Whether you’re a remote worker who thrives in coffee shops or simply need a quick internet fix while you’re out, finding free Wi-Fi can be a lifesaver. It can also be a challenge, especially when traveling to unfamiliar places. The good news is that there are a number of ways you can find a free Wi-Fi connection anywhere.
In this post, we’ll explore a variety of methods, including Wi-Fi finder apps, how to use your phone as a hotspot, using a portable router and more to help you find free Wi-Fi anywhere you go.
1. Find Somewhere With Public Wi-Fi

When you’re on the go, free Wi-Fi can make life easier. Here are a few ways to find a free connection:
- Chain businesses: Many restaurants and hotel chains around the world offer free guest Wi-Fi for their customers. The login process is usually simple, with a quick login page or occasional ads. Some chains might ask for an email address. It’s best to use a separate email address for these situations to keep your email clean and free from any promotional emails.
- For example: Apple Store, Macy’s, Best Buy, Target
- Public establishments: Public libraries are a classic free Wi-Fi resource, but many other shared spaces offer connections as well.
- For example: Public libraries, metro stations, bus terminals, museums

- Find Wi-Fi in your city: Many large cities offer free Wi-Fi within a designated central area. You can check the city’s website or tourism board for the exact location where you can find free Wi-Fi.
- For example: Malmö, Sweden; Tel Aviv, Israel; New York City, USA; Bangalore, India
Pro tip: Loyalty programs are great ways to connect to free Wi-Fi when password-free connections are not available. Hotels like Hilton give free Wi-Fi to those who sign up for Hilton Honors Rewards, a free service that offers discounts and a points system for members.
2. Use Your Phone as a Hotspot
When in doubt, you can always use your phone as a hotspot device (also known as tethering), although this may be a costly choice unless you have an unlimited data plan. Some carriers have restrictions or fees associated with tethering, like only being able to use a certain amount of data, so be sure to check with your provider.
We’ll walk you through how to set up your mobile hotspot for both Android and iPhone.
Setting up a Wi-Fi hotspot on an Android phone:
Note: We used a Google Pixel 6 Pro for this example.
Step 1: Open your phone’s settings.
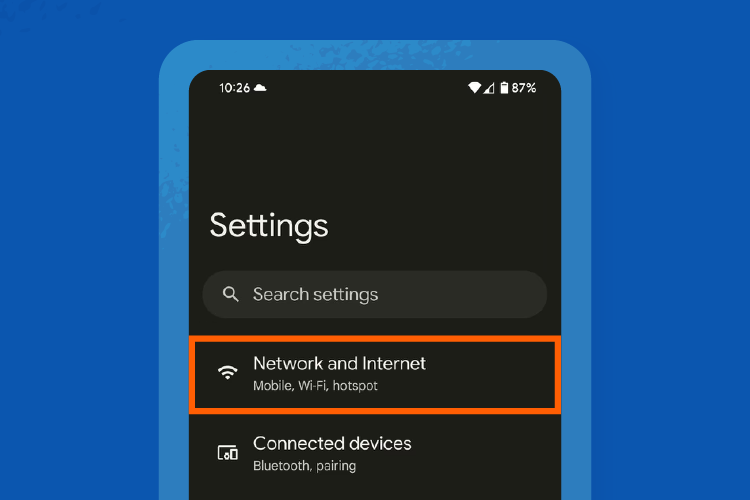
Step 2: Click on Network and Internet.
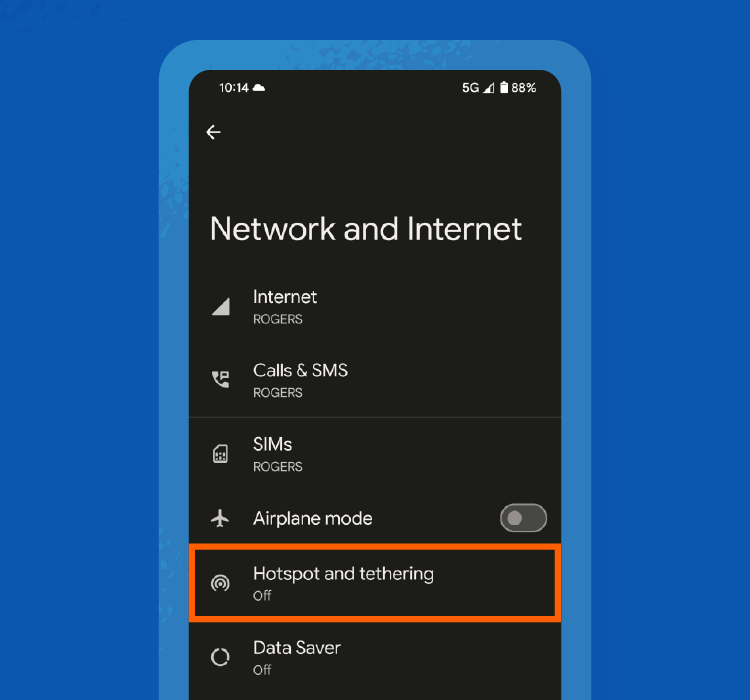
Step 3: Click on Hotspot and tethering.
