The fact that the technology landscape is constantly changing isn’t a new phenomenon, but it’s certainly been taken to new heights in the last year. The word “disruption” adequately describes the experiences of countless organizations amid COVID-19—no one could have predicted its impact on business, technology and cybersecurity. Here, we’ll analyze the emerging threat landscape that’s come as a result, and what cybersecurity trends pose the most risk in 2021 and beyond.
1. Impact of Remote Work: New Threats and Solutions
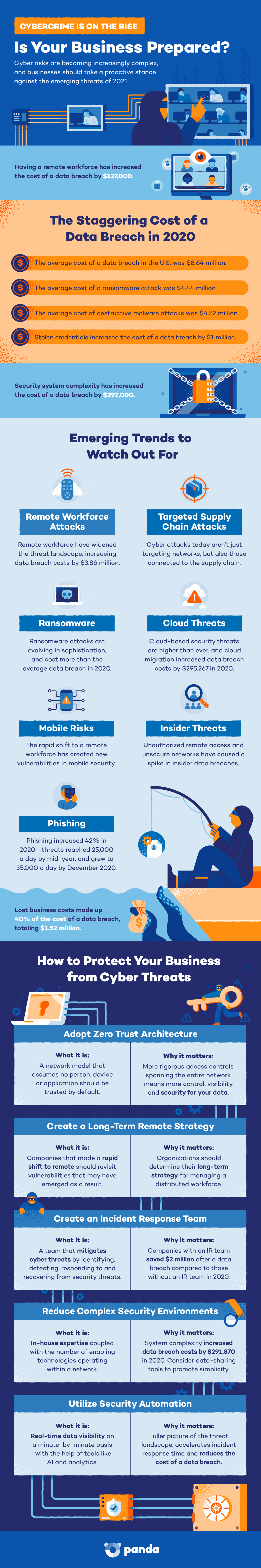
It’s no surprise that COVID-19 and the resulting shift to remote work had major implications for the world of cybersecurity. For many, it involved unplanned cloud migrations and swift procurement of IT products and services to accommodate a newly remote landscape. In the effort to keep business operations running, many companies rushed typical security measures or even side-stepped them entirely, creating new levels of vulnerability and risk across all industries.
Not only that, but the world of remote work isn’t going anywhere post-pandemic. Organizations will need to assess their current security infrastructures for areas of weakness that were left unattended during the sudden shift to remote and start thinking about a long-term remote security strategy going forward.
Key takeaway: If your organization experienced a sudden shift to a remote workforce, you must identify areas of weakness that left your company vulnerable to threats.
2. New Challenges from Ransomware
Ransomware is one of the most common threats to any organization’s data security, and this threat will continue to increase and evolve as a top cybersecurity trend in 2021. Ransomware attacks plague organizations with data theft and economic blows due to the costs of recovering from these attacks. In 2020, ransomware attacks were more expensive than the average data breach, costing $4.44 million on average.
The sophistication of techniques criminals are using is growing, too. There’s an increasing emphasis on extortion attacks, where criminals steal a company’s data and encrypt it so they can’t access it. Afterward, cybercriminals will blackmail the company, threatening to release its private data unless a ransom is paid. The burden of this cyberthreat is significant given the sensitive data on the line as well as the economic impact of paying the ransom.
While many IT departments and companies rely on Virtual Private Networks (VPNs) to facilitate access to their corporate network, VPNs are proving inadequate in 2021 and beyond. The most common entry vector for ransomware is phishing, and organizations should realize these attacks are ramping up significantly and act accordingly. Zero-Trust Network Access (ZTNA) has emerged as a more secure option for controlling remote access to sensitive data and reducing the likelihood of an attack. By 2023, 60% of businesses will phase out of VPNs and transition to ZTNA.
Key takeaway: Transition to ZTNA to strengthen your company’s remote access network and reduce the risk of an attack.
3. Increased Use of Multi-Factor Authentication
While passwords remain a standard for cybersecurity best practices, more companies will adopt multi-factor authentication (MFA) as an additional defense against data breaches and malicious attacks in 2021. MFA involves the use of two or more separate factors in authorizing users to access secure data, forcing people to use more than one device to confirm their identity. An example of MFA in action is having a one-time passcode sent to two or more devices .
While the use of MFA is critical to security, Microsoft recently urged users to move away from phone-based MFA (when the one-time passcode is sent to your phone via SMS text) due to the weak security among telephone networks today. SMS-based aren’t encrypted, meaning attackers can gain access to these plain text codes. This means companies should choose more secure MFA methods to implement, namely application-based MFA like Google Authenticator or Microsoft Authenticator.
