Plenty of cool, life-changing inventions were developed in the 1980s: the CD-ROM, HDTV, 3D video games and — of course — SMB.
With plenty of acronyms to go around, you may have found yourself wondering: What is SMB and why does it matter? And while SMB could be considered one of the most important security inventions of the ‘80s, it’s lesser known than disposable contact lenses — which were invented in 1987, three years after SMB.
While premium security features keep your personal and professional information protected, SMB protocol helps protect users both inside and outside their network’s servers. Dive into our guide to learn just how important SMB is to authentication, security and file sharing.
What Is SMB Protocol?
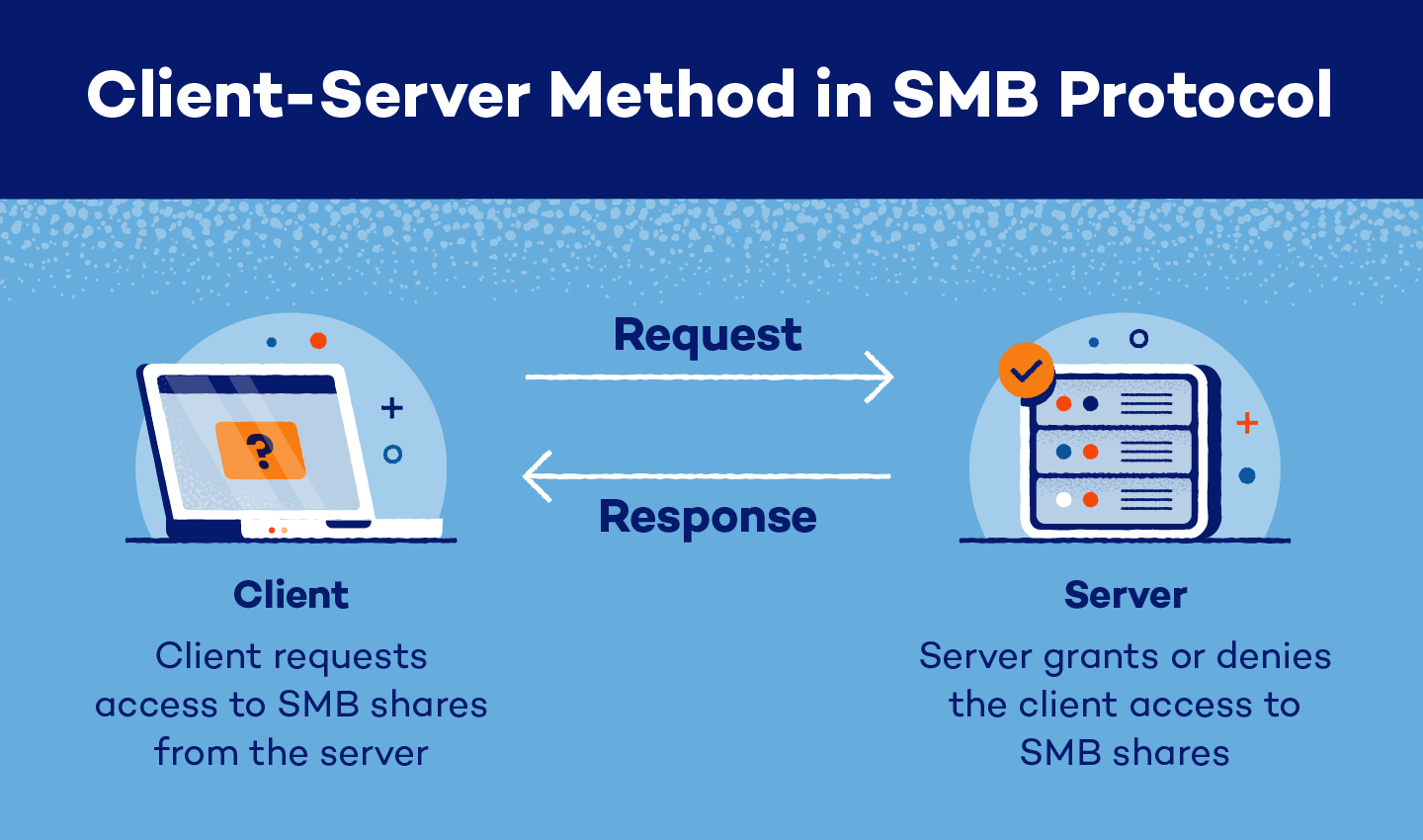
SMB protocol is an internal sharing protocol for resources. This protocol uses a client-server model where users with individual devices can connect to a server to access internal documents, files and more.
