Clickjacking can be described as a dangerous form of online hide-and-seek.
Hackers hide malicious links behind recognizable or appealing webpages and wait for users to unintentionally seek them out. Unlike the childhood version of hide-and-seek, the seeker in these UI redress attacks always loses the game.
To protect yourself and your devices from cybercriminals, it’s important to know when and where clickjacking is at play. Our in-depth guide can help you better understand the dangers of hidden webpage links.
What Is Clickjacking?
Clickjacking occurs when hackers and cybercriminals create transparent layers over buttons or links that reroute users to unintended sites without their knowledge. These attacks take clicks away from legitimate pages and cause users to visit unauthorized websites or landing pages.
In addition to rerouting traffic, clickjacking could lead to:
- The theft of login credentials, including usernames and passwords
- Unauthorized access to cameras and microphones
- The spread of malware
- An increase in online scam success
- Unsolicited purchases
- Unapproved payments to ad and e-commerce sites

Types of Clickjacking
The goal of clickjacking attacks are fairly standard: trick a user into selecting a malicious button or link. However, there are different clickjacking variations cybercriminals use to encourage this outcome:
- Likejacking: “Like” buttons on social media pages are hijacked and cause users to interact with unintended or dangerous pages and profiles.
- Cursorjacking: Cybercriminals mask the location of a user’s cursor so it appears to be on a different part of a page than it actually is.
- Cookiejacking: Hackers steal a user’s cookies, which contain sensitive data that can be used to imitate the user.
- Filejacking: Filejackers place frames over “browse files” buttons, which causes victims to unintentionally give cybercriminals access to their online files.
- Mousejacking: Criminals remotely control the functions of a device and are able to click items, type commands and create code.
Clickjacking Attacks
