Riskware is any software that poses a security risk due to vulnerabilities. The danger of riskware is that even legitimate, functional programs may have risky features that hackers can target and exploit. Keep reading to learn more about what riskware is, how it affects you, and how to get rid of it with antivirus software.
What Is Riskware?
Any software that features risks like security vulnerabilities, legal violations, or software incompatibilities is considered riskware. With that being said, not all riskware is a form of malware. Riskware includes both legitimate and illegitimate software that is vulnerable to cyber threats.
Oftentimes, riskware isn’t designed to be malicious. Rather, the programs happen to have functionalities that hackers can abuse. Essentially, this type of software isn’t a definite risk, but a potential one. Riskware only becomes dangerous when cybercriminals misuse it to gain access to your systems or data.

Typically, hackers can infiltrate a program because of development vulnerabilities or data breaches. There is also the possibility that a program is blatantly abusing the privacy practices of its users and bundling illegitimate software with a legitimate program.
Common Riskware Examples
Examples of riskware include any software that violates laws, monitors user behavior, or has other vulnerabilities that provide access for malware.
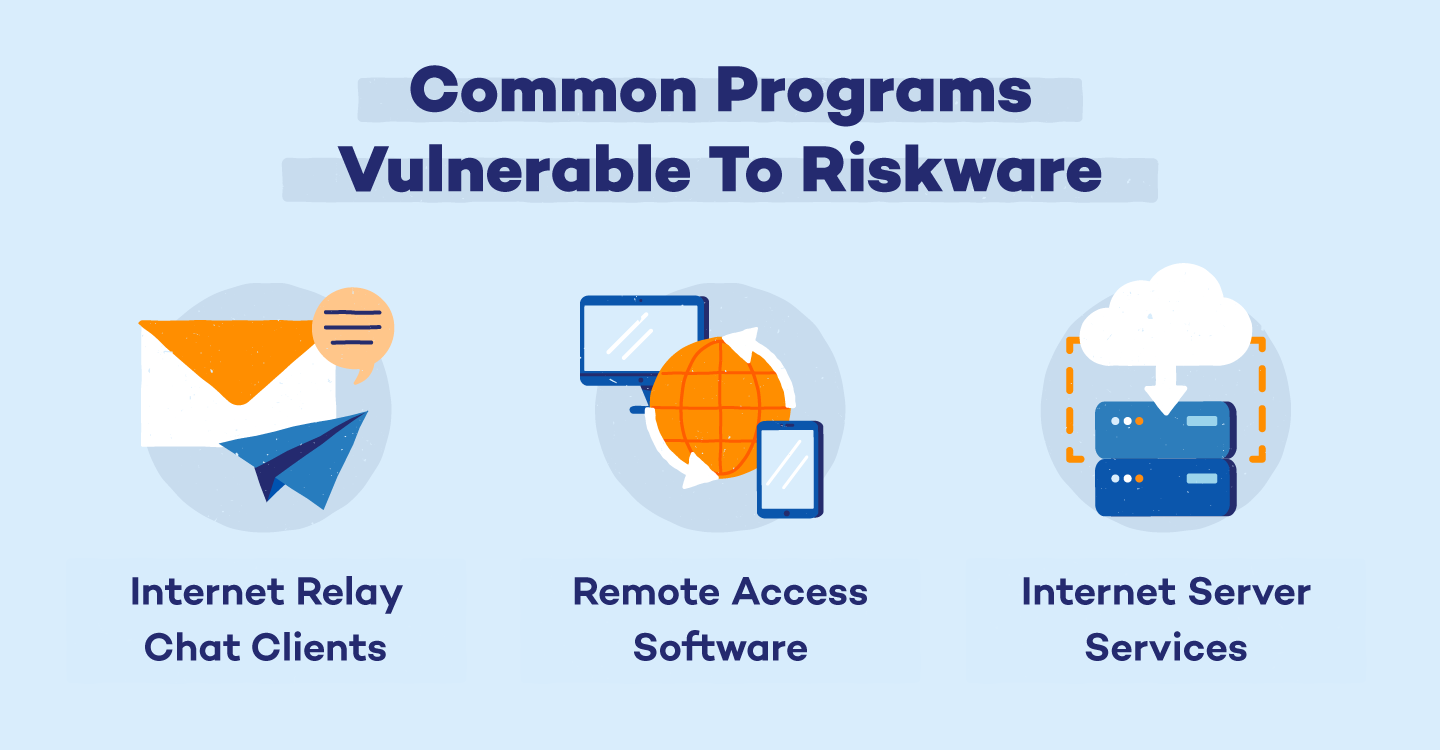
The following types of programs are often associated as riskware: internet relay chat clients, remote access software, and internet server services. Read more about each of these programs below.
