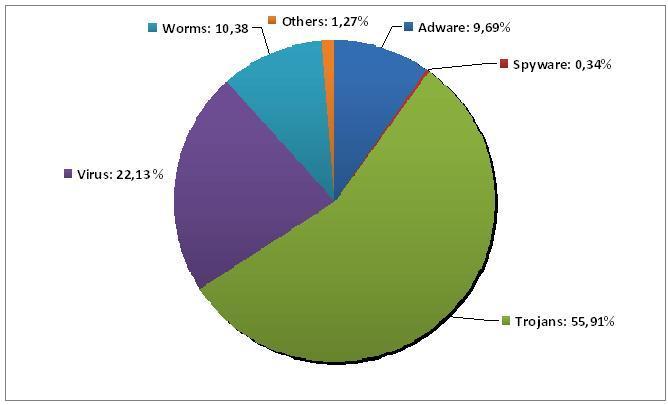
Top Five malware in 2010. Protect yourself against them with Panda Antivirus!
Posted by Blanca Carton, January 2011 Every year, PandaLabs, Panda Security’s anti-malware laboratory, publishes an annual malware report discussing the year’s most virulent threats. In…
Panda Security launches version 5.05 of its cloud-based security solution Panda Cloud Office Protection
The new version includes new features to simplify management and make the solution more efficient, both for corporate end-users and for channel partners and service…
Reader’s Choice Award 2011
Mary Landesman and the editors of antivirus.about.com recently launched the “Reader’s Choice Awards 2011” for favorite antivirus by the community. The first step is a…
An image is worth a thousand words: Video on how to activate Panda 2011 antivirus on YouTube
As the saying goes: an image is worth a thousand words. That is why, and because the motto of Technical Support at Panda Security is…
Panda Security opens registration for the third Security Blogger Summit
Cyber-activism and cyber-war will be the core themes of this year’s event, to be held on February 3 at the Círculo de Bellas Artes, Madrid,…
2010 Annual Security Report
PandaLabs, the anti-malware laboratory at Panda Security –The Cloud Security Company–, has published its 2010 Annual Security Report covering an extremely interesting year with regard…
PandaLabs Annual Report 2010
2011 has just started, so it is time to look back at what has happened in the last year. Today we publish the 2010 Annual…