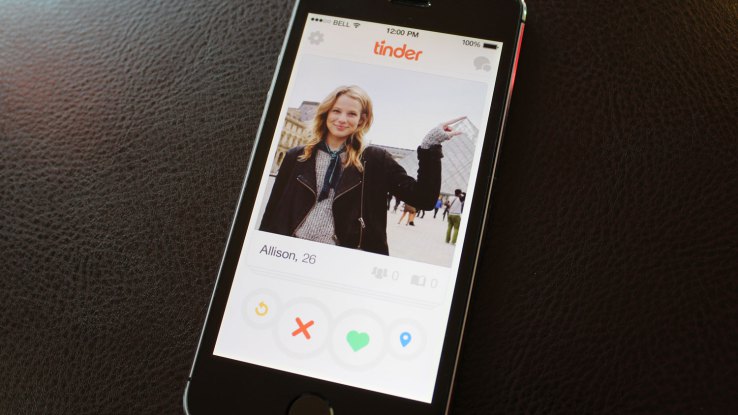
Tinder, the app where you can have your heart stolen, but also your information and your pictures
To find a ‘match’ in Tinder we have to share personal information with other users. If you don’t have at least one picture and you…
CryptoLocker: What Is and How to Avoid it
CryptoLocker is a family of ransomware whose business model (yes, malware is a business to some!) is based on extorting money from users. This continues…
8 things your kids shouldn’t do online
It’s not unusual nowadays to hear people say that if you want to know how to operate any technical device, ask a child, and they’re…
Adaptive Defense 1.5, the enterprise solution that seeks security against advanced and targeted attacks
Panda Security announces Adaptive Defense 1.5, the new version of the managed service that ensures security against Advanced Persistent Threats (APTs) and targeted attacks in…
Ugly Mail: How to know if your emails are being tracked
Someone is spying on your company’s emails. Probably in your office names like Yesware, Bananatag or Streak don’t ring a bell, but they know a…
WhatsApp: 6 scams you must pay attention to!
The success of WhatsApp has a downfall: while the instant messaging service reached 600 million active users last summer, the numbers of frauds emerging around…
What is Cloud Computing and how it will boost your business – Infographic
What is Cloud Computing Cloud Computing means storing and accessing data and programs in ‘the cloud’. This concept has been the basis of an entire…