SMB is also an application layer protocol that uses an intercommunication system to not only share files but transfer them between network servers and users. Plus, this request-response protocol transfers multiple messages between the user and the server.
SMB Functions
While the main function of the SMB protocol is to provide clients with access to SMB shares, it has various other uses, including:
- Opportunistic locking
- Intercommunication within servers
- Sharing access to files, folders, printers and resources
- Editing and browsing access across a network
- Symbolic link support
- File locking
- Change management for records and directories
- Transparent failover, which allows for easy software and hardware maintenance
- Cluster sharing using SMB scale-out
As continued improvements are made to SMB variations, its functions also improve. Updated variations are often more secure and functional than older versions of the protocol.
Is SMB Safe?
SMB is safe if it is up to date and implemented correctly. As with any security system, SMBs could become vulnerable to new attacks and threats as they arise. Being aware of a protocol’s variation and functionality can help keep you protected if it becomes unsafe.
SMB is safest when users:
- Don’t use SMB 1.0, as it lacks encryption protocols
- Use SMB 3.0 or later to keep files and users secure
- Only allow other trusted and authorized users to access SMB shares
How Does SMB Protocol Work?
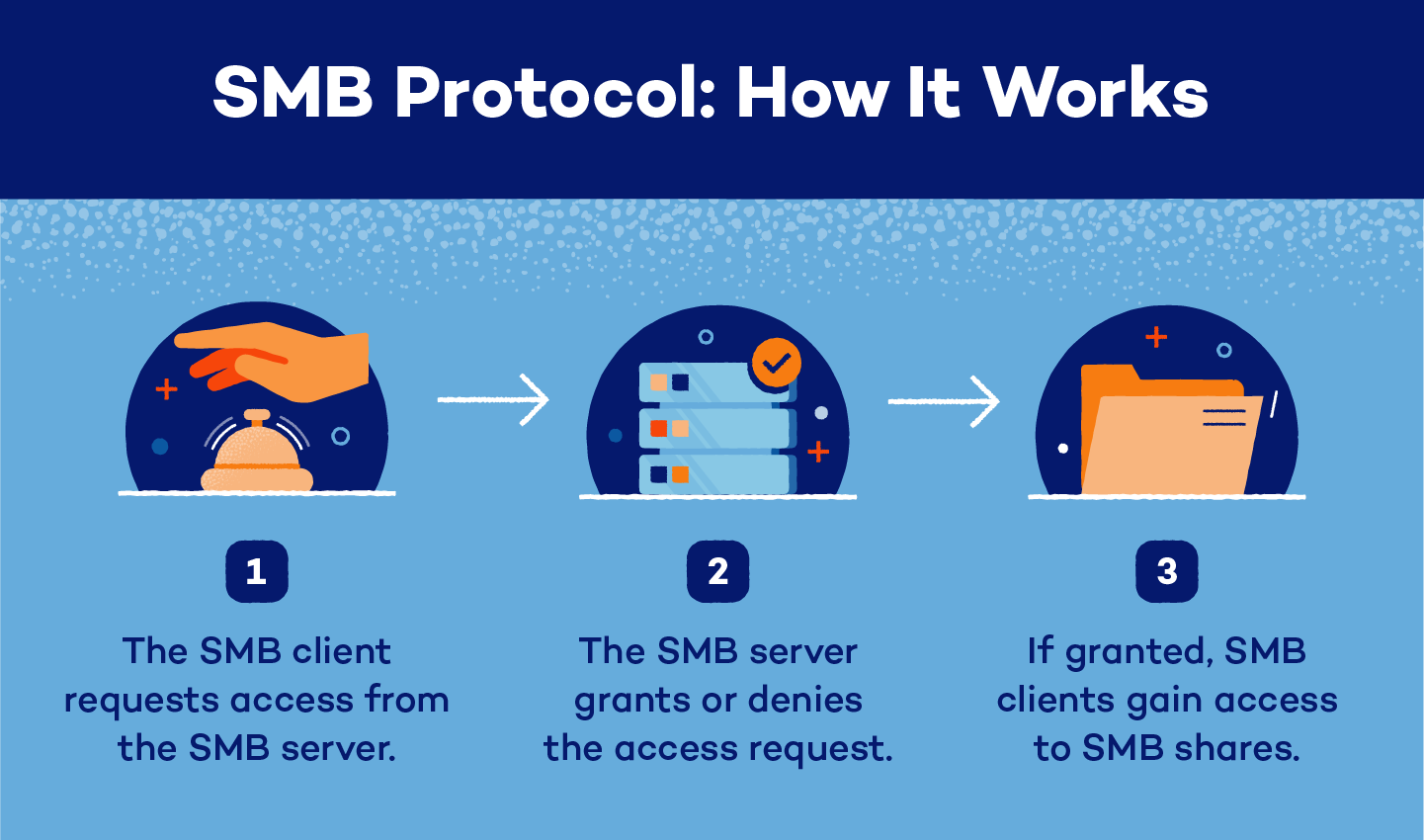
SMB protocol works by sending and receiving messages from a user to another device or file. There are four main actors that work together in SMB protocol:
- SMB client: main device that accesses files and folders on an SMB server
- SMB port: the system on a server or other device used by SMB servers to communicate; modern server variations use port 445, and older variations use port 139
- SMB server: individual or multiple network servers that store SMB resources and grant or deny client access
- SMB share: any resource housed on an SMB server; can also be referred to as SMB file shares
A user, or SMB client, must use an SMB port to request access from a server. The server will then accept or deny their request. If the request is accepted, the client will have access to SMB shares.
