Small businesses (SMBs) account for about 43% of cyber attacks annually, despite their size and revenue. Being small doesn’t necessarily mean you are more protected — in fact, sometimes it means just the opposite because IT teams are unprepared, infrastructure is underfunded and employees are uninformed. Even medium-sized businesses can be vulnerable to dangerous cyber attacks.
Keeping your SMB protected from cybercriminals and hackers of all types is more important now than ever. Investing in premium protection plans and following these 13 cybersecurity tips for small businesses can help you defend your business and protect your online systems.

1. Complete a Risk Assessment
Before investing in antivirus software, VPNs and other protection measures, perform risk and vulnerability assessments to identify where your systems face the most threat. These assessments can provide SMBs with a list of potential vulnerabilities as well as areas where security improvements would make a substantial difference.
2. Install Antivirus Software
Small businesses can protect their systems from potential threats by installing antivirus software. Many antivirus systems can detect threats before they break through a company’s security protocols, acting as one of the first lines of defense against a cyberattack. Additionally, antivirus for small businesses is usually scalable and easy to install.
3. Utilize Virtual Private Networks
To increase your business’s protection while employees are traveling or working remotely, use a virtual private network (VPN). VPNs provide users with a secure network connection and protect vulnerable IP addresses and data from hackers or breached public networks.
4. Secure the Network
The tools you use to protect your networks and infrastructures are vital to the level of protection your devices achieve. Defense mechanisms that are able to protect against active and inactive malware, encrypt SSIDs and hide identifying information are indispensable. Investing in state-of-the-art protection, detection and remediation technology tools like WatchGuard EDR and Panda Adaptive Defense can help you secure your network against both external and internal attacks.
5. Keep Machines Clean
Yes, it’s important to keep your machines clear of dust and dirt, but it’s more important to keep your internal systems clean. Install the latest security software and update your device’s operating systems to ensure bug fixes are installed and your systems are up-to-date with the newest protections.
6. Avoid System Mobility
In a perfectly controlled network, the contingencies that could endanger the system are reduced to almost zero. However, as soon as IT employees clock out for the day, that control is lost. Keeping the system isolated by maintaining no contact at all with personal networks or devices outside the working environment is the best way to avoid this. Teams can also create and employ firewall protections to add an additional layer of security while systems are idle.
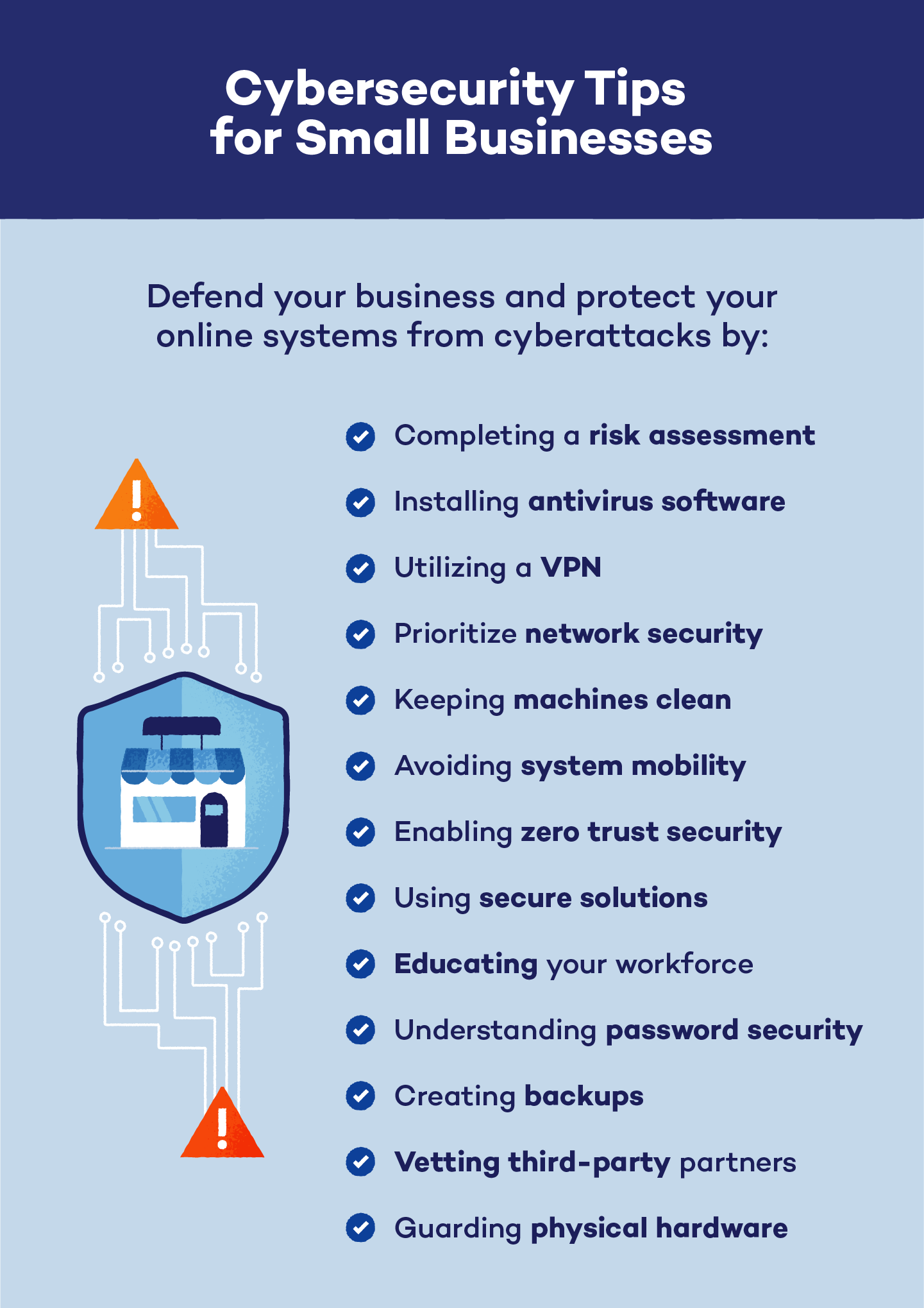
7. Enable Zero Trust Security
