Science is one step closer to reading your mind
Thanks to technology and an implanted brain chip, for the first time ever, a quadriplegic recovered mobility in one of his hands. But there’s a downside.
Tips to help protect your professional Apps
Here at Panda, we are celebrating International Workers’ Day. We want to share some tips with you that will help keep you secure while using Apps for your professional life.
The Hotel Sector: an easy target with juicy profits
Stealing information and then holding it for ransom is a trendy cyber-attack that has arrived to the hotel sector. PandaLabs, Panda Security’s anti-malware laboratory, is launching a…
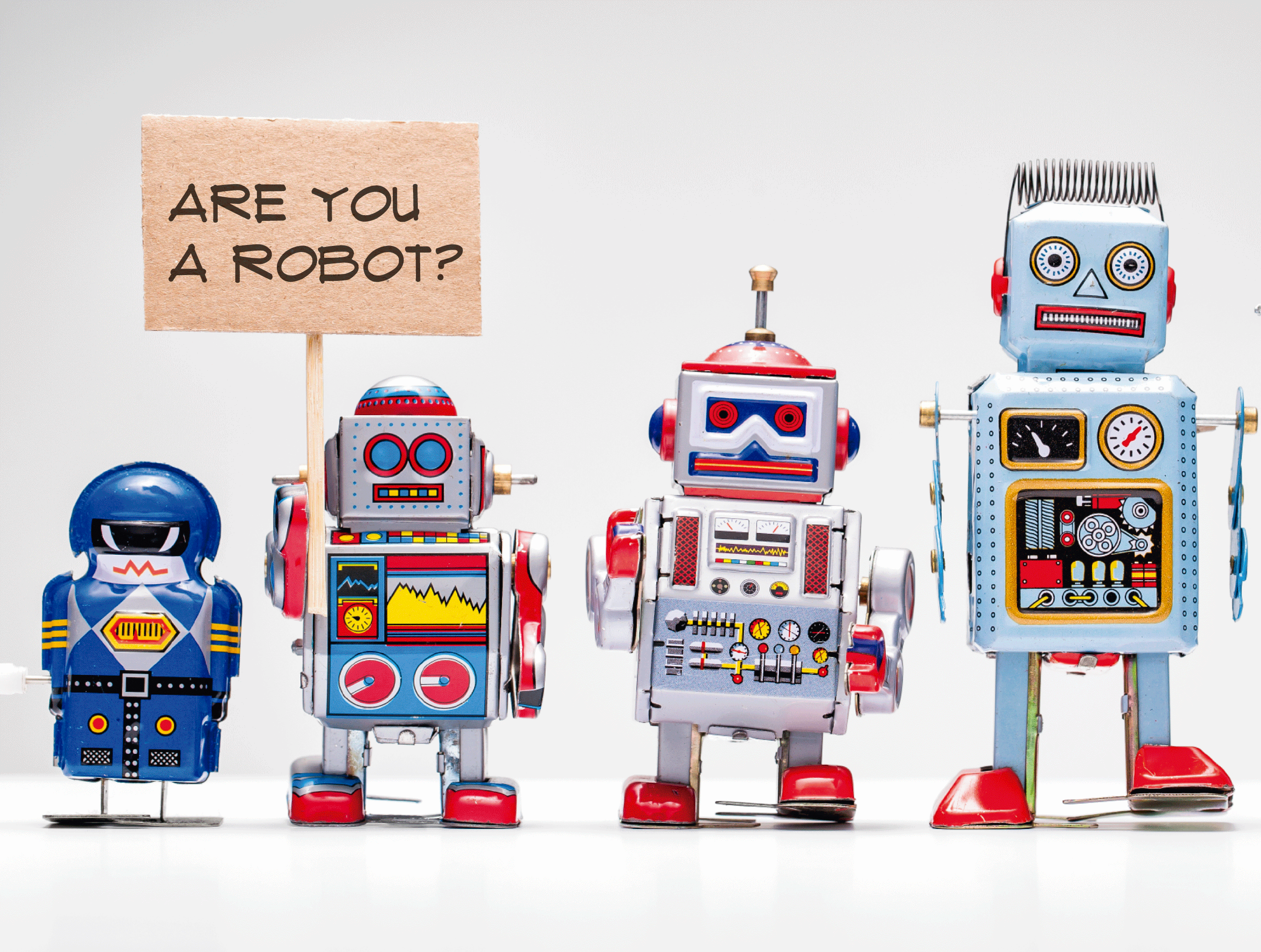
It’s easy to fool CAPTCHA
The program that keeps robots from doing something that should only be done by humans, is not foolproof. The race between humans and technology continues.
If you find a USB stick, resist the temptation to open it
Cyber-criminals are infecting our computers with malicious programs by using storage devices.
Tips to help shield your reading devices
Today, April 23rd, we celebrate World Book Day. Literature has evolved greatly in recent times, both in the way we enjoy it and the way…
your Smartphone is no longer the “smartest” option
Synching your Smartphone and computer might increase your chances of being hacked A classic piece of advice that helps keep email, social networks and other…