In a clickjacking attack, users think they are making one action but invisible frames cause them to make a different unexpected action. These attacks can range from incredibly dangerous to simply inconvenient, and they can be the catalyst for larger, more dangerous attacks.
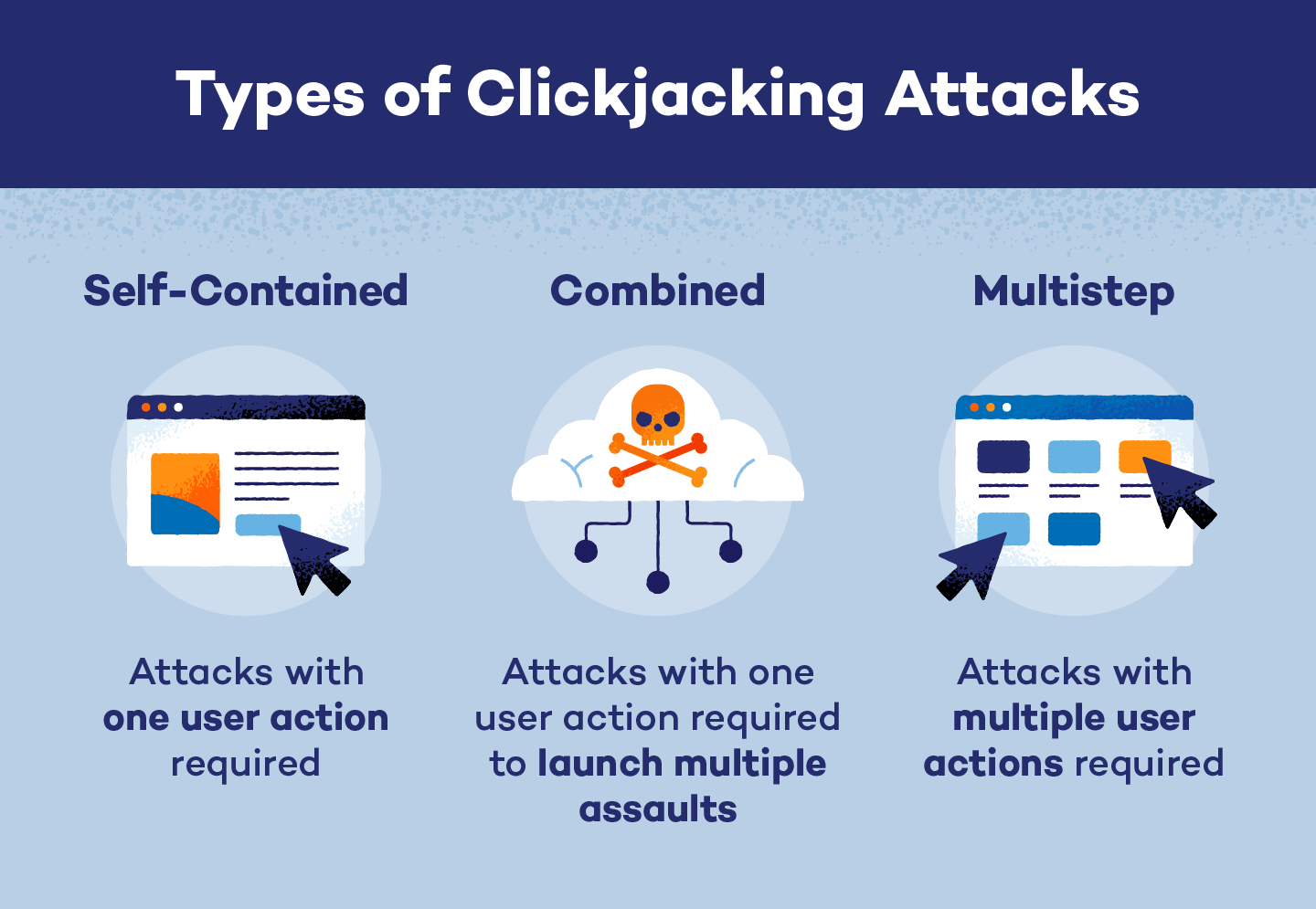
Self-Contained Attacks
Most clickjacking attacks are considered self-contained attacks because they rely on one action. In these cases, a user will click on an invisible webpage frame and take an unknown or unauthorized action.
Multistep Attacks
Similar to self-contained attacks, multistep clickjacking attacks use client-side actions to initiate strikes. These attacks are precise and require users to click on multiple invisible frames to work successfully. For example, a hacker who wants a user to make an unauthorized purchase must set up additional frames that cause users to add items to a shopping cart before their final click.
Combined Attacks
While many clickjacking attacks are self-contained, they can also be used to execute combined attacks. In these cases, hackers will successfully trick users into falling for a clickjacking attack, which can also execute larger malicious strikes. Clickjacking and DOM XSS attacks — attacks that target client-side code and cause webpages to act in a malicious manner — are common combination attacks that modify code and run unauthorized client-side actions.
Clickjacking Example
Clickjacking attacks have been successful in larger corporations like Facebook, Twitter and PayPal. However, these types of online attacks also target individual users.
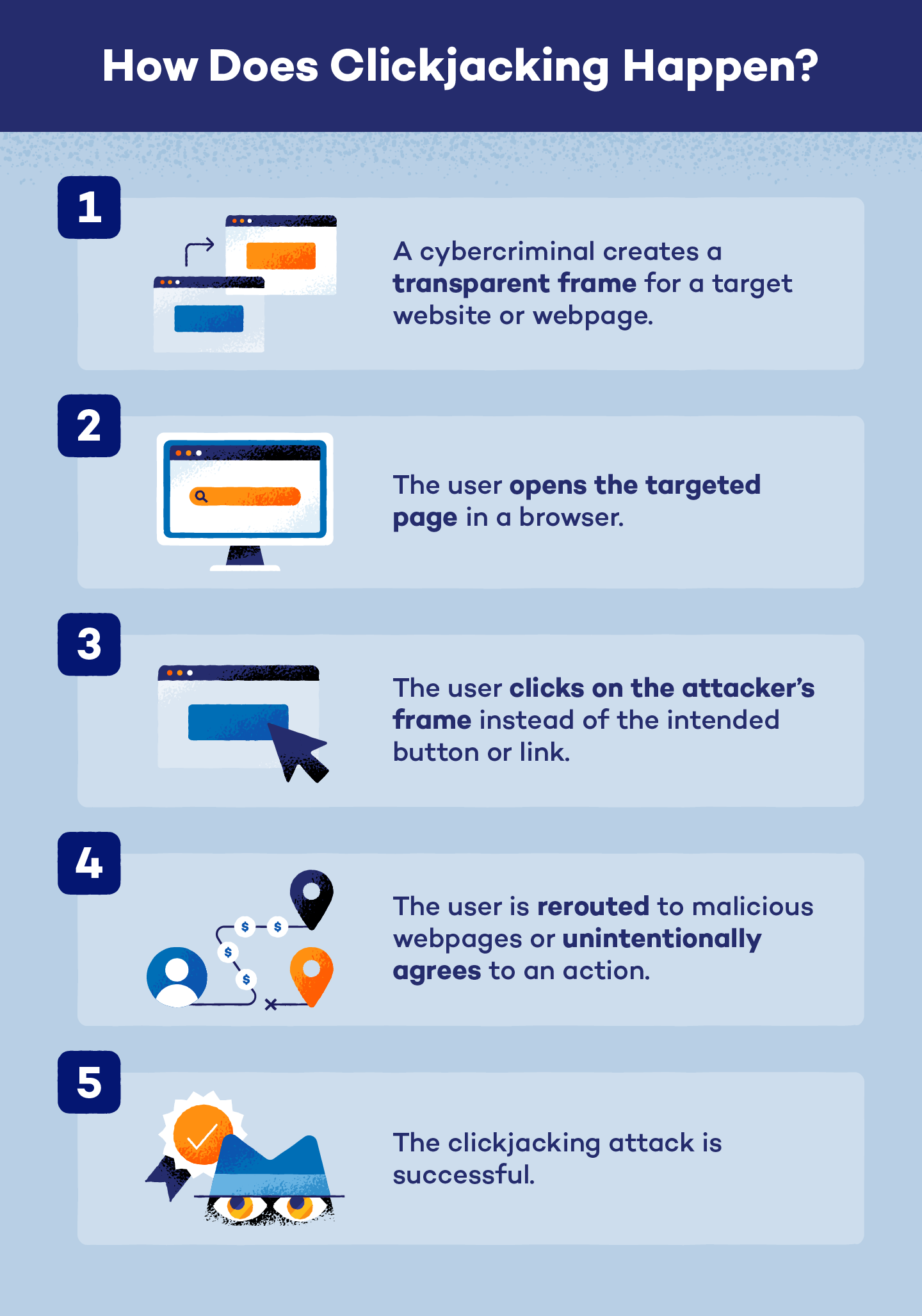
For example, a cybercriminal may create a fake landing page or hijack the iframes of a legitimate website. In both cases, a clickjacking attack can occur like this:
- Users will open and load a targeted website or webpage.
- Enticing buttons like “Play Now” or “Win A Free Trip” will populate.
- Users will attempt to click a button.
- Users will click the transparent or hijacked frame instead.
- Users will follow the bad actor’s button instead, potentially leading to the transfer of funds to the criminal, account deletion or any other type of malicious action.
