Posts by author
Panda Security
No, the FBI is not trying to fine you
New Android malware pretends to be the FBI, tries to extort money from victims. Here is how to avoid being a victim of this malware.
Can your social-media past haunt you?
Your past behaviour on social media may not represent your current or future perspectives. Here is how to delete your past Social Media conduct.
Cyberstalking – Not all hacking is for profit
Hacking is not always about stealing data for money – sometimes people do it to feed their obsessions. Beware of cyberstalkers.
The Perils of Video Calls (And How To Protect Yourself)
Video calls have become more popular since the Covid outbreak. Hackers are causing all kinds of problems for video callers – here’s how to protect yourself.
How to limit work-from-home distractions?
Millions have started working from home since the coronavirus took over. Here are some tips to avoid distractions and be productive.
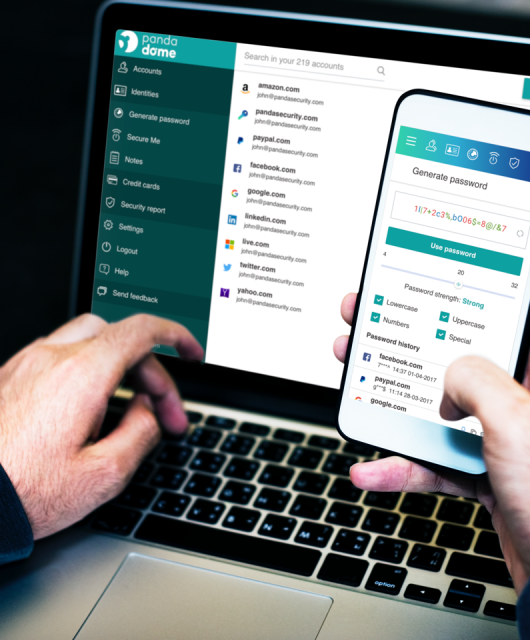
World Password Day : Online passwords as a security risk
World Password Day is an opportunity to recall that the password is very important for online authentication, but that it has also become the weakest link in terms of cybersecurity.
What to expect from the upcoming Apple and Google contact tracing apps
Apple and Google joined forces to develop the technology to trace sick people. It could help stop the Coronavirus spread, but also raises privacy concerns.