Key takeaway: Consider implementing MFA in your organization, and be wary of the risks associated with phone-based MFA.
4. Continued Rise of AI
AI and machine learning are growing in sophistication and capability, and companies will continue to hone these technologies in 2021 as part of their security infrastructure. AI is increasingly being used to build automated security systems that replace human intervention, making it possible to analyze massive quantities of risk data at a much faster pace. This is beneficial both for large companies dealing with huge amounts of data and small or mid-sized companies whose security teams might be under-resourced.
While AI presents a major opportunity for stronger threat detection among businesses, the evolution and increased use of this technology goes both ways. Criminal networks are taking advantage of AI to automate their attacks, and they are turning to data-poisoning and model-stealing techniques to do so. That said, organizations would be remiss to bypass the opportunity AI presents—organizations who suffered a data breach but had AI technology fully deployed saved an average of $3.58 million in 2020.
Key takeaway: If you haven’t already, implement AI-powered security systems in your business to streamline threat detection efforts and potentially save millions in the event of a data breach.
5. Increased Attacks on Cloud Services
With the rapid and widespread adoption of remote work following COVID-19, the necessity for cloud-based services and infrastructure increased drastically. Going into 2021 and beyond, this trend will only continue to grow as more businesses adopt cloud-hosted processes.
While cloud services offer a wealth of benefits such as scalability, efficiency and lower costs, they’re still a prime target for attackers. Organizations will need to take stock of the security implications that come with the cloud and determine any vulnerabilities that exist in their current infrastructure. For example, misconfigured cloud settings were a leading cause of data breaches in 2020—and resulted in an average total cost of $4.41 million. Additionally, migration to the cloud increased the cost of the breach by $267,469.
Key takeaway: Before undergoing a workload migration to the cloud, make sure you’re aware of the security measures you should have in place to avoid a data breach.
6. Data Privacy as a Discipline
With the growing number of high-profile cyber attacks exposing millions of personally identifiable information (PII) records, concerns about data privacy, management and security have skyrocketed. In 2021, data privacy will no longer remain a single component of a security program, but will become a program of its own. Regulatory compliance requirements have continued to increase and will continue to do so in 2021, and organizations will be required to focus on their data privacy efforts moving forward.
Data privacy impacts almost every aspect of an organization, from creating and implementing the corporate strategy to staying in alignment with security and HR throughout the process. Organizations should consider things like data privacy officers, record retention and destruction, role-based access control, encryption in transit, and network segmentation to assess where they can strengthen their data privacy in 2021 and beyond.
Key takeaway: Data privacy is taking a larger role in the security of organizations across all industries, and taking the time to understand the areas of weakness in your business should be a top priority.
7. COVID-19 Phishing Schemes
With the continued release of the COVID-19 vaccination, people are increasingly searching for vaccination information such as where it’s being provided and who’s been approved to get it. Unfortunately, this has brought about a significant level of phishing attacks tied to the COVID-19 vaccine. Attacks against pharmaceutical companies and vaccine distributors, along with email phishing attacks disguised as vaccination appointment emails, are on the uptick.
Phishing attacks are even more troubling amid the widespread remote workforce, and attackers hone in on individuals connecting to their employer’s network from home because they’re the easiest targets. To combat this, organizations should consider their identity management and security strategy and ensure only the right people have the appropriate level of access to the resources they need at the right time. Organizations will need to thoroughly assess their current infrastructure to align with this goal, while paying special attention to company-wide implementation.
Key takeaway: Improve your company’s identity management strategy to combat an insecure remote workforce, and ensure all departments are aligned with the policies enacted to mitigate risk.
8. Increased Need for Cybersecurity Professionals
Finding well-trained cybersecurity professionals has historically been a challenge across all industries, but the continued shift to and dependence on a more distributed workforce is creating a more critical need for them in 2021. Organizations will need to push to find well-trained professionals and subject matter experts to help increase the security of corporate networks.
As companies set out to hire more cybersecurity professionals, they should also focus on educating their employees on how to spot attacks on their own. While it may take some time to adequately staff your organization with the right cybersecurity experts, implementing company-wide training can provide a buffer for attacks in the interim. Training should be continuous and companies should constantly measure its effectiveness. Executives should also be involved—for such an initiative to be successful, it must be implemented from the top down.
Key takeaway: Prioritize cybersecurity staffing company-wide security training as a top goal for 2021.
9. Insider Threats on the Rise
As we continue to navigate a remote workforce, insider threats are becoming a heightened area of concern. While it’s far easier to believe that all cybersecurity threats come from external forces, organizations shouldn’t ignore the reality and increasing sophistication of threat actors within their own company. This is especially true as organizations continue to hire remote-only employees who are scattered across the world, and who they may have hired only after meeting virtually.
