WhatsApp scams and text scams can deceive users into giving away personal information and trick them into paying money for fake services or products. According to Robokiller, there were 19.2 billion spam texts sent in January 2024 alone. This equates to nearly 19 spam texts for every person in the U.S.
Understanding the various types of WhatsApp scams — such as getting scam messages from 234 WhatsApp numbers — is essential to protect yourself from these deceptive tactics.
In this post, we’ll talk about some of the most common WhatsApp scams, learn how to spot a WhatsApp scam and share some tips to stay vigilant against these schemes.
1. Impersonation Scams
Scammers create fake WhatsApp accounts posing as someone the victim knows, such as a friend, family member or colleague. They then use these accounts to send messages requesting money or personal information, exploiting the trust between the victim and the impersonated individual. These messages may appear urgent or convincing, leading the victim to comply with the scammer’s demands.
Example: A scammer creates a fake WhatsApp account posing as a friend and asks you to wire $1,000 — claiming to be in a financial crisis.
2. Phishing Links
Phishing is one of the most common tactics used by scammers on WhatsApp. They send messages containing links that appear to be from reputable sources, such as banks, government agencies or well-known companies.
These links lead to fake websites designed to steal login credentials, financial information or other sensitive data from unsuspecting users. Phishing links can also be disguised as legitimate messages from WhatsApp itself, prompting users to verify their accounts or download software updates.
Example: A user receives a message with a link appearing to be from WhatsApp, asking them to verify their account due to a security breach. The link leads to a fake website designed to steal login credentials.
3. Fake Promotions
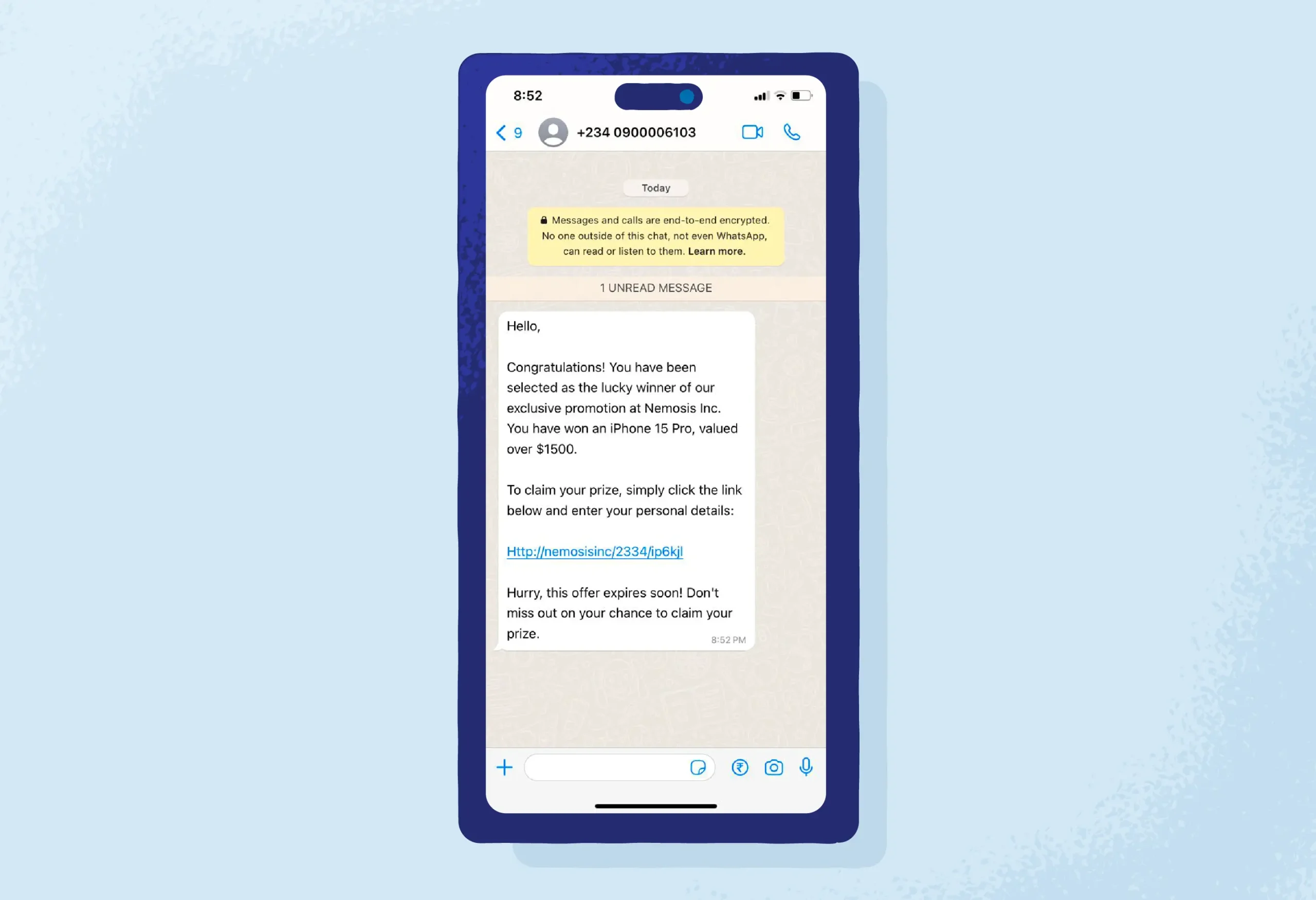
In this type of phishing scam, scammers often send messages promising exclusive promotions, giveaways or discounts to lure users into clicking on links or providing personal information.
