There are almost no electronic devices that are invulnerable to hacks and malware. While very complicated and unlikely, iPhones can be hacked in a multitude of ways.
Over the years, we’ve seen Apple products encounter their fair share of exploits and hacks that capitalize on iOS software vulnerabilities. Being a victim of iPhone hacks isn’t impossible, and it’s important to know how these exploits work so you can reduce the risk of being targeted. We’ll explore the digital threats iPhone users should be aware of, the warning signs to look out for and what to do if your iPhone gets hacked.
Can iPhones Be Hacked?
iPhones are more secure mobile devices than their Android counterparts, but they can still be hacked. Android devices have a reputation for customization and manipulation at the software level since their open-source code makes them much less secure and easier to compromise via malware. iPhones, on the other hand, are closed-source, making them far more challenging to compromise.
Despite their superior security features, iPhones are still susceptible to unsecured Wi-Fi network traps, suspicious apps and social engineering schemes. While rare, iPhone virus threats exist.
Some iPhone hackers attempt to exploit security vulnerabilities the iOS can’t prevent, like exploiting apps to gain elevated permissions. Others try to access your device by hacking or logging in using your Apple ID, giving them better access privileges.
From there, the hacker can access all data on the iPhone, including cloud storage, pictures, messages and sensitive financial and personal information.

How to Tell If Your iPhone Is Hacked
No one knows your iPhone better than you. If you notice your device behaving in strange and unusual ways, your iPhone may be hacked. Here are some warning signs to pay attention to.
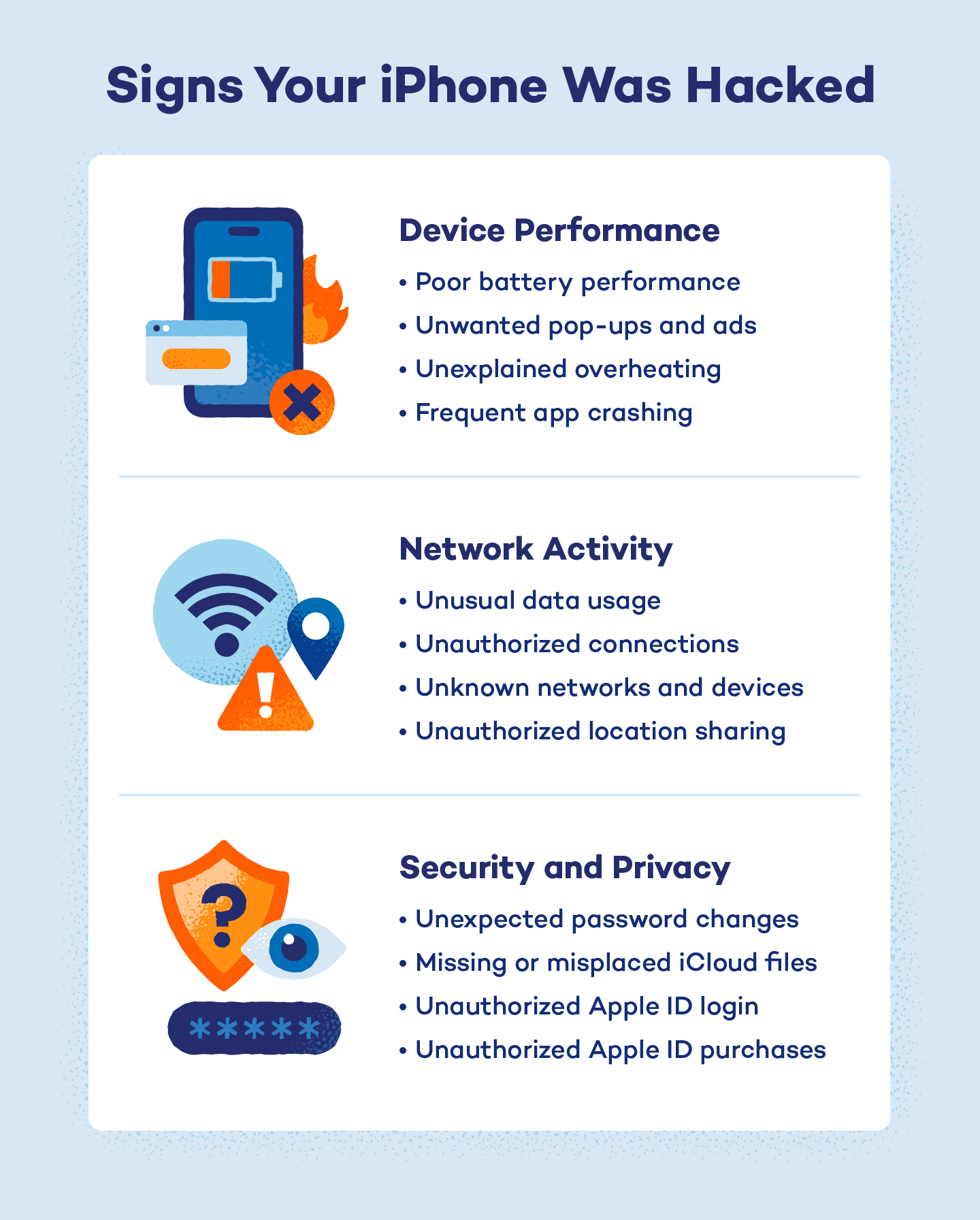
Device Performance
Malware can affect your iPhone’s performance negatively. Some of these signs can be attributed to poor condition or aging technology, but if your phone is in great condition and still underperforms, it’s possible that it’s been hacked.
