Are you OK with a stranger reading your emails?
Most people would answer that question with a resounding “no” — but unfortunately, in this modern technological age, it’s far too easy for cybercriminals to gain access to your email accounts or the messages themselves. To guarantee your information is safe from prying eyes, you need Pretty Good Privacy (PGP) encryption.
So what is PGP? In short, it is an encryption system that scrambles your data, making it unreadable to anyone who doesn’t have the means of decoding it. By coordinating and sharing virtual keys, email senders and receivers can ensure their information stays private and secure.
In this article, we’ll detail the basics of PGP encryption: what it is, how you can use it and if this technology is right for you.
What Is PGP Encryption?
PGP is an encryption system that’s used to safely send sensitive or private information. First developed in 1991, this technology has become one of the most popular encryption methods on the market due to its security and accessibility.
PGP encryption is most commonly used for sending and receiving confidential emails. Cybercriminals can easily intercept messages and access email accounts, and PGP ensures that the user’s information remains secure.
In an age where cyberthreats lurk around every virtual corner, this type of encryption is an essential tool for anyone who wants guaranteed privacy in their digital communications.
How Does PGP Encryption Work?
PGP encryption works by scrambling, or encrypting, a message in a way that makes it unreadable to anyone who lacks the means to decode it. In order to fully understand PGP encryption, we will look at it from a technical perspective and provide a practical analogy.
At a high technical level, PGP encryption protects data by using a combination of public keys, private keys and session keys.
When a user wants to send a private email or message, they’ll encrypt it using the receiver’s public key — an encryption key that’s known to everyone. Once the receiver gets the email, they’ll decrypt it using their private key — an encryption key that is only known by one user. This ensures that the message gets where it needs to go and that the recipient is the only one who can decrypt the message.
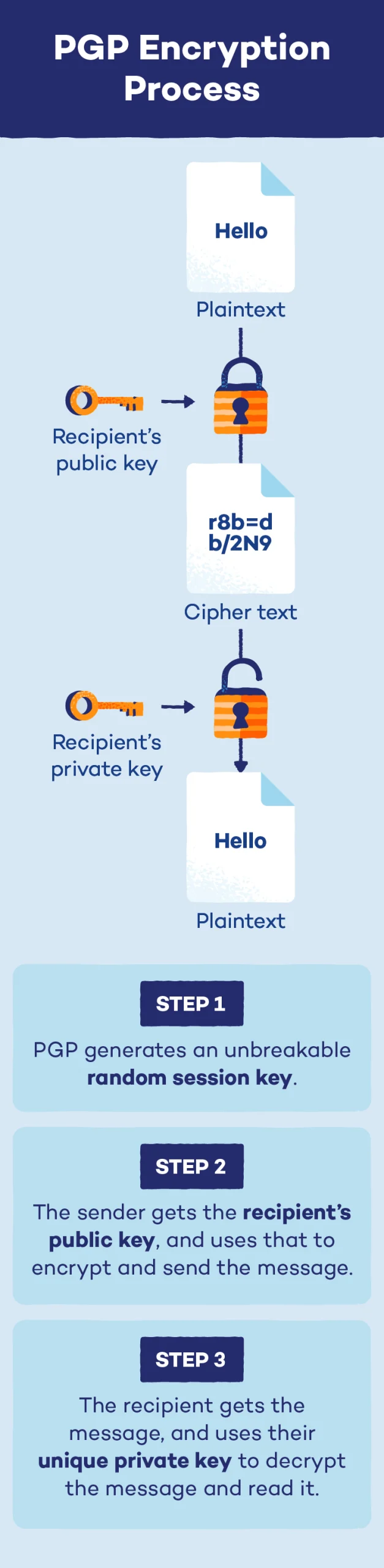
To sum it up, PGP encryption works in a three-step process:
- Step 1: PGP generates an extremely complex single-use random session key that cannot be guessed.
- Step 2: This session key is encrypted using the recipient’s public key. This public key is associated with the individual, and they can share it with anyone they wish to receive messages from.
- Step 3: The sender passes along their session key, and the recipient can use their private key to decrypt and read the message.
Now that we’ve walked through the technical aspects of PGP, let’s look at an analogy to reinforce the concept:
- Michael wants to send Beth a private message.
- In response, Beth sends Michael an open box (her public key) as well as an open padlock (that only she has the key for).
- Michael puts the message in the box, closes it and locks it with the padlock. Now that the padlock has been closed, no one but Beth (the owner of the private key) can open it.
- Michael sends the box to Beth, who opens it with her private key.
As you can see, with PGP encryption, Michael won’t have to worry about the box getting lost or stolen in transit because only Beth has the means to open the lock.
At the end of the day, that’s what makes PGP encryption so secure — and also why it’s critical you don’t lose or share your private key if you’re sending encrypted files regularly.
How to Use PGP Encryption
You can use PGP encryption wherever you need an assurance of technological privacy. That said, the three most popular ways of using it are email and file encryption and digital signature verification.
Encrypting Emails
Email messaging has become one of the most common ways of exchanging information, but this communication method comes with risks. Both email accounts and the messages themselves can easily be intercepted by cybercriminals and other unauthorized individuals, leading to potential data leaks.