In many cases, these attacks can’t be traced back to the cybercriminal because the user unknowingly agreed to the action.
Clickjacking Prevention
Clickjacking can occur on any website that can be framed, so clickjacking prevention measures usually attempt to restrict the framing capabilities of a site. Prevention techniques can be used both client-side and server-side.
Client-Side Prevention
Prevention measures that can be enacted by a user on their own devices or webpages without the help or knowledge of a network server are known as client-side prevention techniques. These techniques can usually be bypassed, so they are best used with other server-side methods.
Clickjacking Frame Busting Script
Prevention scripts are placed and used within a web browser. This clickjacking defense — also known as frame breaking scripts — is platform-specific, and it can also be easily neutralized by attackers with HTML and JavaScript knowledge. However, successful scripts can:
- Make invisible webpage frames viewable
- Stop invisible frames from being clickable
- Identify and protect against clickjacking attempts
- Ensure the intended window is not covered by an invisible frame
Anti-Clickjacking Extensions
Browser extensions can help prevent clickjacking, but they may disable JavaScript and negatively impact a webpage’s user experience. When installed, these JavaScript blockers may prevent popular sites like YouTube and Facebook from opening.
Malicious browser extensions also exist and could cause additional issues for some users. If you choose to disable JavaScript with an anti-clickjacking extension, research your options or choose trusted sources like ScriptSafe or NoScript.
Antivirus Software
Dependable antivirus software works around the clock to keep devices protected from a variety of malicious attacks. In the case of clickjacking, antivirus software can warn users before they enter potentially dangerous websites, and it can help keep data and information secure in the event of a successful attack.