- Battery drains quickly: Hacked iPhones are unable to hold battery power as long as they used to. Be warned that this is also a very common sign of your iPhone aging, so check your battery life to verify if it’s a hardware problem — sometimes your iPhone just needs a new battery.
- Unexplained pop-ups or ads: Uncontrollable pop-ups and ads are a clear sign that, at the very least, your iPhone browser has come in contact with a suspicious site. Pop-ups are the scourge of online phishing and may require deleting website data to get rid of them.
- Apps crash frequently: It’s not unusual for apps to misbehave, but frequent crashing may indicate the presence of malware hindering your device.
- Device is overheating: Overheating can also be a sign of an aging device, but newer iPhones likely won’t exhibit this problem. If your iPhone is overheating when it’s not running a lot of apps or without being used, you may have been hacked.
Network Activity
A lot of hacks attempt to establish communication between the source and your iPhone. Network activity can be a sign of active malware communicating with its source on the internet.
- Unusual network activity or data usage: A lot of hacking threats are related to network activity, like unsecured Wi-Fi networks. Avoid public networks when possible and only connect to secure networks to keep your device safe. If you notice that you’re using more data than you’re supposed to or that there’s unusual network activity like location sharing when you’re connected to a network, your device might be hacked.
- Suspicious outgoing connections: Pay attention to what your iPhone connects to, including other devices, networks, hot spots and Bluetooth devices. If your device keeps connecting to an unknown source, a hacker may be attempting to access it. Any automatic connection to devices you’ve never manually approved can be a sign of a hacked iPhone.
Security and Privacy
Your security and privacy settings are the last line of defense against hackers. If you realize that there’s activity on your account changing or disabling your security settings, you might be getting hacked.
- Unauthorized changes to security settings: Hackers can change your settings remotely if they have access to your Apple ID. Their first move could be changing your security settings, like your passwords, so that your device is no longer accessible to you. If you find that you’ve been locked out of your Apple ID, someone likely gained access to your account and changed the login information.
- Unexplained iCloud or other account activity: If you notice that your iCloud has been deleted, moved or locked, it’s possible that a hacker gained access and manipulated your data.
In the case of unauthorized access, your priority is to secure your data and personal information as soon as possible. If you receive an email from Apple about someone signing into your account, changing passwords or buying products, you need to gain control of your Apple ID and secure it. You can also quickly check who has access to your iPhone and your other Apple devices.
What to Do If Your iPhone Is Hacked
If you think your iPhone or Apple ID has been compromised, remember that you have a short amount of time to secure your account before you’re locked out or your data is stolen. Here’s what to do:
- Disconnect and power off your device: Turn off your Wi-Fi, Bluetooth and cellular data. Then, disconnect the iPhone from any accessories or wired connections and power it down.
- Remove external components: Take out your SIM card and any external storage or charging devices.
- Access your Apple ID: Use another device to access your Apple ID account. Then, reset your Apple ID password and check for any unknown connections. Immediately change passwords for all accounts linked to the device.
- Enable two-factor authentication: Add an extra layer of security to your accounts where possible.
- Check your iPhone settings: Check the settings for services or apps you’re signed in to with your Apple ID. To do this, open the Settings app on your iPhone. Tap your name and verify the email address associated with your Apple ID.
- Contact your service provider: Inform your cellular service provider about the hacking incident and verify if there were any purchases or suspicious charges on your service provider’s app.
- Use a reliable VPN: Secure your online activity on all devices by using a reliable VPN service and browse the internet safely while protecting your personal information.