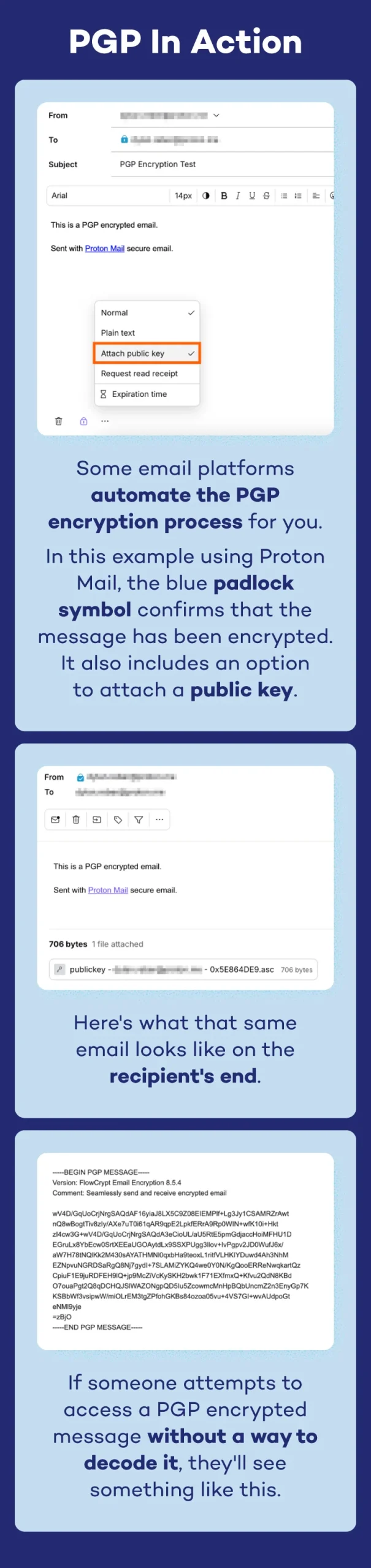
PGP encryption solves this problem by engaging in the secure information exchange process we outlined above. Protecting emails is the most common reason people use PGP encryption. Here’s what it looks like in action:
Encrypting Files
Because the complexity of the PGP algorithm makes it virtually unbreakable, this encryption method is also useful for securing personal files.
Individuals can use PGP to encrypt files on their computer, flash drive, external hard drive or other storage devices. Paired with threat detection and response tools, PGP file encryption helps keep your personal information private.
Digital Signature Verification
Through PGP, individuals can also ensure the authenticity of electronic documents by verifying the identity of the sender and confirming that the information in the message has not been tampered with.
These digital signatures work by generating and encrypting a hash of the message, or a fixed block of data, when it is sent. The recipient of the message can access this data through the use of public and private keys, and they will be able to see if the message has been altered or otherwise manipulated.

Is PGP Encryption Right for You?
PGP encryption is a powerful tool, but is it right for you? Below, we highlight the pros and cons of this technology.
| Pros | Cons |
|---|---|
| Unbreakable encryption | Software can be complex |
| Enhances cloud security | Requires training |
| Cheap and free options | Not anonymous |
Pros of PGP Encryption
PGP encryption is a popular method to keep information secure — and for good reason. A few of the top benefits of this technology include:
- Unbreakable algorithm: PGP’s algorithm is virtually unbreakable, meaning your communications, files and other information is guaranteed to be safe from unauthorized users.
- Enhanced security: Consistently using PGP in communications will enhance cloud security, leading to a more secure online experience for individuals and businesses.
- Inexpensive: PGP software is affordable, with a multitude of cheap yet effective options on the market.
Cons of PGP Encryption
While this technology is extremely effective, there are still a few downsides users should be aware of. A few of the cons of PGP encryption include:
- Complex: PGP encryption is a complicated software that can be difficult and time-consuming to learn.
- Requires training: To guarantee security, all users must safeguard their private keys. If an individual misplaces or accidentally gives away this information, there is real potential for security breaches and exposed information.
- Can’t be anonymous: All senders and recipients of information sent with PGP can be traced, meaning there is no ability for anonymity with this encryption method.
How to Set Up PGP Encryption
Now that you’re an expert on PGP, you may have decided to use the technology in your communications going forward. Luckily, setting up and using PGP is an easy process.
Choosing a PGP Provider
The first step is to select a PGP provider. There are plenty on the market — both free and paid options — that are compatible with Windows, Mac, Linux, iOS and more. OpenPGP and Gpg4win are two free options with good reviews. Alternatively, you can sign up for an email platform that utilizes PGP or install a PGP browser extension.
Setting Up PGP
Once you’ve downloaded the software, you will generate your public and private keys directly from the platform. From there, your email client will have a new option to easily encrypt the email message — and with that, you’ll be communicating securely with PGP.
PGP Encryption FAQ
Finally, we will wrap up with a few frequently asked questions about PGP encryption.
Is PGP Encryption Still Used?
Yes, PGP encryption is still used today. In fact, it is one of the most popular security methods when sending sensitive information over email.
What Is a PGP Key?
PGP keys come in three forms: public, private and session. The session key is a massive number that cannot be guessed, which is then encrypted by the public key. The private key decrypts the PGP-encrypted message once it has been delivered.
How Do I Get a PGP Key?
PGP keys can be generated using PGP encryption software. If you don’t want to download a program, some email platforms support PGP and can generate keys for you.
How Secure Is PGP?
PGP is very secure. PGP encryption is an extremely complex algorithm that cannot be cracked, guaranteeing the safety of your data, email communication and other information.
Is PGP Better Than AES?
PGP is just as effective as AES (Advanced Encryption Standard), and which one you choose depends on your preferences. The main difference is that AES uses the same key to encrypt and decrypt, while PGP uses two different keys.
Panda Security Can Help With Online Privacy
PGP encryption is a powerful tool you can use to protect emails, personal files and other sensitive information. That said, online privacy doesn’t start and end with PGP — to achieve comprehensive security, you need to make sure your devices and networks are safe.
At Panda Security, we have a variety of tools such as password managers, antivirus tools and dark web scanners to ensure you stay safe no matter where you virtually visit. Let us help you on your tech journey today.




