Posts by author
Panda Security
Why Adaptive Defense 360?
A few days ago we published an interview on why Adaptive Defense was the solution against ransomware like Cryptolocker. Now, however, I’d like to go…
If you like videogames, check out these safety steps!
Do you know how to play safely? Follow these tips and use common sense!
How to act after a cyber-attack
We hear it every day, experts are always talking about it: preventing cyber-attacks is very complicated, almost impossible, so what organizations should do is work…
Apple Watch: nothing prevents thieves from resetting the password and using a stolen one (even for shopping)
It is one of the longest awaited gadgets in recent times and is set to become one of the technological gadgets of the year, but…
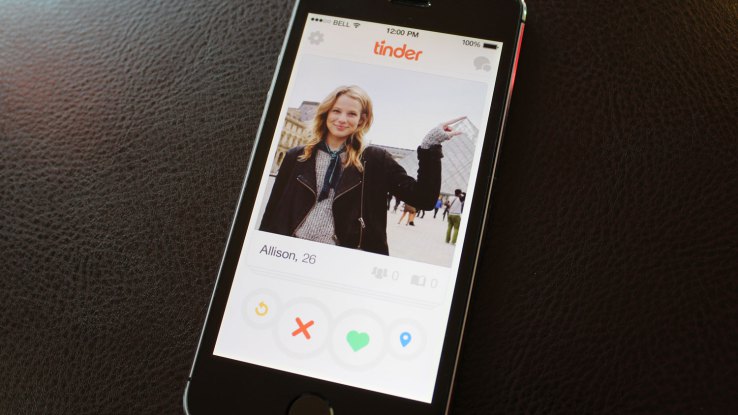
Tinder, the app where you can have your heart stolen, but also your information and your pictures
To find a ‘match’ in Tinder we have to share personal information with other users. If you don’t have at least one picture and you…
CryptoLocker: What Is and How to Avoid it
CryptoLocker is a family of ransomware whose business model (yes, malware is a business to some!) is based on extorting money from users. This continues…
8 things your kids shouldn’t do online
It’s not unusual nowadays to hear people say that if you want to know how to operate any technical device, ask a child, and they’re…