Once a client accesses an SMB share, they can edit, print, collaborate, delete and share files across a network without downloading them to individual devices.
SMB Protocol Variations
Since its initial debut in 1984, there have been many SMB protocol variations created to enhance security, encryption and other features:
- SMB 1.0: Originally created in 1984, SMB 1.0 introduced opportunistic locking (OpLock) to help network traffic decrease.
- CIFS: Introduced in 1996, Common Internet File System (CIFS) debuted in Windows 95 and helped support larger files.
- SMB 2.0: SMB 2.0 was introduced in 2006 and helped improve performance, increase strength and reinforce wide area network (WAN) speed.
- SMB 2.1: Launched in 2010 after SMB 2.0, SMB 2.1 included updates to OpLock, transmission unit support, energy efficiency and file access.
- SMB 3.0: Debuting on Windows 8 in 2012, SMB 3.0 improved stability, security and management, and introduced SMB encryption and more.
- SMB 3.02: In 2014, SMB 3.02 introduced system updates and support options.
- SMB 3.1.1: Delivered with Windows 10 in 2015, SMB 3.1.1 added advanced encryption, authentication, cluster dialect fencing and more.
SMB Variations
| Year | Features | |
|---|---|---|
| SMB 1.0 | 1984 | - OpLock - DOS file sharing - Caching |
| CIFS | 1996 | - File support - TCP/IP transport - Symbolic and hard links |
| SMB 2.0 | 2006 | - Reduced chattiness - Increased growth opportunities - WAN support |
| SMB 2.1 | 2010 | - OpLock leasing model - Maximum transmission unit support - Hibernation |
| SMB 3.0 | 2012 | - SMB multichannel - SMB direct - Remote Volume Shadow Copy Service support |
| SMB 3.02 | 2014 | - Flexible CIFS/SMB 1.0 support - Binary removal |
| SMB 3.1.1 | 2015 | - Cluster dialect fencing - Advanced encryption - Pre-authentication integrity |
SMB Authentication
Similar to zero trust security, SMB uses an authentication protocol designed to protect shares. At the user level, clients are required to enter a username and password when requesting access to an SMB server, which can then be accepted or denied by system administrators.