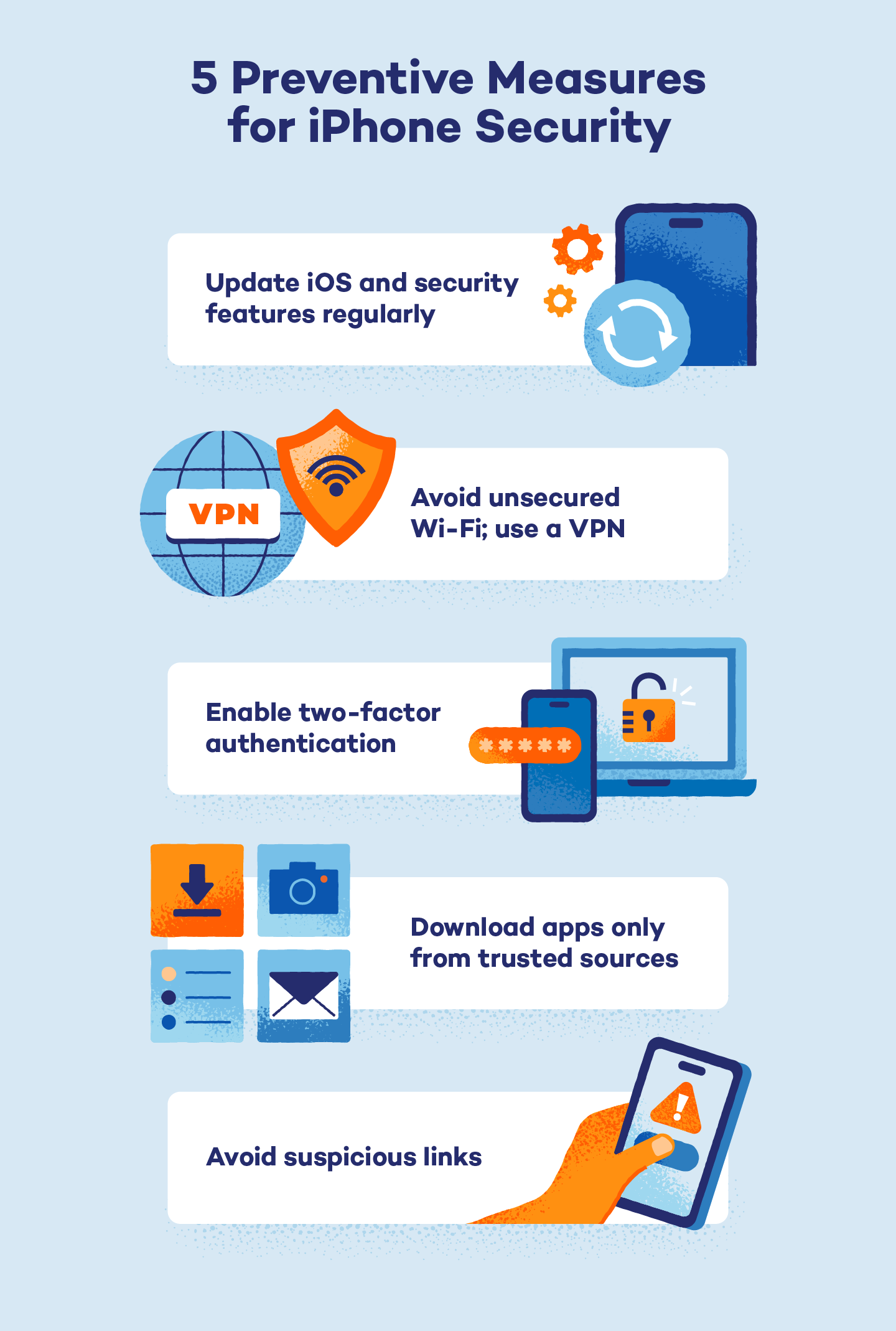
Preventive Measures for iPhone Security
To keep your iPhone safe, it’s important to enable all security features at your disposal. Apple has built its suite for optimal access so that all your Apple devices are connected to your account. This can be scary if your device or account is compromised.
- Keep software up-to-date: Make sure you have the latest software version installed on your devices. It’s best to enable the automatic update feature so it notifies you when it’s ready to install.
- Enable two-factor authentication: Two-factor authentication is a pretty reliable method for immediate verification. This helps make sure you’re the only one with access to your device.
- Use strong passwords: Create complex passwords that aren’t easy to guess, and use different passwords for different accounts.
- Avoid unsecured networks: Avoid connecting to unsecured or public Wi-Fi networks. Use a VPN for an extra layer of online security.
- Avoid suspicious links: iPhones aren’t immune to suspicious links that may lead to malware, phishing schemes and a host of other digital threats. Avoid suspicious and unfamiliar links at all times and practice safe browsing habits to remain secure.
iPhone Hacking FAQ
Know how iPhones can be compromised to keep your personal information from being stolen and used.
Can Hackers Watch You Through Your iPhone?
Yes, but only if you’ve given an app permission to access your camera. There are also hacks in which your phone is mirrored and intruders can watch what you do on your phone.
Can Anyone Hack My iPhone Using My Phone Number?
No, your iPhone can’t be hacked using your phone number. If a hacker has access to your Apple ID, they can gain access to your devices, but a phone number isn’t enough to hack you.
No device is impervious to hacking, digital threats or social engineering. The iPhone offers a well-rounded list of security features, but even with these features in mind, safe browsing can be the difference between safe online browsing and falling for phishing schemes. Using a reliable VPN service can help mask your digital signature and keep you secure while you browse.