These messages may claim to offer prizes from well-known brands or retailers, but in reality, they lead to fake websites designed to collect users’ personal and financial details. Be cautious of unsolicited messages promising rewards or discounts and always verify the legitimacy of the offer before taking any action.
Example: A user receives a message claiming to offer a free iPhone as part of a promotional giveaway from a well-known tech company. The message directs them to a fake website to enter personal information to claim the “prize.”
4. Advance Fee Fraud
This scam involves promising victims a large sum of money in exchange for a small initial payment. However, the promised funds never materialize, and the victim ends up losing the initial payment.
Example: A scammer might claim that the victim has won a lottery and needs to pay a small processing fee to claim the “prize.”
5. Tech Support Scams
Scammers pose as tech support representatives and contact users, claiming issues with their WhatsApp accounts or other social media accounts such as Facebook Page or Instagram Business accounts that may be linked to the WhatsApp account. They then request access to the user’s account or personal information under the guise of fixing the problem.
Example: A scammer might send a message pretending to be an official WhatsApp support technician claiming that the user’s social media account has been compromised and ask for their login credentials to “secure” the account.
6. Investment Scams
Scammers persuade users to invest in fake schemes promising high returns, only for the victims to lose their money. They may use WhatsApp to promote these fraudulent investment opportunities and pressure victims into making quick decisions.
Example: A scammer might promise guaranteed returns on a cryptocurrency investment and convince the victim to transfer funds to their account.
7. Romance Scams
Scammers build romantic relationships with victims on dating apps such as Tinder. They then gradually move to WhatsApp, gaining the victim’s trust over time. Once trust is established, the scammer requests money from the victim for fabricated reasons such as medical emergencies or travel expenses. Keep an eye out for catphishing, especially in the online dating world, to avoid Tinder WhatsApp scams.
Example: A scammer might pose as a love interest and ask the victim for financial assistance to cover supposed medical bills.
8. Identity Theft
Scammers use WhatsApp to trick users into sharing personal information such as login credentials, bank account details or Social Security numbers. This information is then used for identity theft, which can lead to financial loss or other forms of fraud.
Example: A scammer might send a message claiming to be from a trusted organization such as Google and ask the user to verify their Gmail account by providing sensitive information.
9. Fake News and Hoaxes
Scammers may use WhatsApp to spread false information for various purposes, including political manipulation or financial gain. The scammer could message the victim with a fake news article that is simply clickbait. This link may lead the victim to a malicious website that asks for money to view certain “classified” or “exclusive” information.
Example: A scammer might create and share a fake news article about a celebrity’s death to attract clicks to a malicious website that asks for money to read more details about the death.
10. WhatsApp Gold Scam
Since it first appeared in 2016, the WhatsApp Gold scam has continued to be one of the most viral scams. The scam begins with a deceptive message circulating on social networks, enticing WhatsApp users to click on a link promising access to a non-existent Oro (Gold) version of the app.
This version supposedly offers exclusive features and enhancements. However, clicking the link redirects users to a fraudulent webpage, where they are prompted to provide their phone number to access the purported upgrades.
However, giving your phone number signs you up for a costly premium SMS service. Each text message received through this service incurs a charge of €1.45, leading to a maximum monthly charge of €36.25.