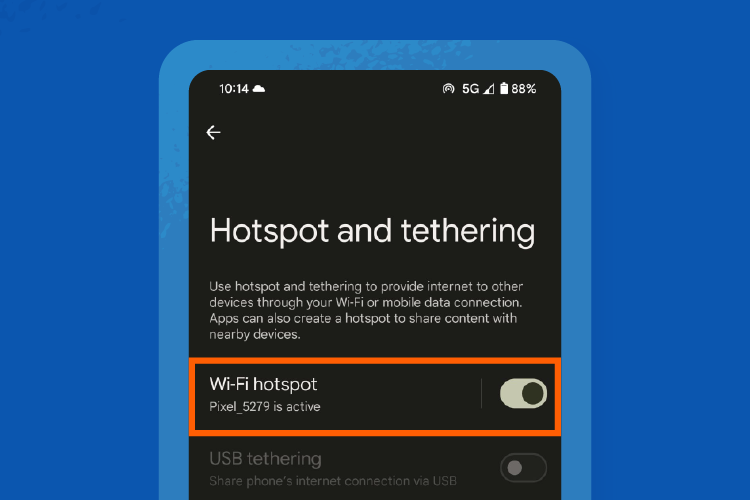
Step 4: Turn on Wi-Fi hotspot.
Step 5: Go to your computer’s Wi-Fi settings and find the list of available Wi-Fi networks. You’ll see the mobile hotspot you want to connect to. In this case, we’ll connect to Pixel_5279 on an iMac.
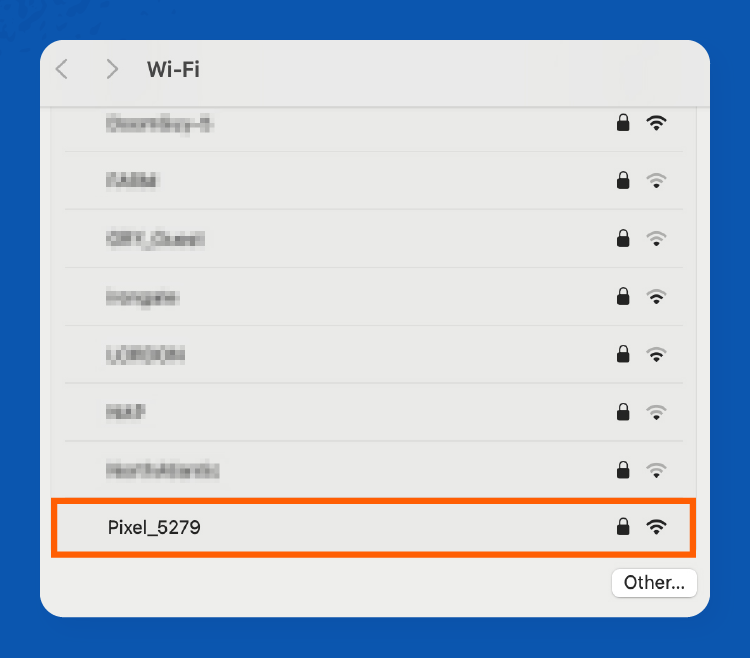
Step 6: Click on Wi-Fi hotspot on your phone settings, and you’ll see the password. Enter the hotspot password on your computer.
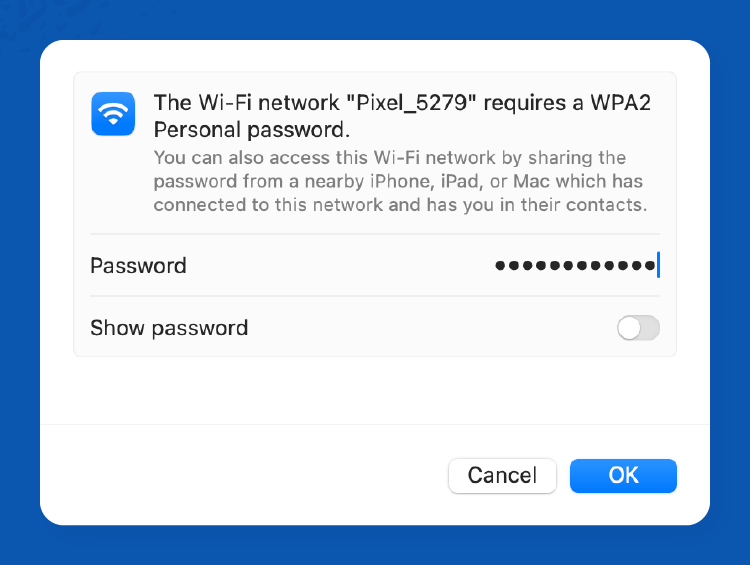
Step 7: Once you enter the password and click OK, you’ll be connected to the mobile hotspot and all set to browse!
