Domain name system (DNS) spoofing is a type of cyberattack that uses tampered DNS server data to redirect users to fake websites. These malicious sites often look legitimate but are designed to install malware onto users’ devices, steal sensitive data or redirect traffic.
Imagine logging into what you thought was a trusted account on one of your favorite sites just to have your data stolen by a hacker. This is the danger of domain name system (DNS) spoofing and poisoning.
DNS spoofing can lead to severe consequences such as identity theft, fraud, malware distribution and data breaches — making it crucial for individuals and organizations to understand and address this threat. By being aware of DNS spoofing tactics, you can identify signs of suspicious activity and take proactive steps to safeguard your data privacy.
Read on to learn the different types of DNS spoofing attacks, how to identify them and tips to prevent DNS spoofing and DNS poisoning.
What Is DNS Spoofing?
DNS spoofing is a cyberattack where a hacker tricks a computer or network into believing it’s communicating with a legitimate website or server. In reality, the computer is interacting with a fake website or server set up by the attacker. This deception leads users to malicious websites — exposing them to identity theft, financial fraud, malware and other online threats.
For example, imagine you’re trying to access your Gmail account. However, a cyberattacker has manipulated the DNS records so when you type “www.gmail.com” into your web browser, you’re directed to a fake website that looks like Gmail, but the attacker has full control of it. When the fake website takes you to the login page, you enter your email and password. The attacker now has your credentials and can use them to access your email.
DNS translates easy-to-remember website names into the complex numerical addresses required for computers to communicate with each other. However, cybercriminals can employ deceptive tactics to manipulate the DNS and lead unsuspecting users astray. Two such tactics are DNS spoofing and DNS poisoning.
DNS Poisoning vs. DNS Spoofing
DNS poisoning is a method cyberattackers employ to compromise and replace legitimate DNS data with malicious information, typically by injecting false DNS records into DNS caches. This deceptive tactic aims to redirect users to fraudulent websites or servers, leading to potential security breaches, data theft or other cyberthreats.
DNS spoofing — a result of DNS poisoning — occurs when users are redirected to malicious websites or servers via the manipulated DNS cache. In DNS spoofing attacks, hackers exploit the poisoned DNS cache to intercept users’ requests for legitimate websites and redirect them to fraudulent destinations under the attackers’ control. This DNS record manipulation can lead users to unknowingly disclose sensitive information, fall victim to phishing scams or inadvertently download malware.
Despite their differences, both tactics pose significant cybersecurity risks, necessitating vigilance and robust security measures to mitigate cybersecurity breaches effectively.
How Does DNS Spoofing Work?
There are a few methods attackers can use to execute DNS spoofing attacks, but they all share the same goal: to trick users and their servers into thinking a fraudulent website is legitimate. To do this, attackers typically follow these three steps:

Step 1: Accessing the DNS server
Before a hacker can perform this attack, they need to gain access to the DNS server or DNS resolver cache. This process involves identifying a DNS server’s software versioning and MAC address, scanning for vulnerabilities and determining whether it uses DNSSEC (domain name system security extensions) or DNS encryption. Unfortunately, most DNS queries and responses are unprotected, making it easy for attackers to gain access and redirect traffic to a server they control.
Step 2: Rerouting Connections
Once the attacker has access to a DNS server or resolver, they can replace stored IP addresses with fake ones. Because these systems can’t differentiate between a legitimate IP address and a malicious one, attackers can trick them into storing a spoofed entry that leads to a malicious website. Once this process is complete, the spoofed entry remains in the system and directs anyone connected to the server to the malicious site instead of the legitimate one.
Step 3: Accessing Sensitive Data
Once a user arrives at a malicious website, it may prompt them to enter their login information like they normally would. Because the fake site looks exactly like the legitimate one, the victim has no idea that they are handling sensitive information over to the attacker. Attackers can also use DNS spoofing to install malware on a user’s device or redirect traffic to phishing websites. This is especially common for online shopping and banking websites.
Cybersecurity Consequences of DNS Spoofing
DNS spoofing can pose multiple risks to users. Some of the most common risks include:
 Data Theft
Data Theft
Attackers frequently use DNS spoofing to access sensitive user data like banking, credit card and personal login information. Phishing websites can be difficult to detect, so users may not notice their data was compromised until it’s too late.
