It’s December 1989, and Joseph L. Popp, an American evolutionary biologist from Harvard, walks into his local post office carrying a large stack of envelopes stamped “PC Cyborg Corporation”. He carefully slides each one into the “Outgoing” slot. Finished, Popp exits the post office, unaware he’s just kickstarted one of the most lucrative cybercrime activities of the 21st century: ransomware.
A continent away, a female researcher at the World Health Organizations opens one of Popp’s envelopes. Inside is a 5 ¼-inch floppy disk with instructions to carry out a research survey to test the risks of contracting AIDS. Excited, she inserts the disk expecting to see cutting-edge research into a virus currently plaguing the world.
Instead, she’s receives to a computer virus.
The computer display reads, “Restart your computer now.” She shuts her PC down and reboots. Nothing. “Turn on your printer,” the computer suddenly demands. The printed paper exits inch by inch, finally revealing a ransom note demanding $189 for a “licensing fee” in exchange for a decryption key. The money is to be mailed to a P.O. box in Panama. If the money is not sent, then decades of research data will be deleted.
Joseph Popp mailed 20,000 of these envelopes to 90 countries around the globe before the FBI captured him at his parents’ home in Ohio. Fearful of the breach, some researchers preemptively deleted decades worth of data, even though Popp’s crude ransomware was later easily defeated by computer techs. One Italian AIDS organization reportedly lost 10 years of work.
Popp’s story is the first ransomware attack, and it illustrates how cybercriminals pray on our hopes and fears. The Harvard biologist’s malware bares little resemblance to today’s strains. In just three decades, ransomware has gone from post office packages to self-replicating, viral monsters capable of infecting hundreds of thousands of computers around the world.
Today, ransomware attacks are on the rise. A recent Verizon study shows a 50 percent increase in 2017 alone. Ransomware is popular among crybercriminals because it’s the most profitable malware in existence today.
Ransomware works just like a real-life hostage situation. Someone kidnaps your data and demands money. There are two basic types of ransomware: encryptors and screen lockers.
Encryptors infect your devices and turn your data into unreadable $&@%#* gibberish. Screen lockers shut off access to your computer by taking over the operating system. They deny access to the data but don’t encrypt it.
If you know which type of ransomware you’re dealing with, you have a better chance of getting your money back.
Screen Lockers
Ransomware works for one simple reason — it attacks our emotions. The fear of losing your family photos or that novel you’ve been working on is palpable. Fear is what gives cyberthieves the power to manipulate. Here are some common ransomware scams and screen lockers.
Metropolitan Police scam
As you’re scrolling through your Facebook feed, a pop-up window appears out of nowhere. It has an official looking coat of arms next to the words “METROPOLITAN POLICE” in all caps, so you know it’s serious business. The message below reads: “You are accused of viewing/storage and/or dissemination of banned pornography (child pornography/zoophilia/rape etc.)”.
After a slight pause to consider what the “etc.” might be, your backbone drops 50 degrees and a knot forms in your gut. You make a hasty mental run through the last websites you’ve visited.
Disgusted at the accusation, you maneuver your cursor to the close the window but nothing happens. Your computer is locked, and the only way to unlock it is to pay a “$300 fine” for your alleged digital indiscretions. Now, a live video feed suddenly pops up. On your laptop screen, you now see your own face staring back at you. You’re horrified. Someone has hacked your webcam and is spying on you. Welcome to the Metropolitan Police ransomware attack.
How did this happen? Many types of ransomware infect systems through phishing emails. Hackers use false accusations, threats of incarceration, and voyerism to motivate victims into paying ransoms. Many infections come from phishing emails that trick users into visiting malicious websites or downloading infected attachments.
Should you start packing for a trip to prison? No. The Metropolitan Police attack is a scam and doesn’t directly threaten your data through encryption. The only malware you have on your computer is the script running the pop-up window and accessing your computer. Nevertheless, the ransomware is effective at intimidating people enough to pay the “fine”. Never pay the ransom. Instead, download antivirus removal software.
FBI MoneyPak scam
The FBI MoneyPak scam is a variation on the Metropolitan Police attack and uses the same types of intimidations. The pop-up looks like an official FBI notice, warning users they’ve infringed copyright laws by illegally downloading files like MP3s, movies, and software. Although the FBI MoneyPak doesn’t hijack your webcam, it does deploy a similar scare tactic, claiming authorities can identity you through your IP address.