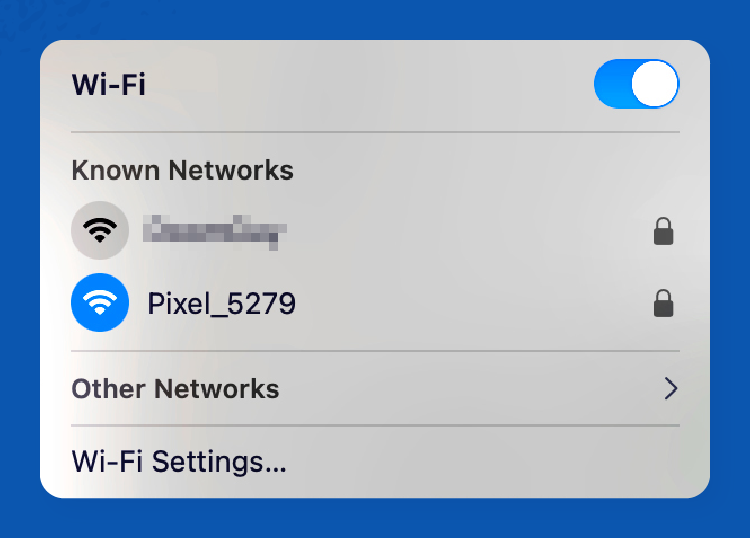
Setting up a hotspot on an iPhone:
Step 1: Go to Settings > Cellular. Confirm your Cellular Data is on. If you’re traveling, make sure your Cellular Data is set to Travel.
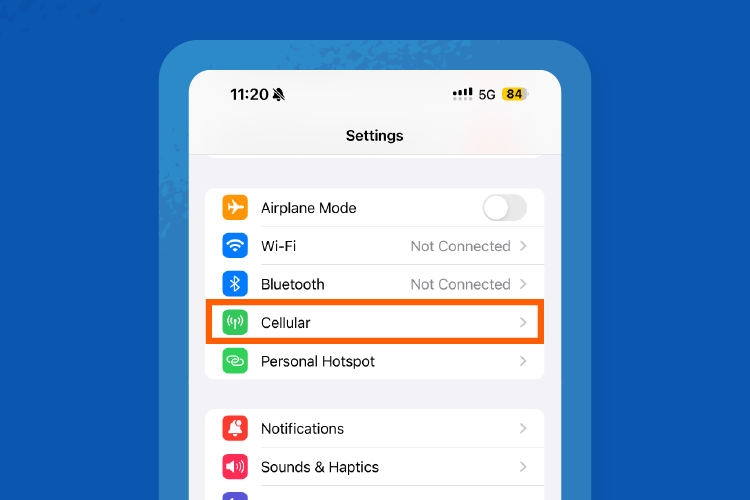
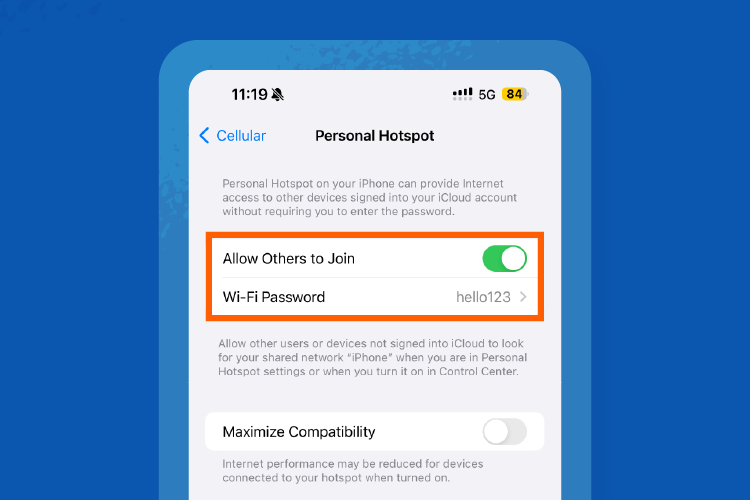
Step 2: Navigate back to Settings and click on Personal Hotspot.
