How to find out if you are receiving malware on Twitter
Social networks are actively used by cybercriminals to spread malware. The most common type of attacks in Twitter usually show the same behaviour: 1.- You…
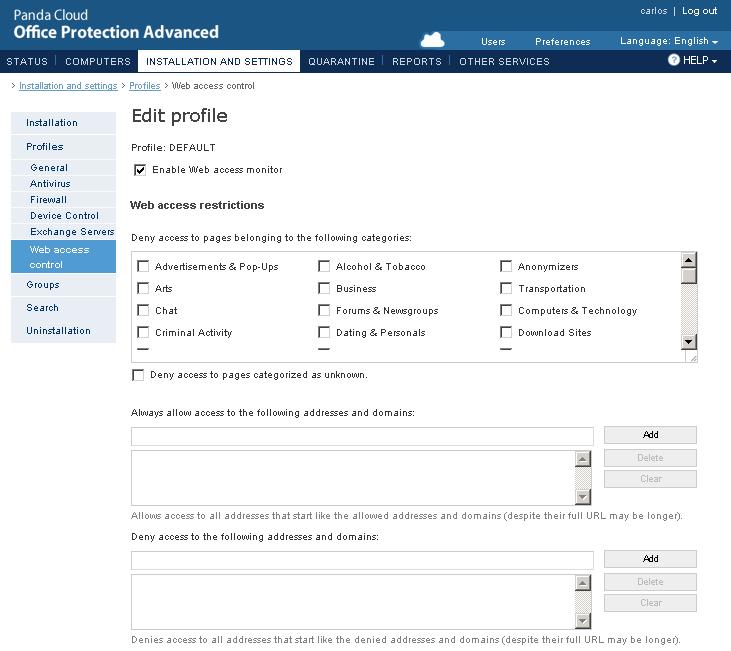
Panda Security Launches Beta Version of Panda Cloud Office Protection Advanced 6.50, Announces Beta Tester Challenge
New version includes URL filtering and anti-exploit technologies, capable of detecting malware that exploits 0-day vulnerabilities The beta is compatible with Microsoft’s new messaging platform…
All that glitters is not gold
As the old saying goes, “All that glitters is not gold”. We live in a time of information abundance, overloaded with eye-catching news stories and…
Panda Security Wins Best eCommerce Software in Best Customer Experience Awards 2012
The study, conducted among consumers in Spain, evaluates the top 500 businesses in the country Panda Security won the ‘Best eCommerce Software’ award, 89 points…
Are passwords dead?
Last Friday my friend Bob McMillan wrote an article on Wired (Google Declares War on the Password) which talks about a research paper Google will…
Java 0-Day vulnerability – A “New Year’s Gift”
These days, the most talked-about story in the security world is the discovery of a new Java vulnerability that could allow attackers to spread…
Hooked on the Internet – Part II
Last week, in Hooked on the Internet? we described the symptoms someone going through a so-called addiction to the Internet could experience. Today we continue…