Cyberthieves demand payment of the ransom through the online wallet service MoneyPak, a competitor to other sites like PayPal or Serve. Hackers may also require a prepaid debit card. Again, the MoneyPak attack is a scam, not a legitimate ransomware attack that threatens your data.
Protect yourself from these types of scams by enabling automatic updates for your operating systems.

Encryptors
Recent cybersecurity studies show encryptors as the most effective forms of ransomware today. Hackers are developing more sophisticated forms of encryptors, which are not only harder to detect but are capable of replicating themselves. Unlike basic screen lockers, encryptors do threaten your data.
CryptoLocker
Inspired by viruses like the Metropolitan Police scam, hackers have developed data-threatening ransomware like CryptoLocker, which hijacks users’ documents and gives the victim 72 hours to pay the ransom. To kick up the drama, an ominous clock is included with CryptoLocker that begins a countdown to data doomsday.
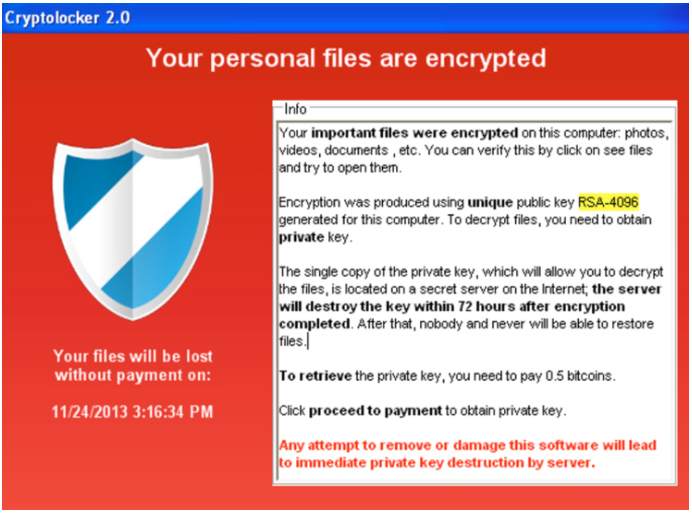
CrytoLocker infections come from an email containing ZIP files and passwords for activation. When you open the email and enter the password, a trojan virus is deployed on your system and begins encrypting your hard drive. The hacker then makes a private key that becomes the only access to decrypting the data. If you don’t pay the ransom, the key is destroyed and the data stays encrypted.
Keep your data out of hackers’ hands by taking away their power to destroy it. Keep your data backed up in a separate drive or in the cloud.
WannaCry Attacks
On Friday, May 12th, 2017, North Korea launched an enormous ransomware attack that spread around the globe. The WannaCry attacks of 2017 were the world’s most widespread and destructive ransomware attack to date — infecting more than 230,000 computers in 150 countries. The hackers required a $300 ransom payment, a clear signal they were targeting small businesses, organizations, and individuals.
WannaCry ransomware is feared in cybersecurity circles for its ability to self-replicate. WannaCry doesn’t need you to open an email or download an attachment from a website. It replicates through a worm virus, sending copies of itself throughout the internet.
WannaCry gains entry through vulnerabilities in your operating system and takes over your computer, encrypting your data and demanding a ransom. Like most data-destructive ransomware, by the time users discover they’re infected, it’s too late.
Ransomware has become exponentially more sophisticated and destructive since Joseph Popp snail mailed his infected floppy disks. Analog delivery methods have given way to more autonomous forms as cyberthieves mix and match malware characteristics to create new strains. In June of 2017, cybersecurity experts discovered a new form of ransomware called Petya, which includes features of both screen lockers and encryptors. If you’re worried about ransomware, protecting yourself is fairly simple. Follow tips for avoiding ransomware and invest in comprehensive antivirus software.









5 comments
Rattling fantastic visual appeal on this web site, I’d rate
it 10.
Thanks!
Hey,
in regards to Hydros Cyber attack last night (19.03.2019).
(https://www.bleepingcomputer.com/news/security/lockergoga-ransomware-sends-norsk-hydro-into-manual-mode/)
have you done anything to shield your customers against the so called “LockerGoga” Virus?
i have not found any news post about this virus in particular.
THanks.
Hi Mads,
Our solution Panda Adaptive Defense was able to detect this ransomware via generic signatures, meaning that every Adaptive Defense Customer was safe from the infection from the very start. You can find out more about it here: https://www.pandasecurity.com/en/mediacenter/news/lockergoga-ransomware-norway/
Thanks for reading!