Once authenticated, users can access servers and move across networks, but they need a file- or folder-specific password to access shares — known as a share-level authentication check. This multilevel authentication protocol helps protect both the users and shares across a server.
CIFS vs. SMB
Since its introduction in 1996, CIFS has become an almost interchangeable acronym for SMB. In their earliest forms, CIFS and SMB were similar in various ways, and CIFS was actually designed as a form of SMB 1.0.
However, CIFS differs slightly from SMB. In fact, CIFS is often referred to as an SMB dialect, which is simply another version of the protocol. With the many different variations of SMB, CIFS does not cover the full realm of the protocol’s abilities, and SMB is simpler to use.
| CIFS | SMB | |
|---|---|---|
| Developer | Microsoft | IBM |
| Protocol | TCP/IP protocol | Application interface network protocol |
| Use | Large corporations or projects | All organizations and projects |
| Authentication | No | Yes |
| Security | Not secure | End-to-end encryption |
| Commands | 100+ | 19 |
| Behavior | Glitchy | Continuously improving |
| Supported by | Windows | Windows, Unix, Samba and other visuality systems |
Samba vs. SMB
Samba was designed in 1991 specifically to allow Windows and non-Windows programs — like Linux and Unix — to interact together. Samba is based on SMB, but there are a few differences:
- Flexibility: Samba operates across systems like Linus and Unix, while SMB supports Microsoft, iOS, Java, ThreadX and more.
- Licensing: Samba’s licensing can be problematic for other servers and systems.
- Support: While SMB offers users direct support, Samba is required to use a third-party system.
As a visuality system, SMB is easier to use, service and adapt across a variety of servers, networks and operating systems.
Dangers of Using the SMB Protocol
Even with end-to-end encryption, SMB protocols are a desirable target for hackers. To gain access to the networks and servers protected by SMB, cybercriminals may attempt to break the protocol by using:
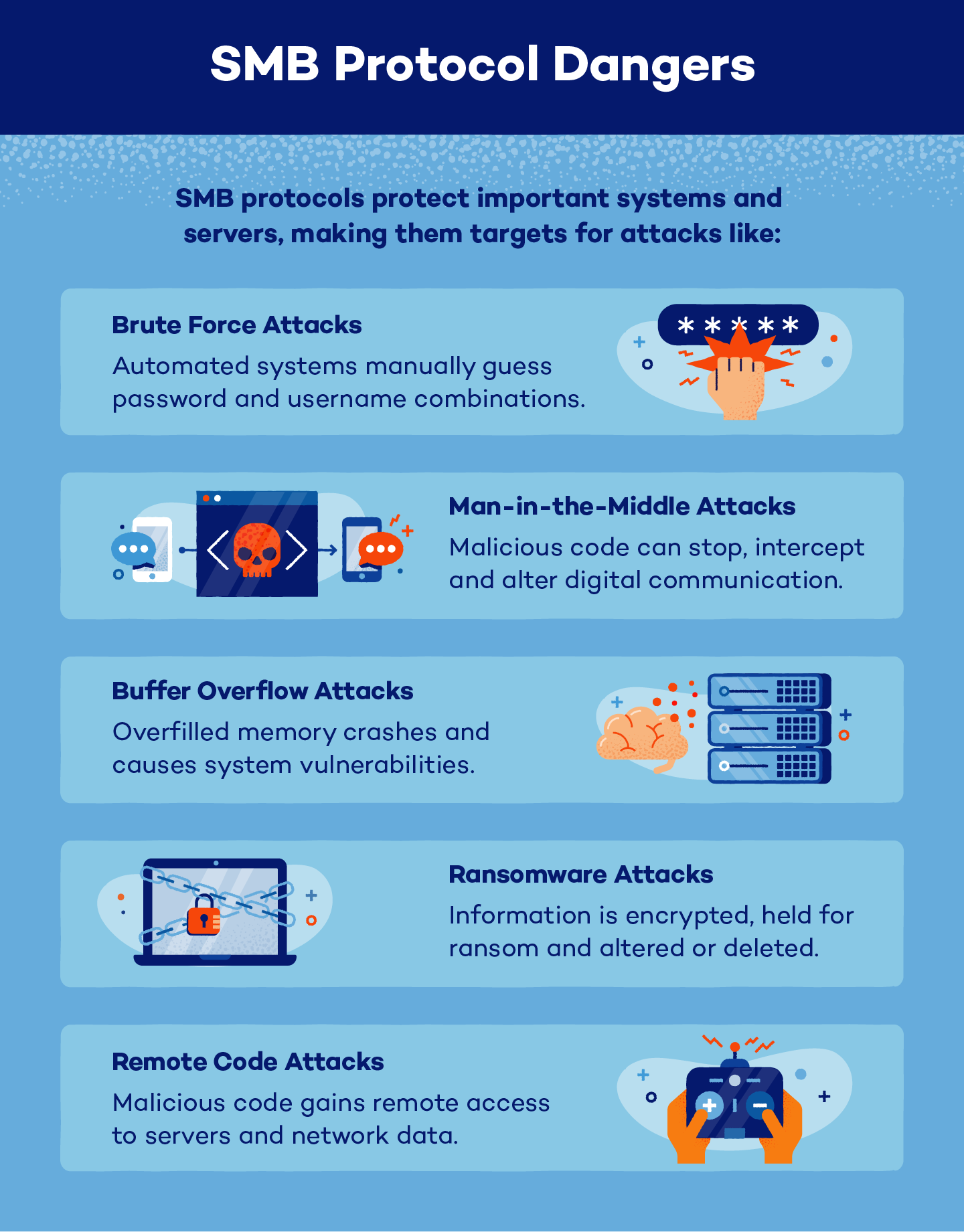
