Panda Security presents the Security Guide for Small Businesses and Freelancers
We could give you a lot of reasons to elaborate this guide, but we think that one should be enough: 91% of small businesses and freelancers suffer daily…
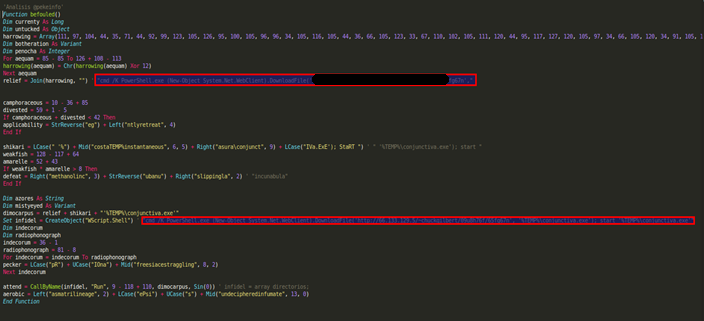
Locky malware report
The main objective of the Locky malware is to encrypt certain system files and network drives to coerce the affected user into paying a ransom…
The first keyless car is on the way (with security in the hands of a smartphone)
First we had keys that could remotely unlock the car door at the push of a button, an almost universal feature today. Then came keyless…
10 things we learnt from viruses of the past
A very special museum has just opened its doors, albeit virtual ones. The gallery is online and its works aren’t paintings, nor sculptures, nor antiques:…
Knowing how many calories you’ve consumed is great, but be careful with fitness bracelets
Thanks to their inbuilt sensors, bracelets and other wearables have become the perfect tool for monitoring our fitness and wellbeing – they inform us of…
Safer selfies on the way as Instagram plans two-step verification
More than 400 million selfie lovers can breathe a sigh of relief – Instagram, the social network phenomenon, has revealed that the two-step verification process…
Panda Security launches its Practical Security Guide for avoiding cyberextortion in businesses
In order to stop an organization becoming a victim of cyber extortion a combination of security technology, company policy and training are the most important…