System breaches can come from anywhere. To keep your small businesses’ systems as secure as possible, set up and enable zero trust security. This will require all accessors — including both internal and external actors — to authenticate their identity before gaining access to the system. Additionally, zero trust architecture systems are segmented so users are only granted access to specific areas of a system.
8. Use Secure Solutions
When it comes to payments, data transfers, and other sensitive operations, it’s important to maintain security and data integrity. Using adequate encryption methods, reliable certificates and secure payment platforms is essential. Plus, small businesses should incorporate multi-factor authentication into their system protocols, and refrain from using personal mobile devices as secondary security sources.
9. Educate Your Workforce
Employees are an SMB’s first line of defense in the face of a cyberattack, so they need to know the possible dangers and access points a hacker may try to break through. Employee training and education should focus on security practices, working protocols, prohibited actions, and how to solve problems stemming from cyber activity.
10. Understand Password Security
Strong passwords can make or break the security of any organization, including small businesses of all types. Create passwords at least eight characters long with alphanumeric characters, uppercase and lowercase letters, and symbols to increase their strength. It is also advisable to change them from time to time, never use the same password for more than a year and utilize a password manager for added security.
11. Create Backups
Although there are solutions and companies dedicated exclusively to safeguarding companies’ data, the value of backups should never be underestimated. Maintaining consistent backups of all company data can protect SMBs from the danger of some cyberattacks and prevent ransomware attacks.
12. Vet Third-Party Partners
If your SMB partners with a third party, vet them and their employees before granting them access to your systems. Zero trust security can provide additional protection surrounding your infrastructure systems, but background checks are encouraged before granting network access.
13. Guard Physical Hardware
While hackers are well-known for attacking devices from a distance, they may choose to access devices physically if they have the chance. Keep devices away from unauthorized individuals, and enable remote wiping access so you can protect your system’s security on lost or stolen devices. Additionally, electronic devices should be wiped and recycled instead of thrown away during times of device transition.
These cybersecurity tips for small businesses are not meant to be fail-safes. Rather, these tips should be put into practice well before a cyber threat occurs.
More than 30 million users trust Panda Security to keep their information and businesses protected from cyberattacks — and you can, too! Our remote support teams can help tailor our services to your business’s specific needs.


1 comment