iPhones generally don’t need antivirus software since Apple’s operating system provides solid security protection from viruses on iPhones. However, iPhones that are jailbroken, missing an update or have certain features disabled are vulnerable to viruses and could benefit from antivirus protection.
Apple products are regarded as some of the most secure devices currently on the market. Designed with an array of security programs, tools and features, you may be wondering, “Do iPhones need antivirus software, too?”
Apple’s operating system (iOS) provides iPhones and other Apple devices with security features that make it extremely difficult for malware to infiltrate. However, if the phone has been tampered with, it may be worth taking additional security measures to protect your devices, such as installing antivirus software.
Keep reading to learn more about iPhone viruses, other potential iPhone threats and how to protect your device.
Can iPhones Get Viruses?
Like any computer, an iPhone can catch a virus. Viruses work by infiltrating systems, attaching to programs, replicating themselves and attaching those copies to further programs. This allows them to communicate, steal data and cause damage.
iOS is a closed ecosystem that restricts communication between programs and requires all applications to be approved by the App Store. These restrictions make it difficult for viruses to communicate and spread. If the original operating system is tampered with, however, like if the iPhone is jailbroken or doesn’t have the latest update, the phone becomes vulnerable to virus attacks.
What Viruses and Other Threats Affect iPhones?
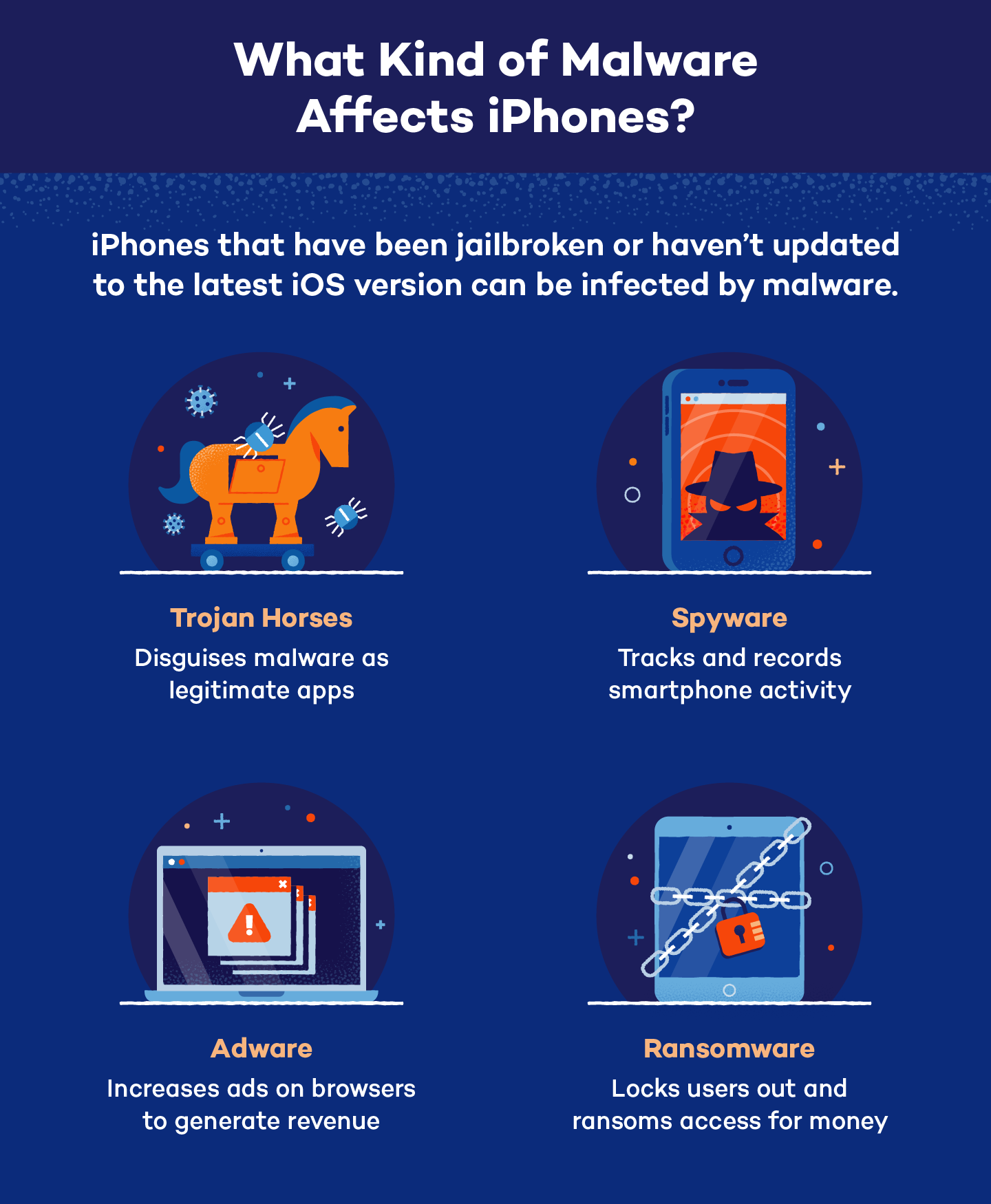
A virus is just one type of malware that can be found on an iPhone. There are many types of iPhone viruses and other cyberthreats that could affect your device if it has weakened security, including:
- Ransomware: a malware program designed to lock users out of their device in order to hold access to it at ransom for a sum of money
- Phishing: the act of sending fraudulent messages with suspicious links in ads, messages, calls, voicemails, emails, or websites to users with the intent of stealing their identity or other personal information
- Data breaches: the illegal access of a device with the intent of stealing private or sensitive information
- Spyware: a malware program that records a user’s actions, such as calls, texts, locations, images, video, keystrokes and browsing history, to obtain sensitive information
- Adware: a program that causes incessant pop-up ads while using a browser, generating revenue for developers every time a user interacts with it
- Trojan horses: programs that are disguised as innocent apps that deploy malware onto devices once downloaded
Although these different attacks have similar characteristics, such as the information they’re seeking or the channels they use to infiltrate your device, it can take a stockpile of protective features to combat them all at once.
