Fast-forward to the year 2020: what cyberthreats is your company up against? In order to get a head start on the future of cybercrime, companies, government organizations, and citizens need to gear up for the challenges of a world which is ever more connected thanks to new advances in technology. The best way to avoid harm is to get ready for when it comes. The Information Security Forum, a non-profit association which analyses and researches the sector, has presented ‘Threat Horizon 2020’, a report which breaks the threats of tomorrow down into three main themes.
Large scale conflicts are looming
As the ISF points out, we are facing an uncertain future: nations, along with terrorist groups, organized criminals, hacktivists, and hackers, will be on the list of possible assailants putting security at risk. Protecting critical infrastructure will be key in 2020: with new possibilities of attacking energy, communications, and logistics systems, all kinds of organizations could lose the basic tools they need in their day-to-day operation.
With a combination of traditional military forces and new technologies which can be used in attacks, the cybercriminals of the near future will be able to create high impact situations which will put companies and nations at risk. In the wars of the future, as well as armies and missiles, digital attackers will also play a part. National cybersecurity departments are already preparing for possible unauthorized access to their infrastructure and their election systems. And this is a matter of when, not if it happens. In light of the possibility of these extreme consequences, the ISF recommends having in place an up-to-date incident response plan, as well as training and educating employees so that, if worst comes to worst, they know how to react at the outbreak of cyberwarfare.
The danger of the IoT: access points increase in number
As technology advances and becomes more democratized, more and more opportunities are created for organizations. But these progress scenarios are a double-edged sword for our security and our privacy. The increase in the number of IoT devices in business environments means an increase in the number of attack vectors. This in turn makes cybercriminals’ jobs a lot easier, as was the case in the recent DDoS attack on the financial sector, when televisions and webcams were hacked. Likewise, fridges, dishwashers, and smart coffee makers could be attacked in order to create power surges which could put electrical networks of whole regions at risk. As we’ve seen with attacks similar to Mirai, any IoT device is susceptible to remote hacking.
To cope with these assaults, the ISF recommends making sure that IoT devices connected to corporate networks can’t be used to attack the company. It’s worth remembering that neglecting such apparently harmless devices as printers can be dangerous.
More regulatory pressure, greater transparency
The last section of the report discusses the relationship between the new regulations and the growing burden that adapting to this new climate means for employees. The need for transparency will multiply information storage points and, by giving access to administrators who aren’t part of the organization, the likelihood of a security breach will also increase. At the same time, the strict privacy regulations will increase the financial repercussions of any attacks, via the imposition of significant fines.
With just a few hours left on the countdown to GDPR, the regulation that aims to protect the privacy of EU citizens’ personal data and control how companies can use this data, this point of view makes even more sense. Given these difficulties, the ISF recommends balancing the management of regulatory requirements with the business risks. It’s also vital to have tools which will simplify compliance with the different regulations for the protection of employees’ and clients’ data.
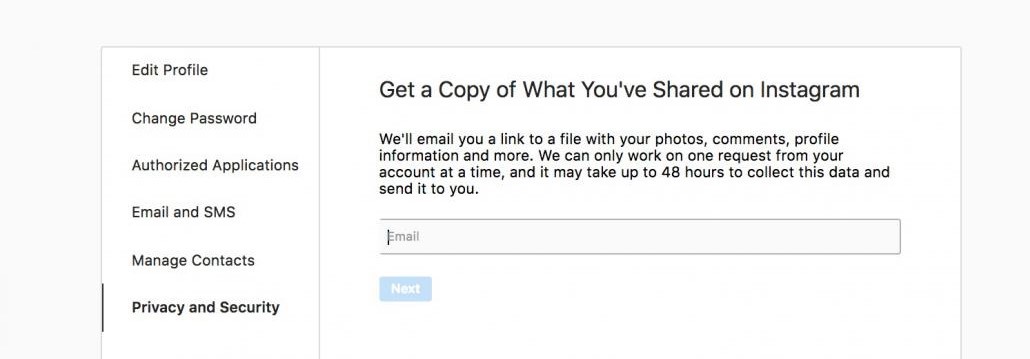
Companies such as Instagram already got a head-start on the May 25 deadline, with their new ‘Data Download’ function, which allows users to download a file containing all the photos, comments, and personal data from their profile. In this way, if a user wants to delete their account right away, they will be able to take all their information with them.
The world will be completely different in 2020, and there’s no one way to combat national attacks, reduce the risks associated with technological advances, or to comply with new legislation. Nevertheless, in the cybersecurity world, tools such as Panda Adaptive Defense 360 can ease the transition to new, ever smarter environments, with tools of the future for threats of the future. Don’t wait until 2020!