To encrypt emails in Gmail and Outlook, use the built-in S/MIME encryption protocol.
Gmail:
1. Enable hosted S/MIME.
2. Compose your email.
3. Click the lock icon next to the recipient’s name.
4. Select “View details” to adjust S/MIME settings.
Outlook:
1. Go to File > Options > Trust Center > Trust Center Settings.
2. Under Email Security, check “Encrypt contents and attachments for outgoing messages.”
3. Click Settings for additional options.
Email encryption is the process of disguising the content of your email messages to protect them from being read by unwanted parties. Sensitive information such as Social Security numbers, passwords, login credentials and bank account numbers are vulnerable when sent via email.
When encrypting emails, it’s important to encrypt all of them — not just the ones with sensitive information. If only some of your emails are encrypted, it is an open invitation for a hacker and could make your inbox even less secure. They will only have to hack into a few emails rather than sift through hundreds to find data they can use. Learn how to encrypt emails on multiple providers and stay safe.
What Is Email Encryption?
Email encryption is a way of securing email messages by transforming their contents into an unreadable format that can only be decoded by authorized recipients. This ensures sensitive information remains confidential, even if intercepted during transmission.
Encryption relies on public key infrastructure (PKI) to encrypt and decrypt messages. Each user is assigned two keys:
- Public key: It’s stored on a public key server and is accessible to anyone. When someone sends you a secure email, they use your public key to encrypt it.
- Private key: It’s safeguarded on your computer or device and is accessible only to you. This key is essential for decrypting emails you receive.
You can also use your private key to create a digital signature, verifying to recipients that the email genuinely came from you.
Why Is Email Encryption Necessary?
Email encryption is crucial for safeguarding sensitive information from cyberthreats, particularly data breaches . When your emails are encrypted, even if a hacker intercepts them, they cannot access the contents without the decryption key. This makes the information useless to attackers and helps protect your privacy.
The importance of encryption is underscored by the alarming rise in data breaches. In the first quarter of 2023 alone, over 6 million data records were exposed. Such incidents are costly, with the average global cost of a data breach reaching $4.45 million in 2023 — a 15% increase since 2020.
By encrypting your emails, you’re taking a proactive step to prevent your information from becoming part of these cybersecurity statistics and to mitigate potential financial and reputational damage.
Types of Email Encryption
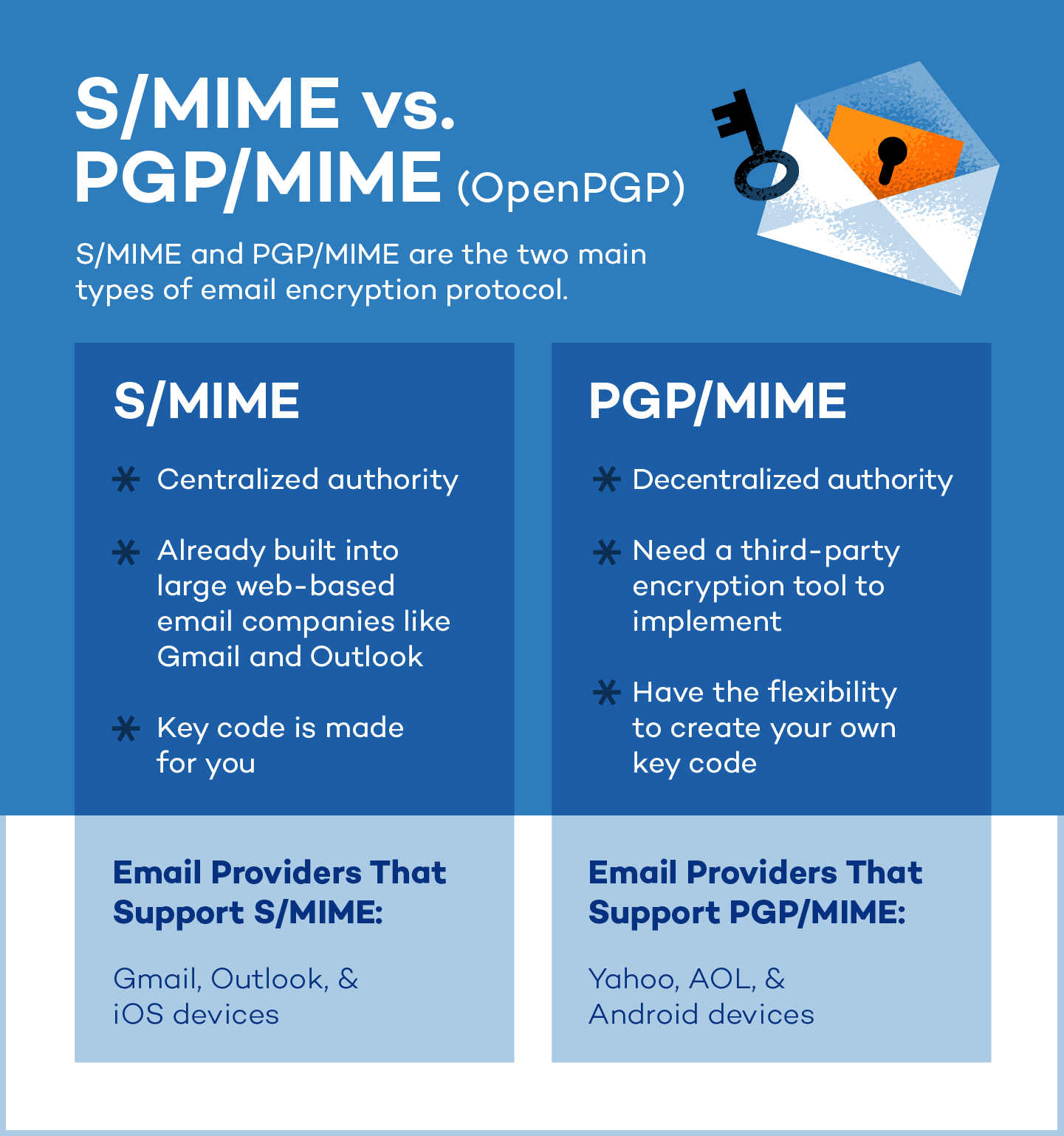
The two main types of email encryption protocols are Secure/Multipurpose Internet Mail Extension (S/MIME) and Pretty Good Privacy/Multipurpose Internet Mail Extension (PGP/MIME).
Both models work by way of user key exchange — the sender and receiver each have a public and private key for encrypting and decrypting messages. We’ll look at each type more in depth below.
S/MIME
S/MIME is built into most iOS devices and relies on a centralized authority to pick the encryption algorithm, issuing certificates to encrypt and “sign,” or verify, email messages.
S/MIME is used most often because it is built into large web-based email services, such as Gmail and Outlook , and can secure plain text messages and attachments. It is most common for industrial or commercial use.