How to Detect Viruses on iPhones
Viruses often remain unseen and undetectable, making it difficult to remove them. Many users may not even be aware that there is a virus on their iPhone.
However, there are several red flags that can indicate an iPhone has a virus, including:
- Overheating: Malware can cause undetectable apps, widgets or programs to continuously run in the background, causing the processor to run heavily, overheat and possibly shut down.
- Excessive data usage: Similar to overheating, malware running programs in the background may also use data to stay connected to outside networks.
- Pop-ups: If pop-up ads appear while you are browsing on Safari warning of a virus infection, it’s not an official Apple notification — Apple does not use pop-ups for system warnings, and interacting with the ad can lead to further contamination.
- Unknown or suspicious apps: Apps that appear on iPhones that you haven’t downloaded or that didn’t come preinstalled may have been downloaded by cybercriminals.
- Drained battery life: Like overheating and data use, malware that causes background programs to run can use up power and drain batteries.
Of course, these signs do not always mean that an iPhone is infected. They may instead indicate that the phone is simply outdated, broken or old. However, because an iPhone virus scan tool is not preinstalled, the root of these issues can be difficult to determine. The most effective way to take care of your device is to be proactive with safety measures.
Do iPhones Have Built-in Security?
Apple’s reputation of being the most secure brand of smartphones and computers is in part due to its multitude of built-in safety features and programs for its devices. However, if something happens to impair these features, such as missing an update, damaging the phone or accidentally turning a feature off, the iPhone would once again remain exposed to viruses and other threats.
Here’s a list of preinstalled Apple tools and features to keep in mind while thinking about your phone’s security.
Fraudulent Website Warning
Fraudulent Website Warning is a Safari setting that indicates if the website you’re trying to visit is suspected of phishing. If Safari determines that the site is imitating a legitimate business in an attempt to steal your personal data, it will warn you and prevent access to the site.
Two-factor Authentication for Apple ID
The Apple ID two-factor authentication feature was released in 2015 and is now a staple across almost every Apple ID account. Only usable with an additional device, users are required to log in by first entering their password and then inputting a six-figure code that’s automatically sent to a trusted or previously authenticated second device.
iCloud Private Relay
Similar to a VPN, iCloud Private Relay is an Apple service designed to hide private web browsing data that can be used to reveal personal information, such as browsing history and IP locations. However, iCloud Private Relay saves part of your information on the Apple server, making the service less private than other secure VPNs.
Mail Privacy Protection
Created for the Apple Mail app, Mail Privacy Protection is a service that prevents scammers from tracking your email activity. This could include your IP address, the times you’ve interacted with a message and the actions you’ve taken with it. However, this feature is limited to the Mail app and cannot be enabled on third-party mail apps.