Step 3: Turn on Allow Others to Join. You’ll also see the Wi-Fi password here to note for the next step.
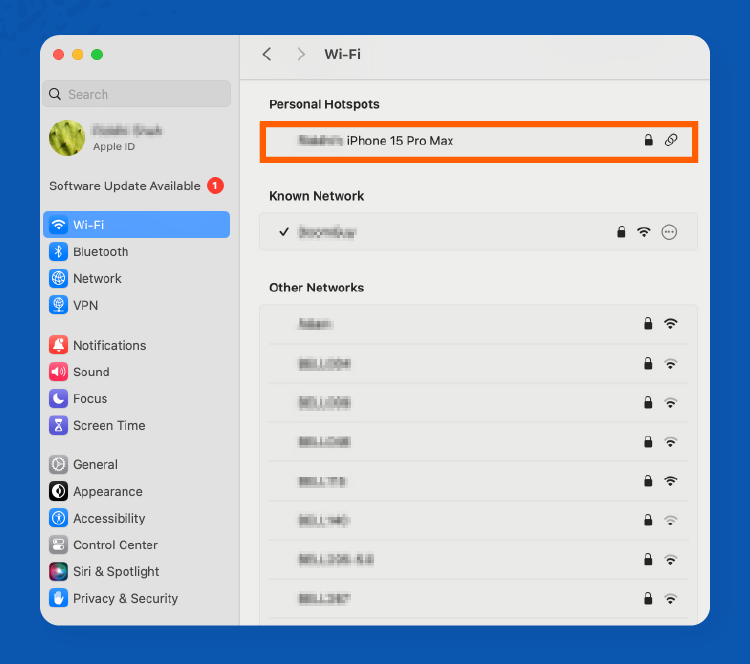
Step 4: Go to your computer’s Wi-Fi settings and find the list of available Wi-Fi networks. You’ll see the mobile hotspot you want to connect to. In this case, we will connect iPhone 15 Pro Max to an iMac.
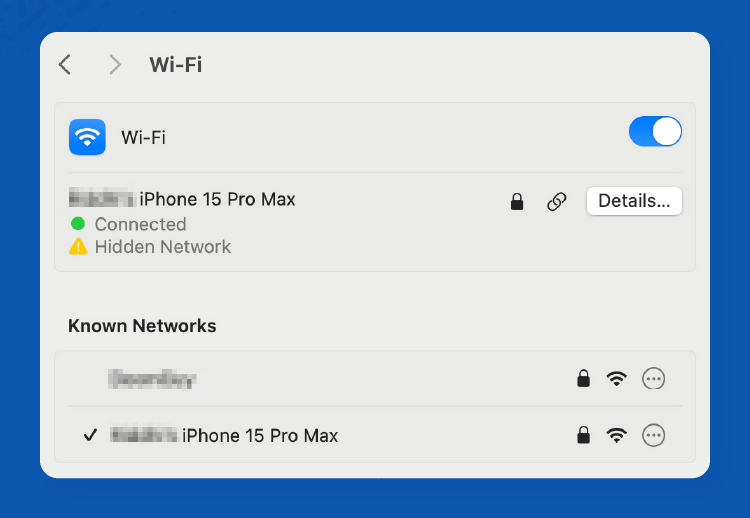
Step 5: Enter the hotspot password and connect your device.
3. Use Wi-Fi Hotspot Apps
While finding free Wi-Fi is great, many question whether the network is safe to join. While we always advise that you use a VPN when accessing free Wi-Fi, you can also download Wi-Fi hotspot apps. These can pinpoint Wi-Fi locations you can connect to, including networks that are hidden from view. The apps can also show you Wi-Fi networks outside your vicinity.
Pro tip: With an app like Instabridge, you can find crowdsourced Wi-Fi connections all in one place. Wi-Fi communities help you connect with others who have been to your locations and rated the Wi-Fi quality. This is a good way to plan ahead if you’ll need Wi-Fi for more than a few hours.
This app offers free Wi-Fi connectivity in just about every city in the world. It contains an interactive map that pinpoints all the hotspots near you. By clicking on the Free Wi-Fi Near Me button, Wifinity will show you how far you are from the nearest Wi-Fi hotspot and how to get there.
This Wefi app automatically connects your device to the best network in your location. It also contains a map showing Wi-Fi hotspots around you. Wefi delivers up to two times faster data transfer speeds on average than manual Wi-Fi selection.
