security?”, keep your infrastructure systems protected from cyber threats with comprehensive antivirus software.





