Companies are increasingly aware of the importance of creating detection and hunting capacities that help to keep their business’s future from being put at risk.
The popularity of Threat Hunting services is a consequence of detecting ever more persistent attacks, which also last longer and longer. On top of this, cybercriminals also have ever more tactics to avoid traditional defense measures, As such, as well as detecting attacks, it is increasingly important to try to get ahead of cyberattacks, so that the detection gap is reduced as much as possible.
However, organizations lack the budget, technology, processes, and above all, the team of experts needed to do this from scratch. This makes it impossible for most companies to build and grow their defenses at the same rate as cybercrime evolves.
In this ecosystem, Threat Hunting stands out as one of the most important trends of the last few years in corporate cybersecurity. But in order to understand why Threat Hunting is such an important concept nowadays, it is vital to understand exactly what it is.
What is Threat hunting? This concept can be defined as “…the process of proactively and iteratively searching through networks to detect and isolate advanced threats that evade existing security solutions.”
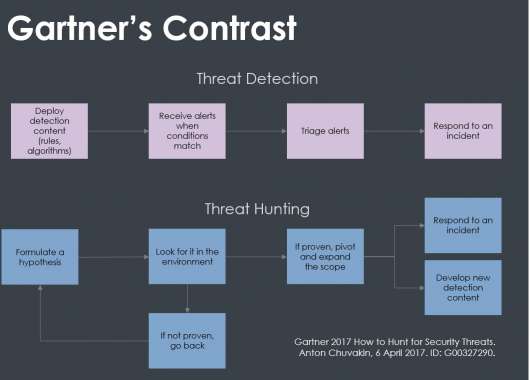
What makes it different? Proactivity is what really sets Threat Hunting apart from traditional threat management measures such as firewalls, intrusion detection systems (IDS), sandboxing, and SIEM systems. All these measures involve an investigation after a potential attack or a security incident have set of the alarm. That is, they are reactive, not proactive measures.
What’s more, proactivity is extremely important in advanced cybersecurity solutions. The change of focus from EPP (Endpoint protection) to EDR (Endpoint detection and response) means that there exists a real time telemetry, something which is vital in order to perform threat hunting.
Discover all the details and the advantages that Threat Hunting can bring to your company in the webinar presented by Diogo Pata, Subsidiaries Presales Manager at Panda Security HQ.
Features of Threat Hunting
The most important feature of Threat Hunting is, as we have discussed, its approach: here we are talking about a proactive approach to threats. This means that it is not a response to incidents, although this concept is connected, since from the results of the investigation and its conclusions it is possible to establish new attack or compromise indicators. Threat hunting measures aim to cover what more traditional tools cannot see.
However, though it may seem to be the case, threat hunting is not a replacement for other strategies, such as threat detection.
How does Threat Hunting work?
Panda Adaptive Defense Threat Hunting discovers new attack patterns using the automatic identification of anomalies in the behavior of each user, process, and machine.
The threat hunters then conduct their investigations, which unravel the principal cause, gain an immediate response, and guide the action plan to successfully reduce the attack surface.
What’s more, each new attack pattern also becomes a threat detection behavior that can be used to stop future hackers before they can cause damage, thus creating a cycle of learning and detection.
Does this put a stop to cybercriminality? In actual fact, no. But it becomes so difficult and expensive that the attack stops being profitable, to the point where the attacker moves on to another goal. Because threat hunting irrevocably makes your business come out on top.






2 comments
Requiero ayuda para instalar el panda softwear en mi nueva computadora mi nùmero de cliente es : 75346566
Buenos días, Vicente:
Por favor, contacta con soporte técnico en las opciones mostradas en el siguiente enlace: https://www.pandasecurity.com/support/#homeusers
Nuestros compañeros podrán ayudarte.
Saludos,
Panda Security.