Example: The scam WhatsApp message may look like: Hey there! Have you heard about WhatsApp Gold? It’s the exclusive new version with amazing features like video calling and enhanced security. Just click this link to upgrade now and enjoy all the benefits.
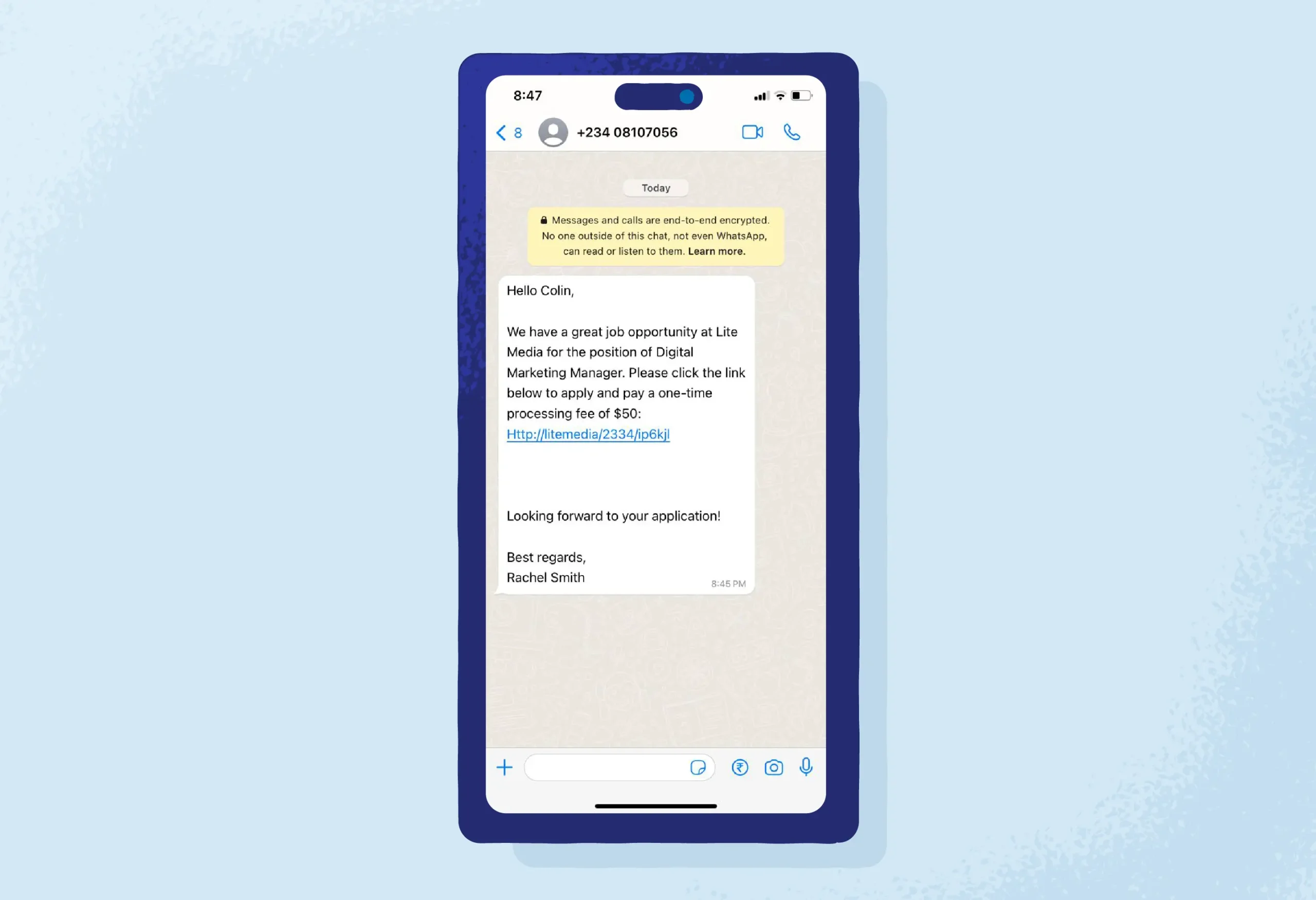
11. Fake Job Offers
Scammers offer fake job opportunities via WhatsApp, requesting payment for training or materials upfront. They may pose as legitimate companies or recruiters, luring victims with lucrative job offers.
Example: A scammer might promise a high-paying remote job and ask the victim to pay for training materials or a background check.