Censorship
Censorship is when someone controls or blocks access to certain information or websites. In the digital world, attackers can use DNS spoofing to censor web results by tricking your computer into thinking a website doesn’t exist. Some governments purposely manipulate DNS caches like internet address books to stop people from accessing specific websites or online resources. For instance, China uses DNS censorship as part of its Great Firewall, which redirects users away from certain websites.
Malware Infection
Fake websites are often full of malicious links and downloads that can infect your device with malware. If the spoofed site is an internet security provider, it can indirectly expose you to viruses by preventing legitimate security updates. This risk is highest for users who don’t use antivirus software.
Types of DNS Spoofing Attack Methods
There are a few different ways attackers can execute a DNS spoofing attack. Some of the most common examples include:
DNS Server Compromise
A DNS server compromise is one of the most common methods for DNS spoofing. In this scenario, an attacker gains access to the DNS server and injects a fake DNS entry. Once the fake IP address is in the system, it directs traffic away from the legitimate site to the malicious one.
A famous example of this type of attack happened in 2018, when hackers compromised Amazon’s Route 53 DNS server and public Google DNS servers. After gaining access, they rerouted roughly 1,300 IP addresses to malicious phishing websites designed to steal user information.
One of their biggest targets was the cryptocurrency website MyEtherWallet. Attackers sent users attempting to access their digital wallets to a phishing site and managed to steal around $152,000 during the two-hour attack window.
Man-in-the-Middle (MITM) Attack
A man-in-the-middle (MIM) attack is a type of cyberattack that hackers use to intercept digital traffic or data transfers and hijack important information. To execute this attack, an attacker intercepts a user’s DNS request before it reaches a legitimate server and reroutes to a fake IP address. This not only sends a spoofed result back to the user and infects their device but can also poison the DNS server that received the initial request.
Exploiting Time-to-Live (TTL)
Time-to-live (TTL) is a setting in DNS records that determines how long the record can be stored (cached) by DNS servers before it needs to be refreshed. By extending the TTL, attackers ensure that their malicious DNS mappings remain in the cache of DNS servers and users’ devices for a longer period than intended.
This tactic prolongs the window of opportunity for attackers to redirect users to malicious websites or servers, amplifying the impact of DNS spoofing incidents.
How to Prevent DNS Spoofing and Cache Poisoning
