To get rid of a computer virus:
Disconnect from the internet
Run an antivirus scan
Delete infected files
Update software and OS
Reboot in Safe Mode
Terminate suspicious processes
Use malware removal tools
Reset or reinstall OS if needed
Change passwords
Stay vigilant for future threats
Finding out that your computer or laptop is infected with a virus is a scary feeling. You may have important files on the hard drive, irreplaceable photos or an in-progress project that you forgot to save. Viruses, many caused by malware, can significantly impact your device’s performance and even threaten the safety of your personal information and data.
While antivirus software adds additional protection to your devices, you still need to be aware of viruses and their removal processes. Viruses are not a one-size-fits-all type of issue, and each can affect the performance of a phone or computer in a variety of ways.
If you think your device is infected, our guide can help you figure out how to get rid of a virus and restore your device’s productivity.
- What Is a Computer Virus?
- How to Get Rid of a Virus on Your Windows Computer
- How to Get Rid of a Virus on a Mac
- How Does Your Computer Get Infected With a Virus?
- Signs of a Computer Virus
- 6 Tips to Prepare for Virus Removal
What Is a Computer Virus?
A virus is usually a piece of tampered code that changes how a device functions and operates. Viruses can be passed from device to device through infected attachments or links, and they usually attach to and hide behind previously installed programs. Some viruses are referred to as worms, and these infections can spread to other devices without human interaction.
Many malware viruses use social engineering to attract and trap users, while others disguise themselves as helpful programs before penetrating an entire system — take, for instance, the heuristic virus.
Other types of viruses are common, including:
- File-infecting viruses
- Macro viruses
- Overwrite viruses
- Polymorphic viruses
- Resident viruses
…and more.
How to Get Rid of a Virus on Your Windows Computer
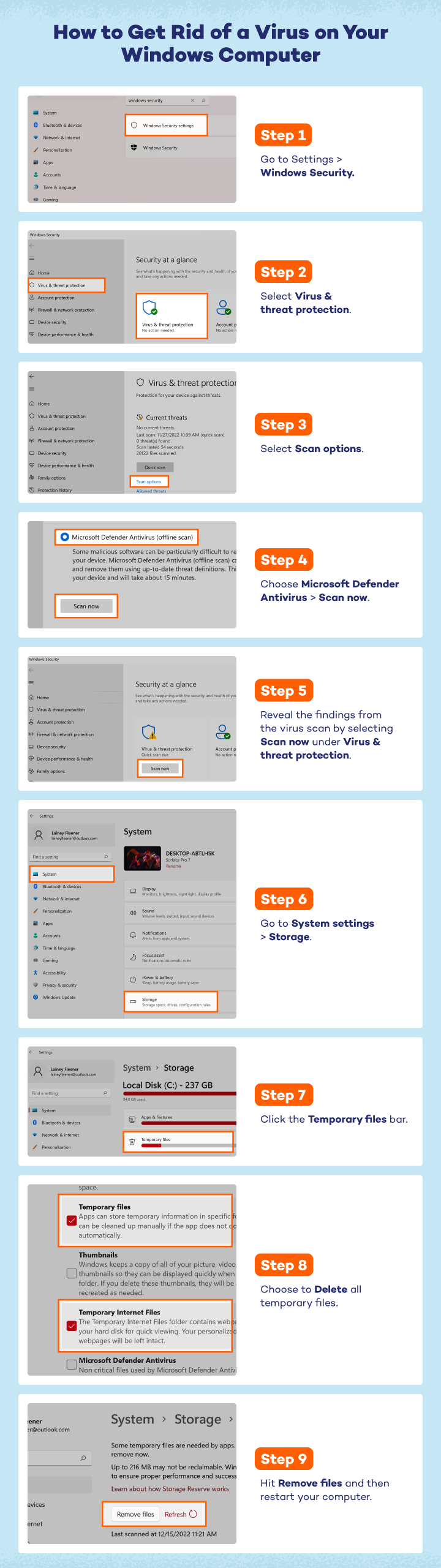
If you believe your computer may be compromised by a virus, your next step is computer virus removal. You will need to use Windows Security to remove the intruder.
- Open Windows Security. This can be accessed from the settings menu.
- In the left panel, select Virus & threat protection.