Additional Virus Protection for iPhones
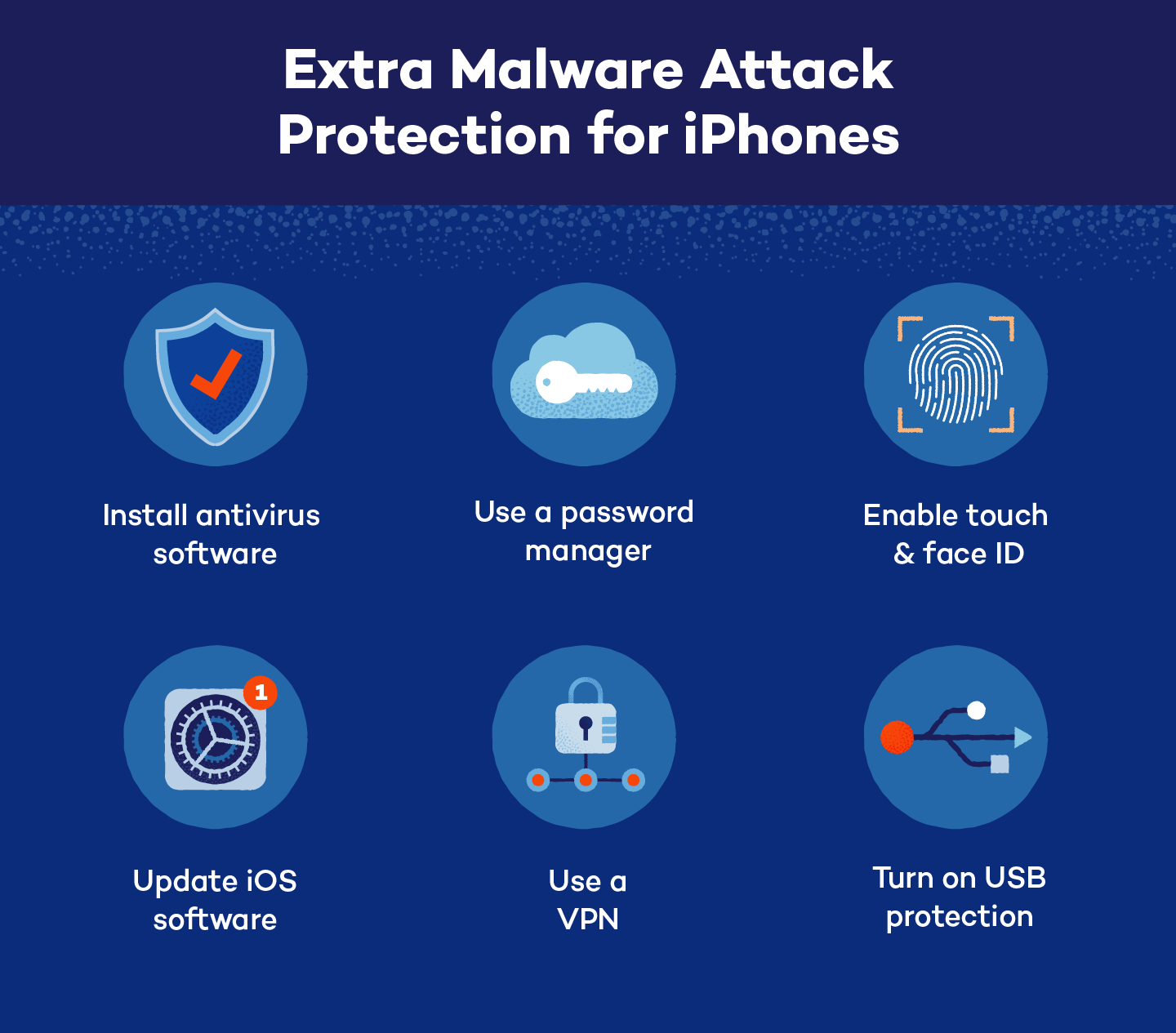
For those looking to take the extra step in protecting their smartphone against viruses, malware and other digital attacks, consider:
- Installing antivirus software: Almost any electronic device can be attacked by malware. Installing antivirus software for desktops or phones can improve security and lower the risk of one device infecting others.
- Updating your software: Enabling automatic iOS updates will help keep your phone’s security programming up-to-date and prepared to fend off the latest types of malware attacks.
- Setting up a password manager: Password managers provide additional layers of protection for passwords, including enhanced encryption, password organization and password generation.
- Enabling touch or face ID: Similar to using password managers or two-factor authentication, using touch or face IDs makes it difficult for hackers to enter accounts without physically being present.
- Using a VPN: Many iPhones have automatic Wi-Fi connection settings enabled, making a VPN a key tool in protecting your location and data while browsing the internet with your smartphone.
- Turning on USB protection permissions: USB permissions protect phones that are plugged into public USB ports from being “juice jacked,” or having malware installed while it’s being charged so that the system can be accessed remotely.
Despite Apple’s best efforts, hackers will continue to find ways around its safety and privacy technology. And although you may not need it now, it is possible that there will soon be a time when you question whether your iPhone needs antivirus support to stay secure.
Of course, smartphones are not the only Apple products at risk. It’s important to remember to also protect Mac desktops from viruses with effective software. Ensure your entire digital landscape is protected with a Panda Dome Premium antivirus service plan today.
iPhone Antivirus FAQ
So, do iPhones need antivirus protection? If you still have questions about iPhone security, check out the answers to common questions below.
Can iPhones Get Hacked?
iPhones can get hacked just like any other mobile device. While Apple devices are generally much more secure than their Android counterparts, it’s still possible for iPhones to fall victim to cyberattacks. Keep your iOS updated and follow the other protection tips above for optimal device safety.
Do iPhones Need Antivirus Software?
If your iPhone is jailbroken, your device is much more vulnerable to viruses and other cyberthreats, so you will likely benefit from a mobile security app. However, the best defense against iPhone viruses is keeping your iOS up-to-date and using your device responsibly.
Do Macs Need Antivirus?
Yes. While Apple’s OS provides sound security, Macs can still benefit from antivirus protection. And like iPhones, you’ll want to practice safe online habits and download the latest OS updates to keep your computer secure.






1 comment
Hope you can help a senior on a fixed income get free antivirus software for free