DNS spoofing and cache poisoning can be difficult to detect since they can affect both user devices and DNS servers. However, individuals and businesses can take steps to reduce their risk of falling victim to an attack.
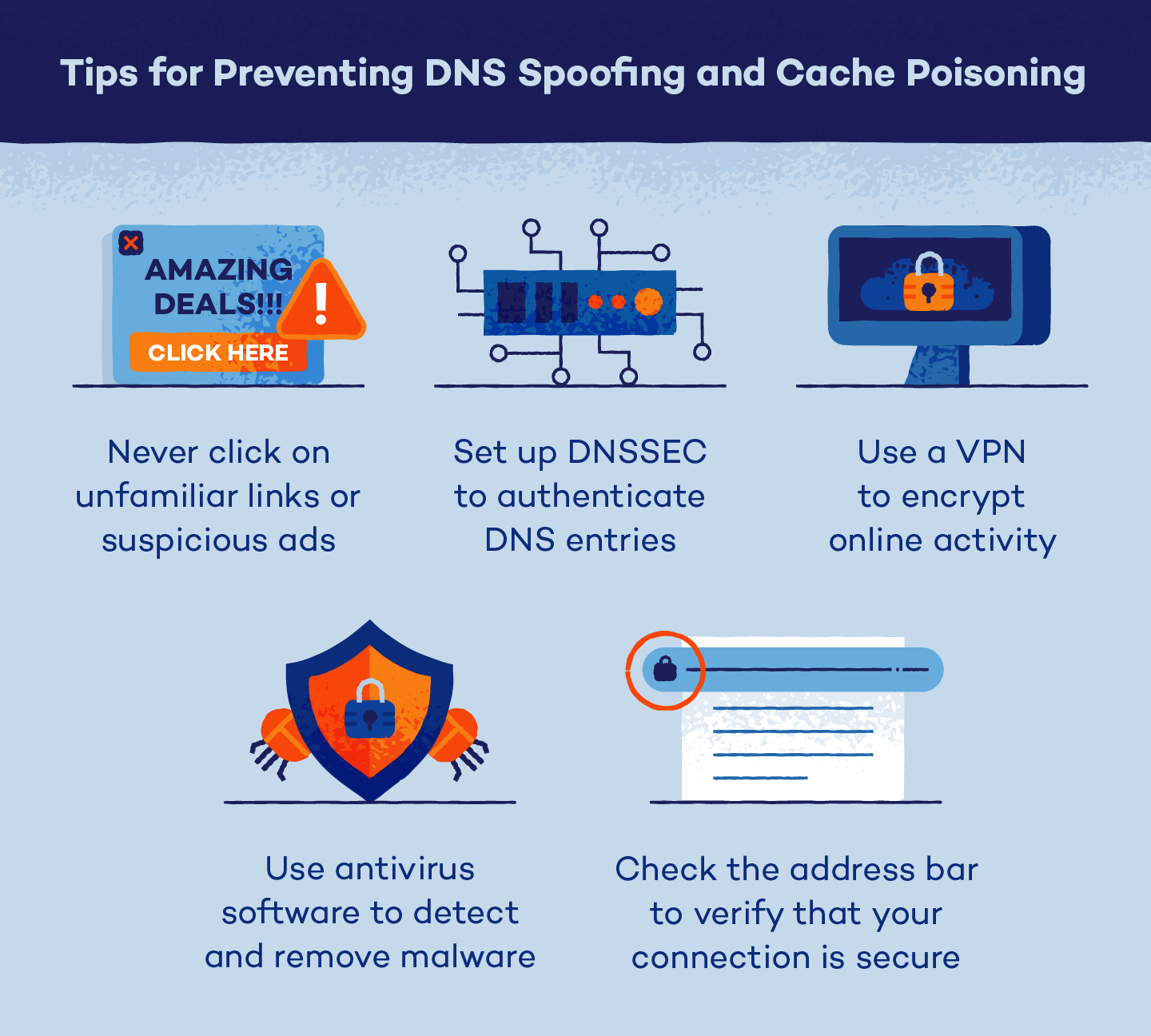 Never Click on Unfamiliar Links
Never Click on Unfamiliar Links
Malicious websites often display fake advertisements or notifications that prompt you to click on a link. By clicking on unfamiliar links, you could expose your device to dangerous viruses and other malware. If you notice an unfamiliar link or advertisement on a website you normally use, it’s best to avoid it.
Set Up DNSSEC
Domain owners and internet providers can set up DNS security extensions (DNSSEC) to authenticate DNS entries. DNSSEC works by assigning a digital signature to DNS data and analyzing a root domain’s certificates to verify that each response is authentic. This ensures that each DNS response comes from a legitimate website. Unfortunately, DNSSEC is not widely used, so DNS data for most domains remains unencrypted.
Scan for and Remove Malware
Because attackers often use DNS spoofing to install viruses, worms and other types of malware, it’s important to scan your devices for these threats regularly. You can do this by installing antivirus software that identifies and helps remove threats. If you own a website or DNS server, you can also install DNS spoofing detection tools. These are designed to scan all outgoing data to ensure it is legitimate.
Use a VPN
A virtual private network (VPN) is an added security measure that prevents attackers from tracking your online activity. Instead of connecting your devices to your internet provider’s local server, a VPN connects to private DNS servers around the world that use end-to-end encrypted requests. This prevents attackers from intercepting traffic and connects you to DNS servers that are better protected from DNS spoofing.
Verify That Your Connection Is Secure
Malicious websites are often identical to legitimate ones at first glance, but there are a few ways to verify that you’re connected to a secure site. If you’re using Google Chrome, look for a small, gray padlock symbol in the address bar to the left of the URL. This symbol shows that Google trusts the domain host’s security certificate and indicates that the website is not a duplicate.
In some cases, your browser will alert you if you try to access an unsecured site. If you see a message warning that your connection isn’t secure, you shouldn’t ignore it. It could mean that the site you’re trying to access is a spoofed site without a legitimate SSL (Secure Sockets Layer) certificate.
DNS spoofing is one of the most difficult types of cyberattacks to detect, but there are plenty of strategies you can use to protect yourself and your information. Consider installing reliable antivirus software or a VPN to help secure your online activity and fend off future attacks.