PGP/MIME
PGP/MIME relies on a decentralized trust model and was developed to address security issues facing plain text messages.
Within this model, there is more flexibility and control over how well you want your emails to be encrypted, but it requires a third-party encryption tool. PGP/MIME is most common for personal or organizational use and is compatible with Android devices. It can also be used in VPNs , whereas S/MIME cannot.
Transport Layer Security (TLS)
TLS is a cryptographic protocol that ensures secure communication over a network by encrypting data exchanged between two parties. TLS is commonly used to safeguard sensitive information such as email content, login credentials and financial transactions.
Unlike S/MIME and PGP/MIME, which encrypt the content of emails, TLS focuses on securing the transmission process. It plays a critical role in maintaining data privacy by verifying the authenticity of communication parties and encrypting data in transit. This prevents tampering, eavesdropping and unauthorized access.
 How to Open Encrypted Email
How to Open Encrypted Email
Opening an encrypted email typically requires specific tools or keys to decrypt the message securely. The process depends on the encryption method used: S/MIME, PGP/MIME or a platform-specific service.
For S/MIME encrypted emails:
- Ensure you have an S/MIME certificate installed on your device.
- Use an email client or platform (eg, Outlook or iCloud Mail) that supports S/MIME.
- Open the email, and the client will automatically use your private key to decrypt it.
For PGP/MIME encrypted emails:
- Install a PGP-compatible tool or plugin, such as Gpg4win or OpenPGP.
- Import your private key into the tool.
- Open the email in your client, and use the tool to decrypt the message.
For platform-specific encryption like Gmail confidential mode:
- Follow the instructions in the email to verify your identity, such as entering a passcode sent via SMS.
- Click the provided link to view the email in a secure browser window.
How to Encrypt Email
Now that you know what email encryption is and what it does, how do you actually encrypt your emails? Here are various ways to encrypt your email in popular platforms like Gmail, Outlook and other email services.
How to Encrypt Emails in Gmail
Gmail already has S/MIME built into the app, but it only works if both the sender and receiver have it enabled.
- Enable hosted S/MIME. You can enable this setting by following Google’s instructions on enabling hosted S/MIME.
- Compose your message as you normally would.
- Click on the lock icon to the right of the recipient.
- Click on “View details” to change the S/MIME settings or level of encryption.
When changing the encryption levels note these color codes:
- Green: Information is protected by S/MIME encryption and can only be decrypted with a private key.
- Gray: The email is protected with TLS. This only works if both the sender and recipient have TLS capabilities.
- Red: The email has no encryption security.

How to Encrypt Emails in Outlook
Outlook is also compatible with the S/MIME protocol, but it requires additional setup.
- Enable S/MIME encryption. This process will involve getting a certificate or digital ID from your organization’s administrator and installing S/MIME control. Follow Microsoft 365’s steps for setting up to use S/MIME encryption.
- Encrypt all messages or digitally sign all messages by going to the gear menu and clicking S/MIME settings. Choose to either encrypt the contents and attachments of all messages or add a digital signature to all messages sent.
