The security and privacy of personal data is once again a cause of concern and debate for business organizations. With the new General Data Protection Regulation just weeks away, the latest cyber-security studies reveal that data theft incidents continue on the rise, with an average of 122 data records being compromised per second. What’s more, if you take a look at the data breach statistics recorded since 2013, you will realize that the number of data records lost of stolen over the last four years is over 9,740,567,988. From medical information to credit card numbers, from access credentials to information relating to purchasing habits, personal choices and opinions, this information is large enough to generate a huge database that could be exploited for social, financial and even electoral purposes.
Facebook, Equifax or MyFitnessPal
Although when talking about security breaches the first thing that usually comes to mind are attacks perpetrated by cybercriminals, it is important to focus on internal threats and oversights in companies’ own security as well. Over the last week we have seen how data breaches can hurt even tech giants such as Facebook, which is in the eye of a controversy storm for the alleged harvesting of data from more than 50 million users in order to favor President Trump’s election campaign.
Accidental data leaks, due to simple negligence, reached a disproportionately large number in 2017, with the Equifax case offering a prime example of the consequences of not protecting confidential data adequately. Last September, Equifax, one of the three major credit bureaus in the United States, was hit by a security breach affecting the personal information of 147.9 million customers, making this one of the biggest data breaches in history. The attackers got their hands on the victims’ names, social security numbers, home addresses and even driver’s license numbers, being able to access customers’ credit scores and financial profiles.
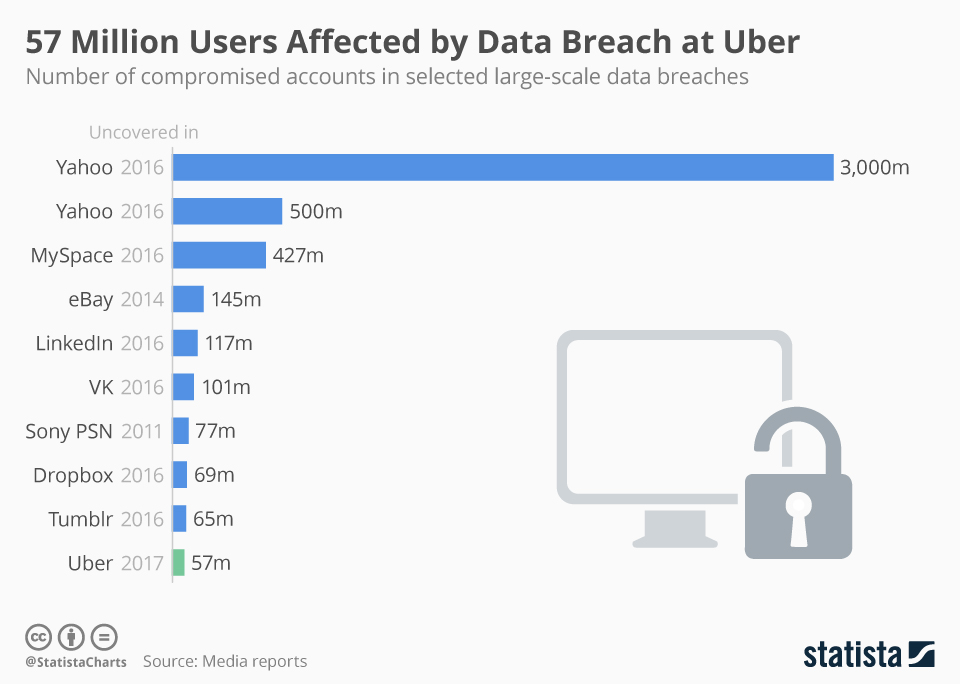
Unfortunately, this trend doesn’t seem like it will stop anytime soon. Sport clothing company Under Armour has suffered the largest data breach this year and one of the top five to date, based on the number of records compromised. The American company confirmed it had discovered on March 25 a potential data breach affecting 150 million users of its MyFitnessPal app and website.
Don’t be a victim of data theft
No one wants their company to appear in the news as the latest victim of a security breach due to the devastating impact it can have on their reputation, users and business. And even more so with the imminent entry into force of the GDPR on May 25. The purpose of this legislation is to protect the personal data of the EU citizens, monitoring how that data is collected, stored, and processed by organizations. Companies must take all necessary measures to ensure the proper levels of data security, traceability and management, including the application of the ‘Right to Erasure’, as failing to comply with the GDPR requirements can have significant consequences including fines of up to €20 million or 4 percent of an organization’s annual worldwide turnover.
To avoid being in that position, the first step is to be aware of the importance of implementing effective security measures and policies. Prevention in data processing activities is one of the basic requirements set out in the new Regulation. It’s very important to work with the necessary vision and anticipation to gain competitive advantage in business strategies.
Security solutions such as Panda Data Control are capable of discovering, auditing and monitoring the unstructured personal data stored across an organization: from data at rest to data in use and data in motion. They allow administrators to prevent uncontrolled access to the company’s sensitive data, ensure proper registration and traceability of personal information, and help comply with data protection regulations such as the GDPR or PCI-DSS.
The data monitoring capabilities provided by Panda Data Control are key to showing senior management, the DPO and the relevant authorities the strict control you have over the PII files found on your network. It is the ultimate tool for justifying any operation you must perform on that information: alteration, confirmation or deletion.
Don’t let your organization be in the headlines for the wrong reasons: find, monitor and control unstructured personal data across your network in real time, with one agent, and from one single solution with Panda Data Control.