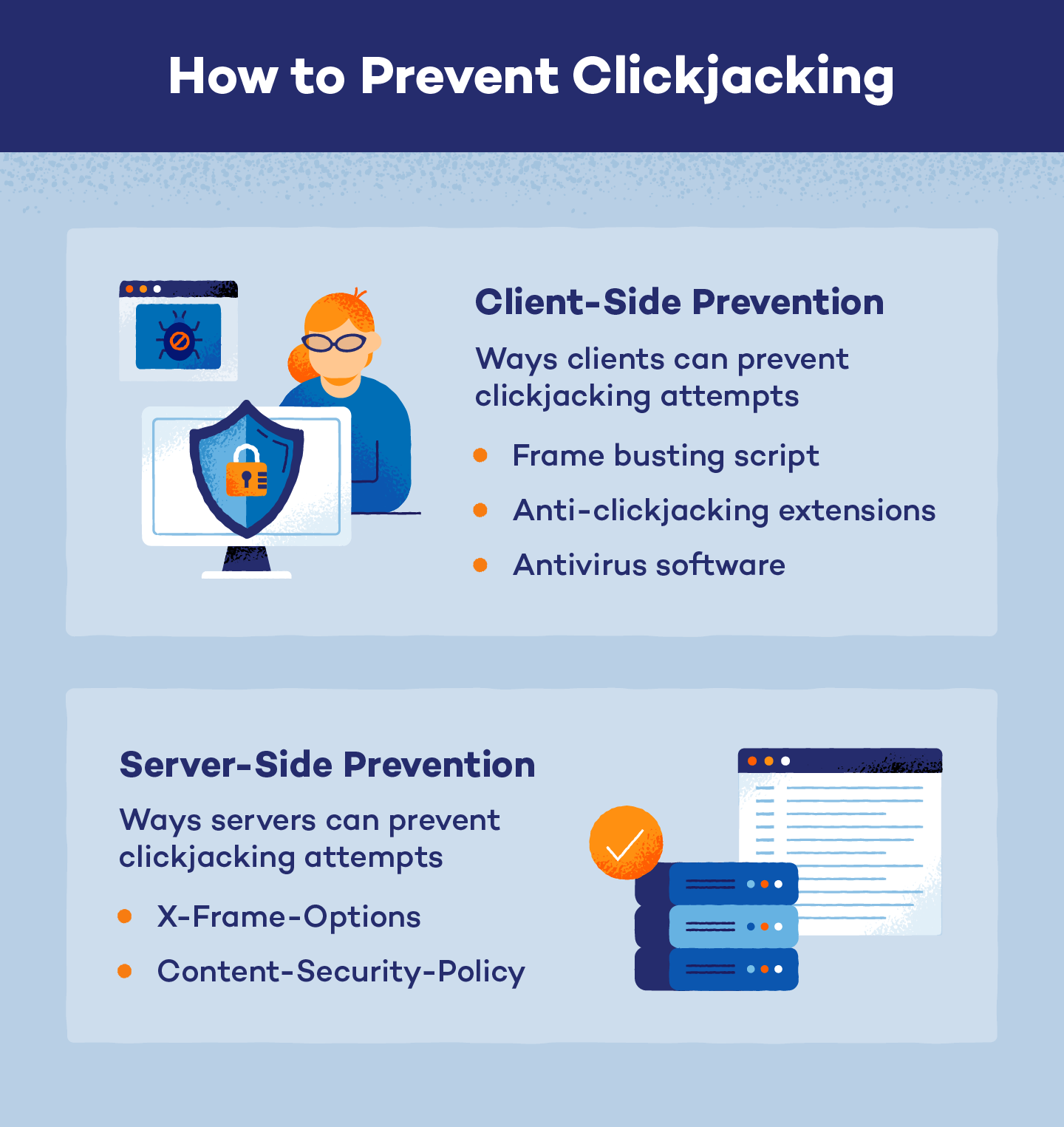
Server-Side Prevention
Defense mechanisms that need to be created and enacted by a server are known as server-side prevention techniques. These cannot be set up or used by a client and are only successful when implemented within the server.
X-Frame-Options
Originally created for Internet Explorer, X-Frame-Options was quickly adapted as a clickjacking prevention method within other browsers. This technique controls a webpage’s iframes and other objects by enacting directives like:
- X-Frame-Options: deny prevents use or change of frames
- X-Frame-Options: sameorigin restricts site framing to the original page
- X-Frame-Options: allow-from https://any-site.com allows framing changes from specific sites
X-Frame-Options: allow-from is only active on some browsers, but the other directives can be combined with a content security policy to create a multifaceted clickjacking prevention method.
Content-Security-Policy
Webpage attacks are usually prevented by the Content-Security-Policy (CSP), which also helps detect when and where these attacks might occur. This prevention method provides webpages with a specific list of allowed and unallowed sources, changes and users.
Similar to X-Frame-Options, CSP has specific protection directives:
- Content-Security-Policy: frame-ancestors ‘none’ stops malicious actors from changing frames
- Content-Security-Policy: frame-ancestors ‘self’ keeps site framing to the original page
- Content-Security-Policy: frame-ancestors any-site.com only allows specific sites to enact framing changes
When created properly and implemented within a multi-layer strategy, server-side prevention methods are incredibly successful at protecting against clickjacking attempts.
Clickjacking is a threat to all types of online browsers. Keeping devices clean of malware and other malicious software can help keep a user’s browser free of clickjacking vulnerabilities. Panda Security can even help tailor cybersecurity services to a user’s specific protection needs.
Sources: Intellipaat | OWASP | Sepio