- Encrypt or remove individual messages by selecting more options (three dots) at the top of a message and choosing message options. Select or deselect “Encrypt this message (S/MIME).” If the person you are sending a message to doesn’t have S/MIME enabled, you’ll want to deselect the box or else they won’t be able to read your message.

How to Encrypt Emails on iOS
iOS devices also have S/MIME support built in as a default.
- Go to settings, then click “Mail.”
- Select “Accounts.”
- Click on the email account you want to encrypt messages from.
- Select “Advanced” and change “Encrypt by Default” to yes.
- When you compose a message, a lock icon will appear next to the recipient. Click the lock icon so it’s closed to encrypt the email.
Note: If the lock is blue, the email can be encrypted. If the lock is red, the recipient needs to turn on their S/MIME setting.

How to Encrypt Emails on Yahoo Mail
Yahoo Mail does not offer built-in email encryption for end-to-end security. However, you can still encrypt your emails using third-party tools or secure communication methods.
Use a third-party encryption service:
- Install an email encryption tool like Proton Mail Bridge, Mailvelope or PGP-compatible software.
- Generate a public-private key pair and share your public key with recipients.
- Encrypt your email using the tool before sending it through Yahoo Mail.
Send encrypted attachments:
- Use software like 7-Zip or WinRAR to encrypt email attachments with a password.
- Share the password with the recipient via a secure method (e.g., a phone call or SMS).
Secure your emails by enabling HTTPS — typically enabled by default. While this secures data transmission, it doesn’t encrypt the email content.
Encrypt Email With Third-Party Tools
Email encryption can be done manually or by a secure email service. Here are some email service apps, each with unique offerings such as encrypting emails, attachments and contact lists. They do this in the background so you don’t have to worry about doing it manually.
- Proton Mail: End-to-end encryption with free and paid plans
- CipherMail: Supports S/MIME, OpenPGP and TLS encryption, ideal for Android devices
- Mailvelope: Browser extension for OpenPGP encryption compatible with popular webmail services
- Virtru: End-to-end encryption for Gmail and Outlook
- StartMail: Offers PGP encryption with paid plans
- Skiff Mail: Provides end-to-end encryption on mobile devices
Email Security Best Practices
With or without an email encryption service, it’s always a good idea to implement security best practices when using email. Keep these tips in mind:
- Create strong passwords: Using complex passwords with a mix of uppercase and lowercase letters, numbers and symbols makes it harder for hackers to guess your passwords and access your personal accounts. Try our password generator to make this quick and easy.
- Enable 2FA on email accounts: Two-factor authentication (2FA) serves as an additional layer of security for your email accounts. For example, you might enter a code that’s sent to your phone after inputting your login information.
- Don’t click on links or attachments from unreliable sources: Malware often lurks in email attachments or links. Before clicking on a link or opening an attachment, verify that you know the sender and check for signs of phishing. Never open an attachment from someone you don’t know.
- Scan attachments, even from encrypted emails: Use antivirus software or an online service to scan your email attachments and look for malware before you open them.
- Avoid logging in to check emails on public Wi-Fi: Cybercriminals can monitor your online activities and steal your personal information on public Wi-Fi , so avoid logging in to accounts like email or your bank accounts if possible.
Protect yourself and your business from new email threats by taking preventative measures. Implementing an advanced cybersecurity solution like antivirus will help you find the best prevention techniques and instruct you on efficient ways to apply them to keep you safe from hackers.
FAQ
Have more questions about email encryption and security? Here are answers to some frequently asked questions to help you understand how you can protect your emails and ensure your sensitive information stays secure.
How Can You Password-Protect an Email?
To password-protect an email, use a third-party encryption tool or an email service with built-in password-protection features. For example, services like Proton Mail allow you to set a password for the recipient to decrypt and view the message. You can also create a password-protected PDF or document to attach to your email as an alternative.
What Does Encrypting an Email Do?
Encrypting an email transforms its content into unreadable code, ensuring only the intended recipient can decipher it using a private key. This prevents unauthorized access, even if the message is intercepted during transit.
Is It Safe to Encrypt Email?
Yes, it is safe to encrypt email. Emails often contain sensitive information, and without encryption, they are vulnerable to attack at every stage of their journey from sender to recipient. End-to-end encryption ensures that only the users communicating with each other can access the encryption keys — not even the system provider. For maximum security, use email encryption tools that comply with robust security standards, such as PGP or S/MIME.





2 comments
This article is misleading for AOL users. AOL does not accept any third party encryption for kits EMAIL account holders
This should be updated .at this site
I have been searching about Yahoo Mail then finally, when I read this article I get to know the correct information about it and I found this information is relevant. You have an ample amount of knowledge and that describes it very clearly and I thank you for giving me this type of knowledge and it helps me a lot.Still useful post. Solved my Problem