4. Use a Portable Wi-Fi Router

Imagine carrying your own internet access wherever you go. A portable Wi-Fi device, also known as a mobile hotspot, is a pocket-sized gadget that creates its own personal Wi-Fi network.
Unlike relying on finding free public Wi-Fi, a mobile hotspot provides a secure and reliable connection. This is especially helpful in areas with limited or unreliable Wi-Fi availability, like remote locations or during travel. With a portable hotspot, you can connect your laptop, phone or tablet to the internet anytime, anywhere.
Here are a few of the best travel Wi-Fi devices: Tep, Roaming Man, TravelWifi and Google Fi Wireless.
Common Public Wi-Fi Threats
Public Wi-Fi offers a tempting connection to the internet, but it can be a breeding ground for security threats. Before you jump online at the coffee shop, be aware of the potential dangers lurking beneath the surface of that free signal. Here’s a breakdown of some common public Wi-Fi threats:
- Fake Wi-Fi hotspots: These malicious networks disguise themselves with names that look legitimate, like “Free Airport Wi-Fi” or “Coffee Shop Guest.” You can spot a fake Wi-Fi hotspot if it asks for your credit card information or any other confidential information. If you connect to one, hackers can easily intercept your data, including passwords, emails and even credit card information.
- Malware: Public Wi-Fi can be a breeding ground for malware, malicious software that can infect your device. Clicking on a suspicious link or downloading an unverified app can unleash a hidden threat. This malware can steal your data, track your activity or even take control of your device.
- Unsecured connections: Many public Wi-Fi networks lack proper encryption, which scrambles your data as it travels between your device and the internet. Without this encryption, anyone lurking on the network can eavesdrop on your online activity, potentially exposing sensitive information.
- Phishing attacks: Phishing emails or websites designed to trick you into revealing personal information are more prevalent on public Wi-Fi. Hackers can exploit the unsecured connection to send you emails that appear to be from legitimate sources, like your bank or a social media platform. Clicking on a link or entering your information on these fake websites can compromise your accounts.
- Unsecure file sharing: Downloading files on public Wi-Fi can be risky. The file itself may be infected with malware, or the download process could be intercepted, exposing your device to vulnerabilities. This is especially true for peer-to-peer (P2P) file sharing, where you connect directly to other users’ devices.
How to Stay Safe on Public Wi-Fi
While public Wi-Fi offers undeniable convenience, it can expose your devices and data to a range of security vulnerabilities. However, by adhering to well-defined security protocols, you can mitigate these risks and utilize public Wi-Fi connections with greater confidence. 
Tips to stay safe on public Wi-Fi:
- Use HTTPS sites only
- Refrain from accessing confidential data (ex. bank account)
- Give a secondary “spam” email for sign-ups
- Avoid performing online transactions
- Cover your keyboard when entering any passwords or credentials
- Install an antivirus that includes parental controls for kids accessing public Wi-Fi
- Always make sure paid Wi-Fi is legitimate and use a third-party payment system
- Keep antivirus up-to-date
Browsing on public Wi-Fi can be risky, but security doesn’t have to be complicated. A VPN encrypts your data like a virtual tunnel, shielding your online activity from prying eyes. Plus, a strong antivirus protects your devices from malware lurking on unsecured networks.
Download Panda VPN and antivirus for complete peace of mind while you connect on the go.
Free Wi-Fi Connection FAQ
Here are some answers to the most common questions about unlocking the web anywhere you go.
What Is the Difference Between Hotspot and Wi-Fi?
Wi-Fi and hotspots might seem interchangeable, but there’s a key distinction. Wi-Fi is a wireless networking technology that allows devices to connect to the internet. It acts like an invisible bridge between your device and a router or access point, which provides an internet connection.
On the other hand, a hotspot is a device or location that creates a Wi-Fi network. Think of it as a source that broadcasts the Wi-Fi signal. Your phone can use Wi-Fi to connect to a hotspot and access the internet through that connection.
What Is a Wi-Fi Hotspot?
A Wi-Fi hotspot is essentially a location or device that broadcasts a Wi-Fi signal, providing internet access to nearby devices equipped with Wi-Fi capabilities. For example, Wi-Fi at a coffee shop, public library and airports are all considered Wi-Fi hotspots.
Can I Get Free Wi-Fi at home?
Yes, you can get free Wi-Fi at home, but it can be a bit tricky. While options like using your phone’s data as a hotspot or finding open networks exist, they have drawbacks like data limitations or security risks. For reliable and secure internet access, a traditional home internet plan might be a better solution in the long run.