- Select Scan options.
- Choose Microsoft Defender Antivirus and then select Scan now. Your computer will restart and reboot in a safer, offline mode. After your PC restarts, navigate back to Virus & threat protection.
- Reveal the findings from the virus scan by selecting Scan now under Virus & threat protection in the middle panel. You can also access this history from Protection history on the right-hand sidebar. Then, restart your computer in Safe Mode.
- Navigate to System in the settings menu and select Storage.
- Click the Temporary files bar.
- Choose to Delete all temporary files.
- Hit Remove files. In regular mode, restart your computer.
After you have run a virus scan and deleted all temporary files, you can download and extract Autoruns. This Microsoft tool identifies malicious programs that should be deleted from your computer.
While most Windows systems have antivirus and antimalware software already installed, you may want to investigate your device’s protections and consider installing an antivirus system to help protect your device in the future.
How to Get Rid of a Virus on a Mac
While many people believe they cannot get viruses on Macs, these devices can also be infected. There are a variety of viruses posing as Mac antiviruses — including MacDefender and MacSecurity — that are malicious and dangerous. If your Mac has been infected, here is how to clean malware on your Mac.
- Navigate to the Applications Folder in Finder.
- Move any offending applications to Trash. After moving applications to trash, navigate back to Finder.
- Select Go in the top menu and then Go to Folder in the dropdown.
- Enter “/Library” in the search field and click Go. Drag any related or suspicious folders to the Trash.
- 5. Empty the Trash.
- Next, you’ll open the Launchpad by clicking on the icon with multiple colorful tiny square icons in the bottom toolbar.
- In the search field, type Activity Monitor and launch the program.
- Go to the CPU tab to view all running processes. Keep an eye out for any unfamiliar or suspicious process names by clicking the X in the top left corner.
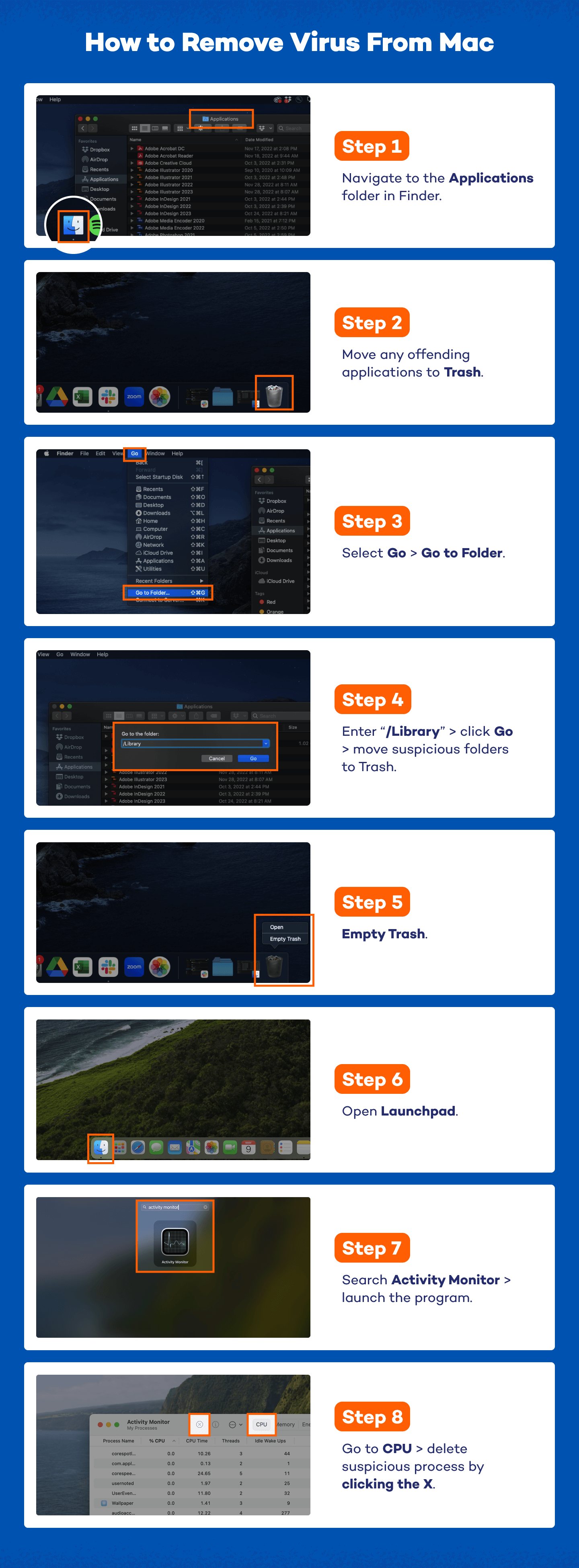
- If you identify a process that seems like malware, select it, then click the gray X in the top left corner of the Activity Monitor. Click Force Quit to terminate the process.