12. Fake WhatsApp Voicemail
Not all WhatsApp scams happen via text message. Scammers also use fake voicemail messages on WhatsApp to pretend to be someone you trust, like a friend or a bank. They might say there’s an urgent issue and ask for your personal information.
Example: You receive a voicemail on WhatsApp from Bank of America claiming suspicious activity on your bank account. The message asks for your details through a link or phone number, but it’s a scam to steal your information and commit fraud.
13. Scam Voice Calls
Scammers may try to initiate voice calls on WhatsApp to deceive users. They often use techniques like impersonating someone the victim knows or claiming to represent a legitimate organization.
During the call, they may attempt to extract sensitive information or persuade the user to take certain actions, such as sharing personal data or clicking on malicious links.
Example: A scammer calls pretending to be a bank representative and asks for account information under the guise of a security check.
How to Spot a WhatsApp Scam + 5 Protection Tips

Be cautious of unsolicited messages on WhatsApp, especially those that compel you to take quick action. Scammers often use urgency as a tactic, urging recipients to act immediately without giving them time to think.
Watch out for words like “hurry” or “emergency” in these messages, as they are red flags indicating potential scams. Additionally, be wary of offers that seem too good to be true, such as winning a lottery or receiving a large sum of money for no reason.
These offers are often used to lure victims into sharing personal information, including passwords or other sensitive data. Remember, legitimate organizations will never ask for your password or other personal information via WhatsApp or any other messaging platform. Always verify the authenticity of such messages before responding or taking any action.
It’s a good practice to use a password manager to generate and store strong and secure passwords for different accounts, helping to protect against scams and unauthorized access.
Let’s look at some protection tips to stay safe from WhatsApp scams.
Verify Contacts
Be cautious of unsolicited messages and always double-check the identity of senders, especially if they claim to be from a known organization or someone you trust. This simple step can help prevent falling victim to impersonation scams.
Enable Two-Factor Authentication
Protect your WhatsApp account from unauthorized access by enabling two-factor authentication. This additional layer of security sends a verification code to your phone number or email, preventing scammers from gaining access to your account.
Update Privacy Settings
Adjust your WhatsApp settings to limit who can see your profile information, status updates and “last seen” status. This helps safeguard your personal information from potential scammers. Check out this guide for tips on updating your Android privacy settings.
Educate Yourself
Stay informed about the latest scams and common tactics scammers use to avoid falling victim to their schemes. Educate yourself about different types of scams to recognize and avoid potential threats on WhatsApp and steer clear of social media scams.
Report Suspicious Activity
If you receive a suspicious message or encounter a potential scam on WhatsApp, report it to the platform and warn others in your network. Reporting suspicious activity helps protect yourself and others from falling victim to scams.
For added protection against viruses and hackers on your mobile device, consider using Panda Antivirus. With advanced security features, Panda Antivirus safeguards your device and personal information from online threats. Download now for peace of mind.
WhatsApp Scam FAQ
Whether you’re curious about specific area codes or the potential risks associated with sharing your phone number, we’ve got you covered. Read on to learn more about protecting yourself from scams on WhatsApp.
What Is the Area Code 234 in WhatsApp?
The area code 234 is often associated with WhatsApp scam messages originating from Nigeria. Scammers use this area code to deceive unsuspecting users into believing they are receiving messages from legitimate sources. However, it’s important to exercise caution and verify the identity of senders, especially if they request personal information or financial assistance.
Do Scammers Use WhatsApp?
Yes, scammers use WhatsApp to carry out their fraudulent activities. WhatsApp provides scammers with a convenient and widely used messaging platform to reach a large number of potential victims. Scammers may use WhatsApp to impersonate trusted contacts, send fake job offers or promotions, request personal information or payments, spread misinformation and more.
What Can a Scammer Do With My Phone Number?
Scammers can use your phone number for various malicious purposes, including identity theft, phishing attacks and unauthorized access to your accounts. By obtaining your phone number, scammers may attempt to impersonate you or contact you with fraudulent offers or requests. It’s crucial to be vigilant and avoid sharing your phone number with unknown or untrusted sources to protect yourself from potential scams on WhatsApp and other platforms.





2 comments
I want to know if all the people the
Use 234 code are scammer?
Or only certain people .
How do you know if the person is
Scam or not?
As the article says: Trust your instincts. But don’t do like my friend; her instincts led her to lose a lot of money and gotten into trouble.