In 2021, companies must give more consideration to the possibility of insider threats and data theft at the hands of their own employees. While this can be difficult to come to terms with, the data doesn’t lie—15% to 25% of security breach incidents are caused by trusted business partners. Inside threats must be taken seriously and seen as a real risk by security leaders, and tough questions will need to be asked about whether organizations have the proper tools in place to spot and stop them.
Key takeaway: Inside data breaches are on the rise, and companies should have the proper tools and systems in place to detect them.
10. Increased Need for Chief Security Officers
While the need for strengthened security systems across industries is well known, only 11% of companies report a high degree of confidence in managing or responding to a cyber attack. Security risk management as a discipline is still maturing, so while this data isn’t all that surprising, it should be an area of importance for companies moving into 2021. One increasingly common barrier is a lack of alignment between security operations and business strategy.
The disconnect between security and business reduces the effectiveness of cybersecurity initiatives, as the baseline for what’s considered adequate risk management is disjointed across departments. To combat this, Chief Security Officers will need to become more vigilant in identifying risks in the context of business objectives and be able to explain why they matter to business leaders. By pinpointing these risks and articulating how they plan to lower them (and at what cost), CSO’s can create a shared understanding between business and security leaders that strengthens cybersecurity initiatives across the board.
Key takeaway: CSO’s should prioritize creating alignment among corporate leaders and organizational security initiatives and goals.
11. Critical Need for Real-Time Data Visibility
While many executives are managing cybersecurity risks for some aspects of their organization, their efforts are weakened without a comprehensive picture of the company’s entire technological landscape. Many executives don’t have a full IT asset inventory or a complete list of all third-party suppliers and cloud applications used within their organization. This results in weakened risk assessment programs, since they’re often based on inventories that lack a full and clear picture of the threat landscape.
To combat this, introducing security automation and real-time data visibility within organizations is imperative to managing data protection to the fullest degree. The only way to prevent data loss is to know exactly where your data is, and for 2021 and beyond, knowing this on a minute-by-minute basis. Implementing automated security systems not only strengthens companies’ ability to mitigate data theft and breaches, but also heightens operational efficiency and overall resilience to cybersecurity threats.
Key takeaway: Organizations must introduce real-time user activity monitoring with the help of cloud-native solutions to create a more robust security infrastructure and full visibility of every possible threat.
Cybersecurity Hygiene in 2021 and Beyond: Tips for Businesses
From what we’ve seen so far, many of the cybersecurity trends that we’ve seen in the last few years have been accelerated by COVID-19, and organizations should take these risks seriously. Being proactive will be one of the most important actions businesses can take in 2021— organizations who come to terms with the fact that security is no longer an optional investment will more successfully withstand the cybersecurity challenges they now face.
Prioritize Growing Your Cybersecurity Workforce
The cybersecurity workforce shortage stubbornly persists into 2021, while the security risks faced by companies today continue to grow. With 56% of organizations reporting a shortage of cybersecurity staff in 2020, organizations must prioritize growing their cybersecurity workforce to secure the fast-expanding digital world they face today.
Invest in Security Automation
With the amount of data multiplying every day, hyper automation—the process in which businesses automate as many IT processes as possible—is more imperative than ever. In 2020, IBM found a $3.58 million difference in the average total cost of a data breach for organizations without security automation versus those with automation fully deployed. Organizations should consider implementing automation tools as a way to collect and analyze data in real time, accelerate incident response time and save money in the process.
Educate Your Staff
Many companies miss a golden opportunity to strengthen their data protection efforts—creating a culture of cybersecurity awareness and education among their entire staff. A threat can’t be avoided if it isn’t recognized, and equipping your staff to identify threats on their own can significantly reduce the likelihood of a data breach. Ongoing training will be essential going forward, and leaders who instill the fact that every role is responsible for understanding cybersecurity risks will find the most success.
As companies continue to navigate the new challenges of cybersecurity in 2021, approaching their security strategies with a sense of urgency will separate those who are equipped to reduce overall risk and those who will remain vulnerable to the increasing attacks we face today. This is especially true as organizations continue with full-time or a hybrid-model of remote work, where threat actors are becoming more sophisticated with their ability to infiltrate networks and compromise data.
As these trends continue to evolve, organizational leaders will seek out new ways to properly secure their data and defend against increasingly complex cyberattacks. The same applies to cybersecurity on the consumer level, and implementing a cross-platform antivirus program can provide better protection for all your devices as we operate in the new normal of 2021.