These are just a few simple ways to delete viruses from a computer without antivirus. If your computer has a virus that originated from a browser extension, you will need to delete these as well.
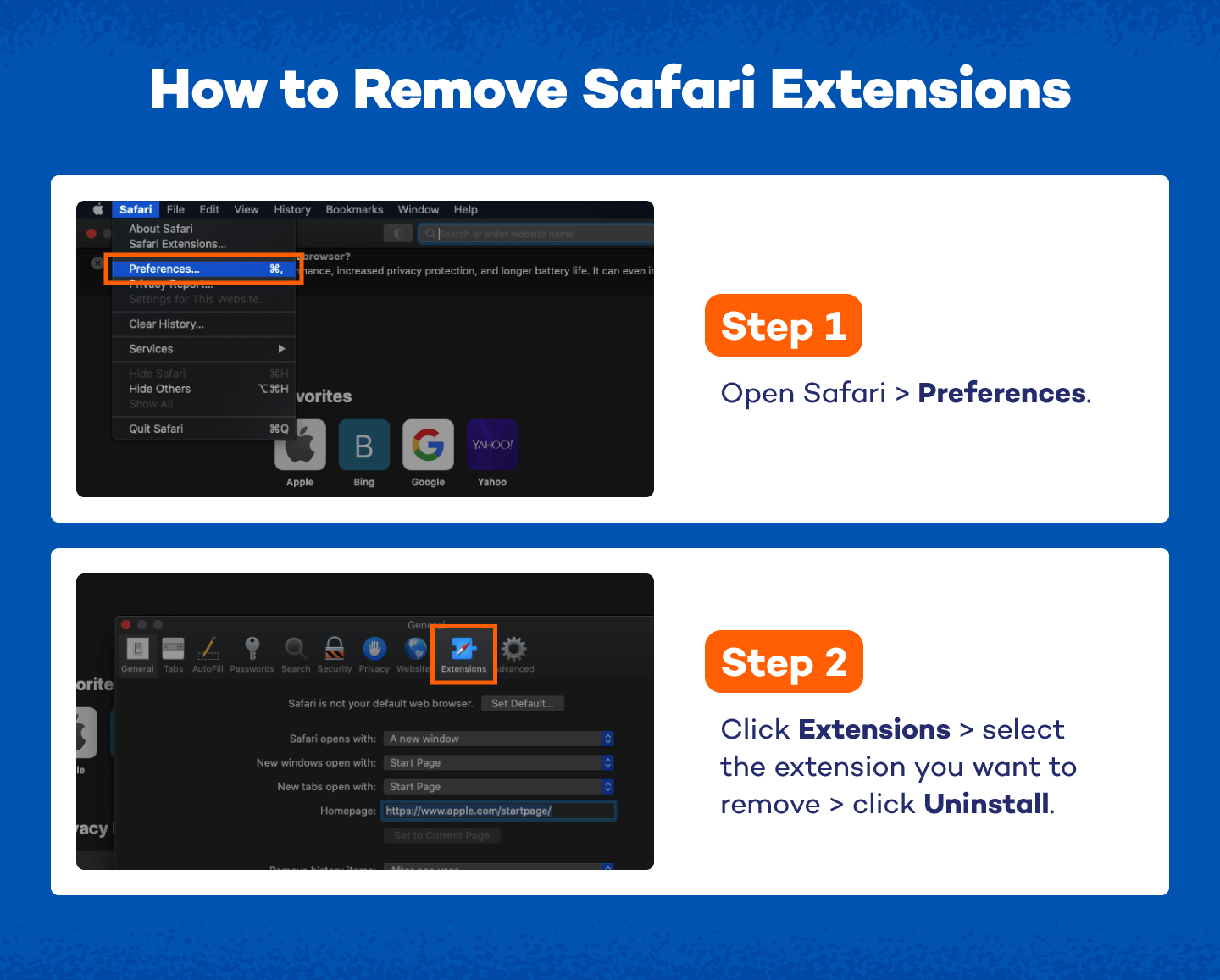
Removing Extensions on Safari:
- Open Safari and select Preferences from the top dropdown menu.