Internet Relay Chat Clients
Programs that allow for instant messaging and dialer programs such as Voice over Internet Protocol (VoIP) may have extended features that are exploited by malicious users. In the worst case, a backdoor could allow a malicious user to write dangerous script while the chat user is unaware, leaving them susceptible to malware.
Remote Access Software
Also called Virtual Network Computing (VNC), this type of software allows remote access to your desktop, software, utilities, and administrator privileges. While these programs are often legitimate, they can leave users open to security risks if the software is not properly secured against hackers.
Internet Server Services
When a malicious user finds another user that allows file transfer protocol’s full access to their administrative privileges, they can install a server. This gives the hacker access to all files while the user is on the internet. This practice can be present on file downloaders such as web and proxy servers, programs to transfer files over the internet, and auto-installers for mobile devices.
How Riskware Affects You
Riskware is dangerous because it leaves users vulnerable to unethical practices by malicious users. Not only is your highly-sensitive information able to be exploited, but there are legal consequences that come along with it. Below are the main problems that riskware may cause for you:
- Data or program exploitation leaves you vulnerable to data breaches or unauthorized system access
- Legal ramifications that stem from the abuse of privacy or illegal modification of programs on your system
- Network or computer disruptions make it difficult to use your programs productively or cause your computer to shut down entirely
Although the presence of riskware leaves you vulnerable to these problems, it has to first be abused by a cybercriminal to have these consequences. This is why it’s important to learn how to identify riskware on your devices and take steps to prevent hackers from misusing it.
How To Spot Riskware
Antivirus programs won’t always be able to detect riskware unless it’s a malware threat, so it’s important to manually vet potential vulnerabilities. Here are a few things to look out for when searching for riskware:
- Check for outdated operating systems and apps that developers no longer update. These are particularly vulnerable to exploitation by malicious users and are generally considered riskware.
- Review the terms and conditions of your software, as it’s often a signal of riskware. If two programs interact and one disables the features of another, the disabling program may be riskware.
- Confirm that you authorized a program’s permissions. Any program that you didn’t directly authorize could be a sign of riskware. These programs commonly attempt to gain access to your system’s core data, internet functionality, and hardware like microphones and cameras, to misuse them.
How To Get Rid of Riskware
Vulnerabilities in risky software leave you open to malware threats. Malware attempts to exploit security vulnerabilities within developmental errors of a program. Typically, these threats are bundled with legitimate programs that run once the original program is opened.
If your computer warns that riskware is detected on a website or application, proceed with caution, and if you’re experiencing a malware infection, reference this guide on malware removal.
If you suspect that riskware is on your device, take the following steps to get rid of it:
- Uninstall the affected program
- Run an antivirus detection software to find and remove potential threats
How To Prevent Riskware Threats
Fully preventing riskware means being cautious of any program you use. On a macro level, always practice safe computer habits like only visiting trustworthy websites to proactively protect against malware.
