Cybercriminals have a litany of ways to make money. One of these methods is the use of social networks. According to Dr. Mike McGuire, a Senior Lecturer in Criminology at the University of Surrey, black hats generate $3.2 billion ($2.87 billion) per year in social media-enabled cybercrime. What’s more, one in five companies has experienced a malware attack through social media.
LinkedIn, a tool for cybercrime
In July, a cybersecurity company discovered a cybercriminal campaign that infected companies via the social network LinkedIn. The attackers posed as researchers from the University of Cambridge in order to gain their victim’s trust. They then used this trust to trick the victims into opening documents infected with malware.
The attackers were part of APT34, a cyber espionage group with links to the Iranian government, which has been active since at least 2014. The group usually attacks organizations in the financial, government, energy, telecoms and chemical sectors in the US and Middle East. This campaign follows the same modus operandi, since its victims work in the energy, gas and oil sectors, as well as government organizations. All of these areas are of particular strategic interest for anyone who wants to get hold of sensitive information, as well as being particularly lucrative.
Spyware
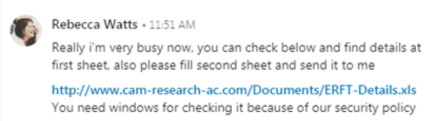
APT34 used three types of malware in this campaign: Tonedeaf, ValueValut and LongWatch. Tonedeaf is a backdoor that communicates with a single command and control (C&C) server. It supports several commands for collecting system information, uploading and downloading files, and executing arbitrary shell commands.
ValueVault is used to steal Windows system credentials, while Longwatch is a keylogger that exports information about keystrokes to a log.txt file in a Windows temp folder. These three pieces of malware were delivered via a weaponized Excel called “ERFT-Details.xls”.
The dangers of social engineering
The tactic of gaining a victim’s trust in order to get them to download infected files has been seen in other campaigns. In this case, the attackers started the conversation by requesting the victim’s CV for a potential job opportunity.
This technique is called social engineering. It consists of making the victim believe that the attacker is someone they can trust. The attacker can use this trust to different ends, not just downloading malware. One cybercriminal tactic that often makes use of social engineering are BEC scams (business email compromise), which consist of tricking an employee into making a fraudulent bank transfer.
The keys to protecting your company
The first line of defense against attacks of this kind is, without a doubt, awareness. To stop an attacker from being able to get into your company with infected files and social engineering tactics, every employee must be aware of this kind of threat. It is also essential that they know what they must do if they are faced with this kind of incident.
Here, training is another key concept. Employees must be taught that any member of an organization can be victim of an attack of this kind, not just the top management, and that they too can become a way in for a cyberattack that could endanger the whole organization.
It is also important that they know how to recognize a suspicious email or message. Is the email address really an actual company’s email address? Does the sender’s name appear on the website of the company they supposedly work for? If they have even the slightest doubt about the origins of an email, they mustn’t respond and, more importantly still, must never download any attachments. In these cases, the IT team should be the first point of contact.
Even if employees are perfectly trained in how to prevent social engineering attacks, it is also vital to have an advanced cybersecurity protection to detect, identify and stop threats. Panda Adaptive Defense monitors an company’s IT systems constantly to ensure that no cyberthreat can endanger our organization.
With this combination of employee awareness and IT professionals who have the best advanced cybersecurity solutions to carry out their work, you can ensure that your company will be protected.