- Click Extensions. Here is where you will uninstall suspicious extensions. These could have been added by you or a piece of malware.
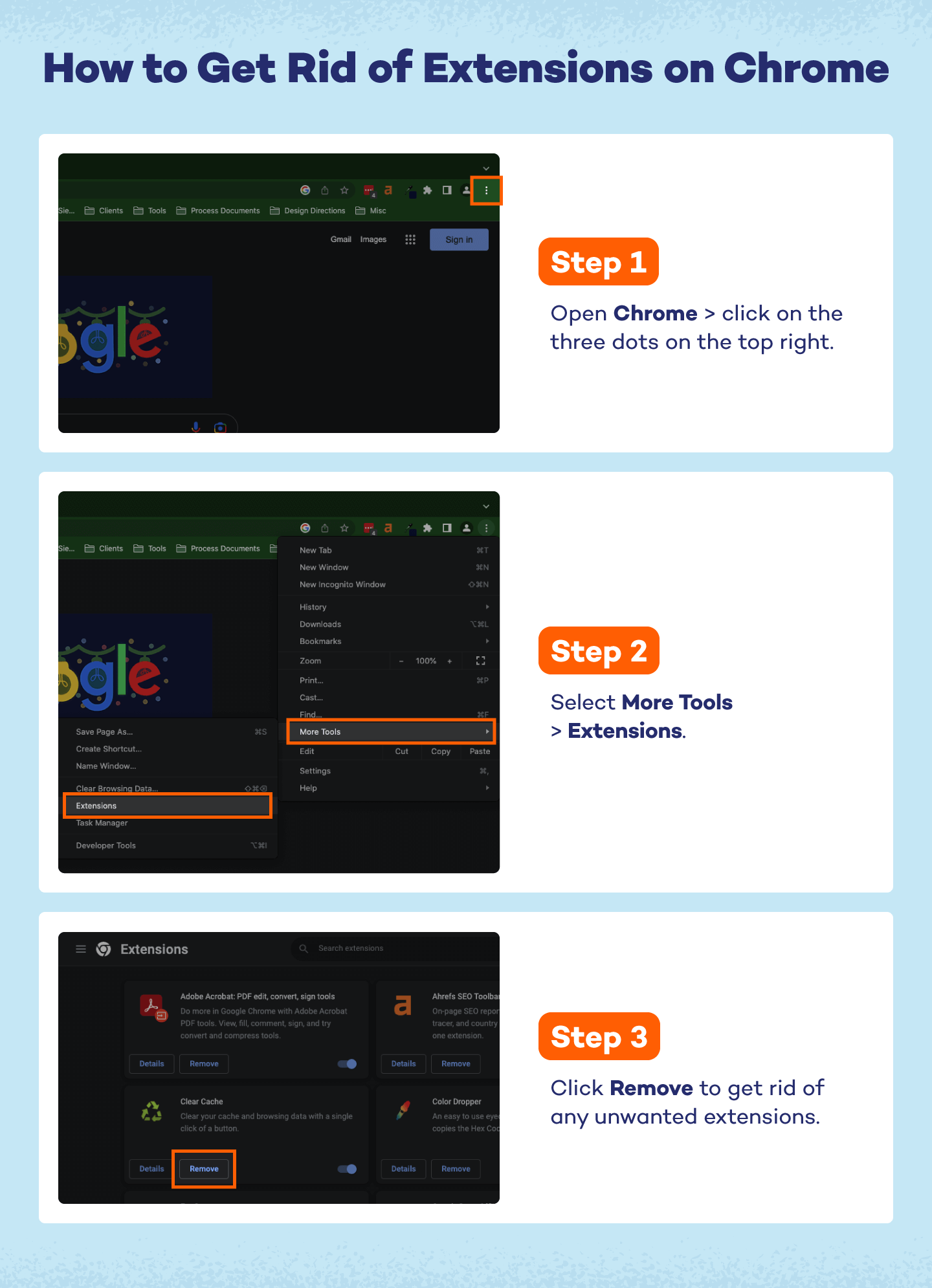
Removing Extensions on Chrome:
- Open Chrome and navigate to the three dots in the upper right-hand corner.
