Halloween is just around the corner. As the day approaches, we have to be aware that “trick or treat” means something a little more sinister when it comes to cybercriminals. They may play some bothersome pranks, or they may in fact try to infect our computers with real, no-joke malware that will undoubtedly ruin our holiday spirits.
This Halloween will be marked by threats and cyberattacks organized by criminal groups that shake the foundations of businesses and infrastructures every day. In 2017, WannaCry showed us how it was possible to indiscriminately attack corporate networks all over the world. We’ve also seen surgical attacks, like Petya/GoldenEye, whose target was much more defined. Then, just in time for the spookiest holiday of the year, we saw the big Bad Rabbit.
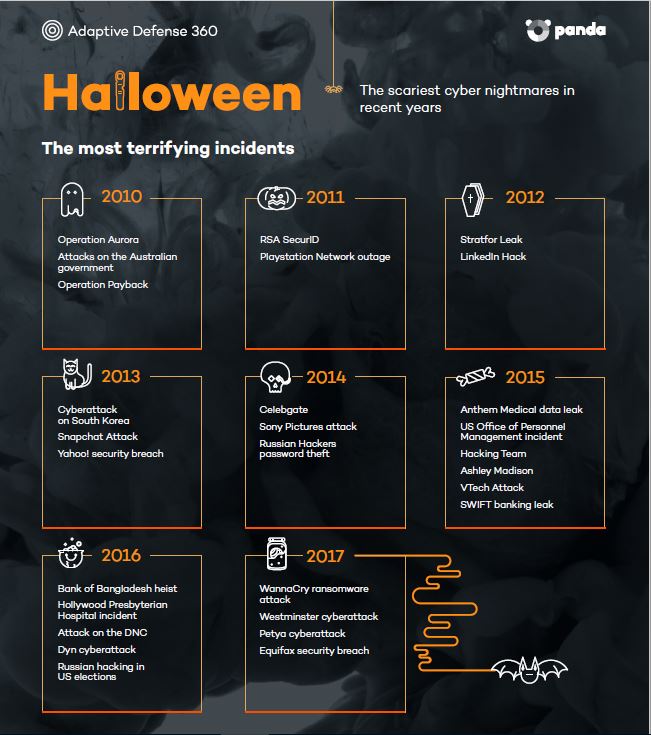
These are just a few recent cases, but can you remember the most terrifying attacks of recent years?
Hackers and Organized Groups, the Latest Cyber Nightmare
There are all different types of hackers with a wide variety of motives. From the cyber arms dealer — a hacker who develops and sells malware and other hacking tools and exploit kits — to other cybercriminals specializing in ransomware; from so-called bankers (hackers specialized in credit or financial card information theft) to contract hackers who belong to a well-established industry and who offer their services in return for remuneration.
They are all behind the most terrifying cyber nightmares, creating diabolical malware and exploiting tenebrous vulnerabilities to haunt your company.

Protect Your Company Year-Round and Enjoy a Bone-Chilling Halloween
Using the right tools is essential to keeping your network safe. A defense method able to protect against malware of all types, even before an attack can begin, is indispensable. Such solutions allow continuous monitoring of network and endpoint activity in real time. Panda Adaptive Defense is a pioneer in this type of technology, and combines state-of-the-art protection with detection and remediation capabilities with the ability to classify 100% of running processes. This approach secures the system against external attacks, and even attacks originating within the network itself.
Make sure Halloween comes only once a year. Manage, control and protect your data against all kinds of advanced threats.
Download bellow other versions:
Portuguese: eBook and Infographic







1 comment