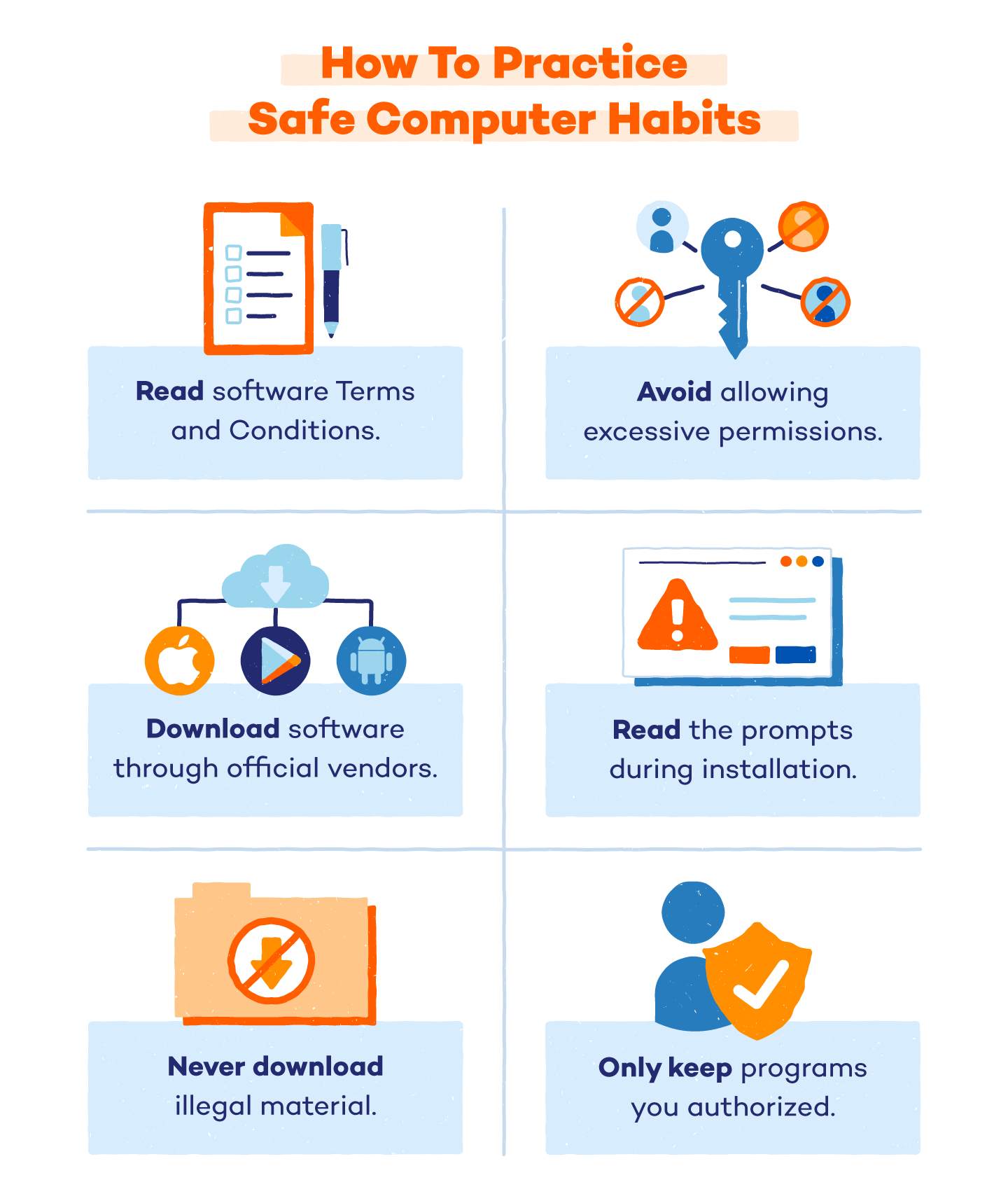
Safe Computer Habits That Prevent Riskware Threats:
- Read the Terms and Conditions thoroughly and delete software that prohibits other software from functioning properly.
- Avoid software that requests excessive permissions without a clear reason.
- Only download software through official vendors like the Apple Store or Google play store.
- Always read the prompts when installing new programs.
- Never download illegal or explicit material on your device.
- Avoid running programs that have administrator privileges.
- Only keep the programs you have authorized on your computer.
Safe computer habits and a proper antivirus defense are the best way to protect yourself against riskware on your system. Be proactive when allowing permissions and avoid allowing unnecessary privileges. If you suspect malware on your device, carefully vet any installed programs and applications, and delete any that you haven’t authorized.