- Select More Tools and then Extensions.
- In the new screen, you can click Remove on any suspicious extensions.
In order to prevent a virus, be sure to download a secure Mac antivirus system on your computer. Additionally, it’s important to update your software as often as you can and back up your data regularly to ensure you will not lose previous files if ever infected with a virus.
How Does Your Computer Get Infected With a Virus?
Viruses are a common threat to computer systems, capable of causing significant damage to data, software and even hardware. Understanding how these harmful programs gain access to your computer is crucial for maintaining a secure system.
Here are some of the most common ways a computer can get infected with a virus:
- Email attachments: Opening email attachments from unknown or suspicious sources can lead to infection. Malicious attachments can contain viruses or other types of malware designed to compromise your system as a part of phishing scams.
- Infected downloads: Downloading files or software from untrustworthy websites can be risky. Hackers often hide viruses within seemingly harmless downloads like freeware, shareware or cracked software.
- Compromised websites: Visiting malicious or compromised websites can lead to automatic downloads of harmful software. These sites often use scripts or pop-ups to infiltrate your computer without your knowledge.
- Vulnerabilities in software: Operating outdated systems can have security flaws that allow viruses to enter. Hackers exploit these vulnerabilities to inject malicious code into your system.
- Removable media: Inserting infected USB drives or other removable media into your computer can introduce viruses. These devices may carry malware from other systems they’ve been connected to.
Signs of a Computer Virus
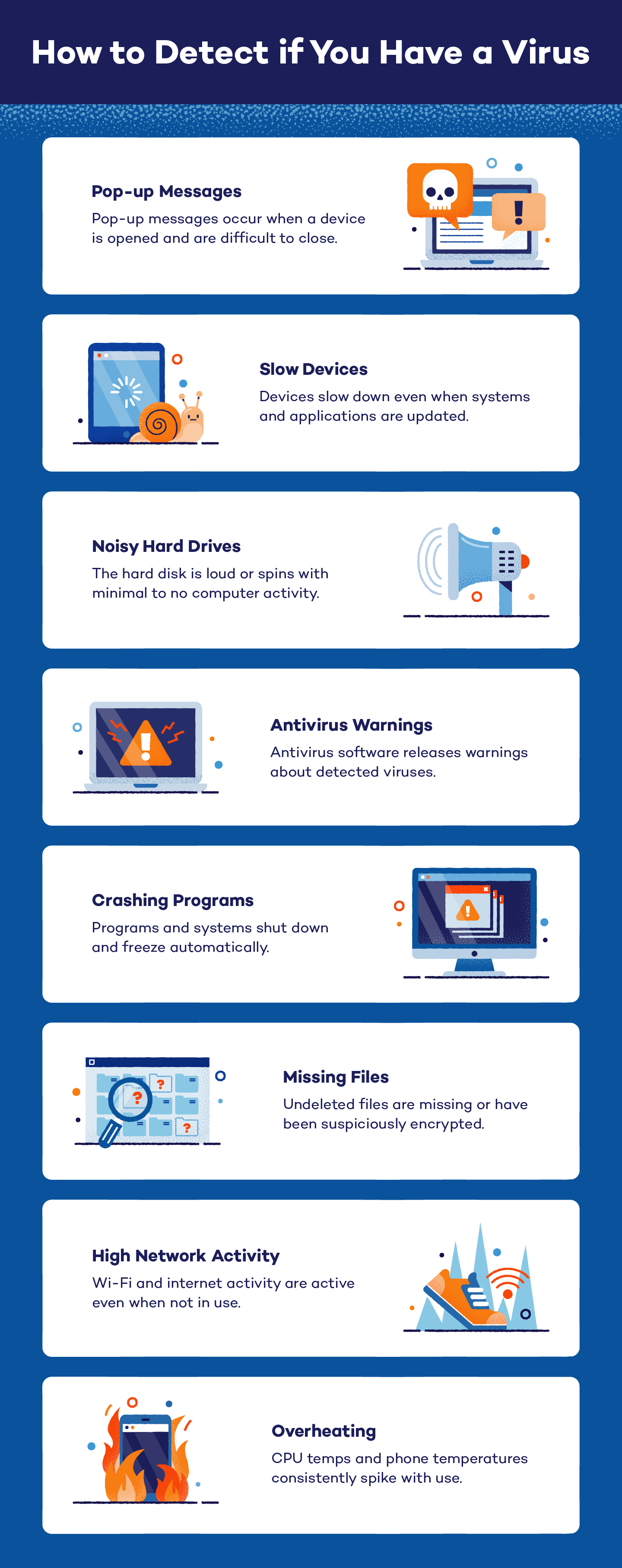
Before you begin the virus removal process, double-check that your device’s symptoms are characteristic of viruses. A few telltale signs that your computer or phone may be infected are:
- Pop-up messages are appearing. If pop-up messages appear every time you use your device or they are hard to close out of, you may have a virus. Never click on a suspicious pop-up if you think your device may have a virus, even if it’s a virus warning.
- Your device is running slowly. Make sure all of your applications and systems are up to date. If you are unable to increase its speed, it may be experiencing the side effects of a virus that is hijacking your device.
- Your hard drive is making noise. If your hard disk is making continuous noises or spins with minimal to no computer activity, your device could have a virus.
- Programs are continually crashing. If programs are starting and closing automatically, or your system randomly shuts down or freezes, your device could be infected by a virus.
- You have missing files. If you are missing files that you know were not deleted, this may be due to malware. Some malware deletes, moves or encrypts files so you cannot open them.
