Your likes in Facebook can be the passwords of the future
Do you remember, who was the last person you spoke on the phone with? And the first one you sent a WhatsApp message this morning?…
ICSA stands out Panda Security for 15 years of excellence
The good performance and the excellence of Panda Security has been recognized by ICSA (International Computer Security Association) because of having received quality certifications on…
When printers and routers become weapons to make web pages fall
A single denial-of-service attack (DDoS) can make medium and large companies loose tens or hundreds of thousands of euros, according to most studies published in…
Heartbleed. Why do the vast majority of companies remain vulnerable?
When you visit a webpage, your computer actually accesses the server where the files displayed on your screen are located. If you enter a password…
10 commandments for remote desktop managers – Infographic
Try Systems Management, the new way to manage, monitor and support IT systems! If you want to share this infographic, here you have the…
The famous reversible USB could be a ‘malware’ loophole for your devices
Wouldn’t it be nice not having to turn around several times your USB before connecting it to the computer? You won’t remember that feeling, very…
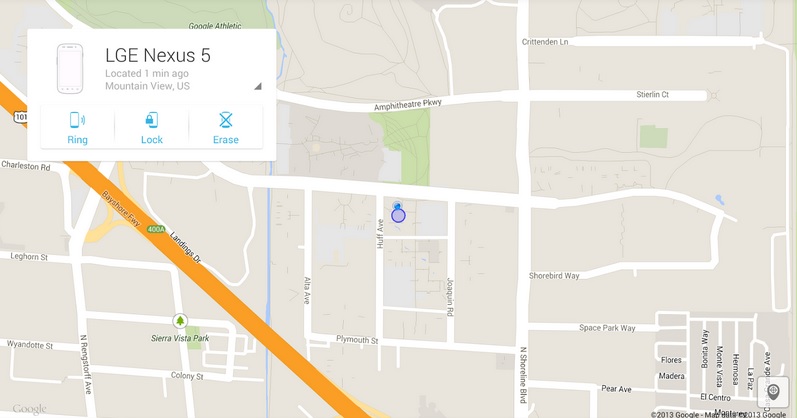
A Google search is enough to find your lost or stolen mobile phone
As much as you look for it you can’t find it. It is not on the table where you usually put it, it is not…