- Brute force attacks: As the most common SMB attack, hackers will use automated systems to continuously guess password and username combinations.
- Man-in-the-middle attacks: Hackers may insert malicious code into a system where they can stop, intercept and alter communication between servers and systems.
- Buffer overflow attacks: Bad actors can overfill a system’s memory, which crashes the system and causes network vulnerabilities.
- Ransomware attacks: If they gain access to a system, hackers can encrypt data, hold it for ransom and delete or alter the information permanently.
- Remote code attacks: Similar to man-in-the-middle attacks, remote code attacks use inserted code to gain access to a network’s system where bad actors can steal, alter, delete or intercept data.
SMB Protection
While SMB is protected by internal mechanisms, it’s also possible for clients to protect servers and systems from potential dangers by:
- Installing updates: Keep systems up to date with new security features and system patches to help create stronger security systems.
- Educating users on cybersecurity: SMB users should be aware of the dangers of cybersecurity at all times, including how to identify attacks and ways to protect against hackers.
- Browsing with a VPN: A VPN can help mask locations and encrypt server data, which can protect users from malicious actors.
- Using antivirus software: Antivirus software can warn users of potentially dangerous actions and keep systems protected from attackers.
Answering the question “What is SMB?” and understanding its importance to online security is an almost foolproof way to help clients, servers and shares be informed about and stay protected from online dangers. To keep your PC clean and protected, update SMB protocols when necessary and exchange data with caution.
Sources: UpGuard | TechTarget






1 comment
Thank you for mentioning Visuality Systems in your thorough article. It’s important to note that it’s not a category but rather a company (therefore it should be capitalized) that offers commercial SMB protocol libraries (available in either C or Java) that can be ported and integrated into any platform and operating system, from embedded devices and RTOS to Storage and Cloud environments.