- High network activity. If your Wi-Fi or internet activity is active even when you are not using it, a virus could be infiltrating your internet to send and steal information.
- Your device overheats. If your device has a virus, it is most likely working overtime to keep things running smoothly. This can cause overheating in phones and computers. Keep an eye on your CPU temps and how hard your device’s fans are working.
- Warnings are being released by your antivirus software. If you have antivirus software installed, don’t ignore its warnings. This could be a sign that your device is compromised.
6 Tips to Prepare for Virus Removal
Even after you’ve detected a virus, there’s preparation to be done before jumping into virus removal. To ensure that all internal and external files have been cleaned, it’s important to keep every possible removal method accounted for and prepare your devices to get rid of a virus.
- Scan personal data: Before beginning the virus removal process, scan all your personal data for viruses. This will ensure that viruses aren’t accidentally reinstalled after the removal process. Scanning tools like the Panda Cloud Cleaner can help disinfect your PC quickly.
- Reboot Safe Mode: A virus can only access your device when it’s running. When placed in Safe Mode, your device will only load the essential files, which can stop all viruses from starting.
- Use a rescue USB drive or rescue disk: A rescue USB drive allows you to scan a device without starting it. This helps keep viruses contained and provides you with an additional safe space to scan for viruses.
- Don’t forget manual removal: You may need to view and delete program files manually to get rid of a virus. If you feel comfortable, download Autorun, which allows you to see exactly what it is that is operating on your computer and how to get rid of it. This type of virus removal can be overwhelming, so be sure you’re prepared to determine the legitimacy of your programs before beginning.
- Employ clean install: If all else fails, it’s possible to resort to a clean install. A clean install deletes everything on your hard drive, but it also almost always guarantees the removal of viruses and malware. You will have to reinstall all programs, but it can save your computer from further infiltration and destruction due to viruses
- Install antivirus software: Make sure to install an antivirus system that also protects against ransomware, as programs with both can detect things an antivirus program alone does not recognize.
While viruses can be scary, they can also be removed. Cleaning up your device may take some time, but Panda Security offers users a variety of tools to help simplify the process and get your personal devices running again.









4 comments
French version? Pls
Hello Arnaud,
We will soon have a French version of our blog.
We are sorry we cannot offer it right now.
Thanks!
Good info , simple explain . Well done,thankyou.
Thanks for sharing this is very helpful for me.