UPDATE 24th May 2019
In order to prevent the exploitation of the critical vulnerability of Microsoft - BlueKeep (CVE-2019-0708) - and to ensure the correct protection of all clients that have not yet installed security updates on computers with vulnerable operating systems, Panda Security has deployed a new detection called W32 / BlueKeep.A.worm.
In the case of Panda Adaptive Defense products, the detection is carried out by the advanced protection, whereas in the case of Panda Endpoint Protection products, it is implemented by the firewall module. Therefore, it is necessary that these protections are active for the new detection to be implemented. What's more, this detection is only applicable on protection versions 8.0010.X or higher, so if you have previous versions of protection, we recommend planning the update as soon as possible.
We remind you nonetheless of the importance of applying the corresponding Microsoft patches indicated in the Support article, to close the door permanently to the exploitation of this type of vulnerabilities.
***************************************************************************************************************
Situation
On May 14, 2019, Microsoft has released its monthly security update for May, which included a set of security updates for the various supported versions of the Microsoft Windows operating system. One of the updates addressed CVE-2019-0708, a critical remote code execution vulnerability that could allow an unauthenticated remote attacker to connect through RDP and run remote code on a vulnerable target running Remote Desktop Protocol (RDP).
Potentially, this vulnerability, if exploited, could spread very rapidly.
Affected operating systems
- RDP on Microsoft Server 2008/2008 R2 and Windows 7.
- End-of-Life operating systems Windows Server 2003 and Windows XP.
Panda Security urges you to apply the Microsoft Security Updates for all vulnerable systems, in particular, those computers with RDP. Please click on the links for the appropriate downloads:
- Windows 7, Windows Server 2008 and Windows Server 2008 R2.
- End-of-life systems: Windows XP, Windows XP Professional, Windows XP Embedded and Windows Server 2003.
- Enable Network Level Authentication (NLA) on supported systems (Windows 7, Windows Server 2008, and Windows Server 2008 R2).
- Disable the Remote Desktop Service on those computers where its use is not essential.
In addition, Panda Security recommends setting up in LOCK mode any computer in your organization with Panda Adaptive Defense and Panda Adaptive Defense 360 that uses RDP to guarantee optimal protection for them.
| Traditional Platform | Aether Platform |
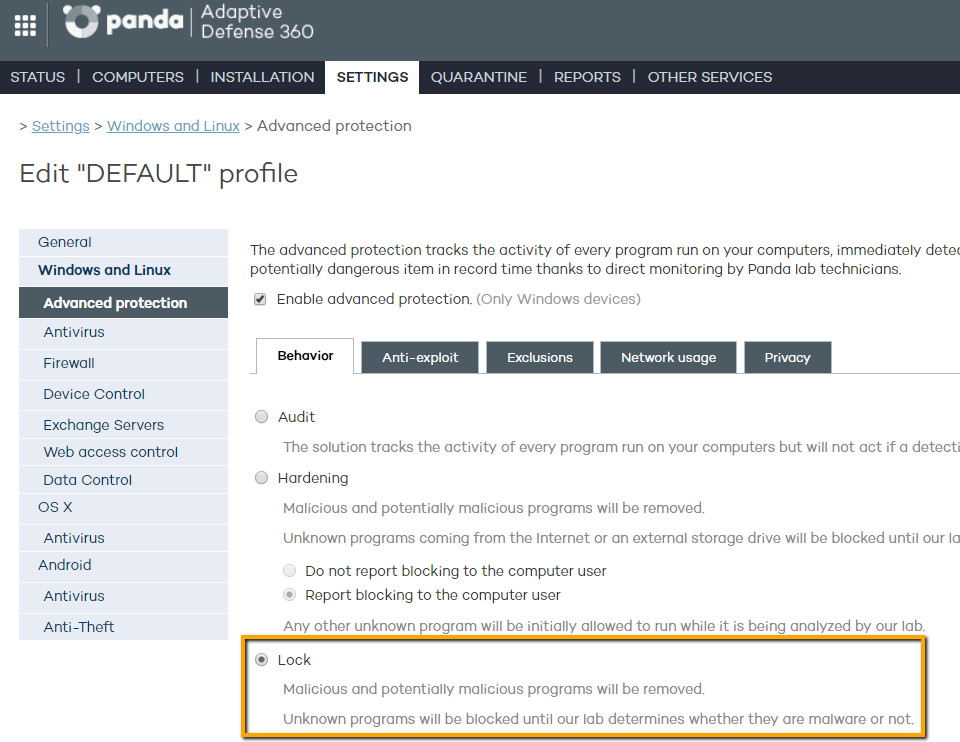 | 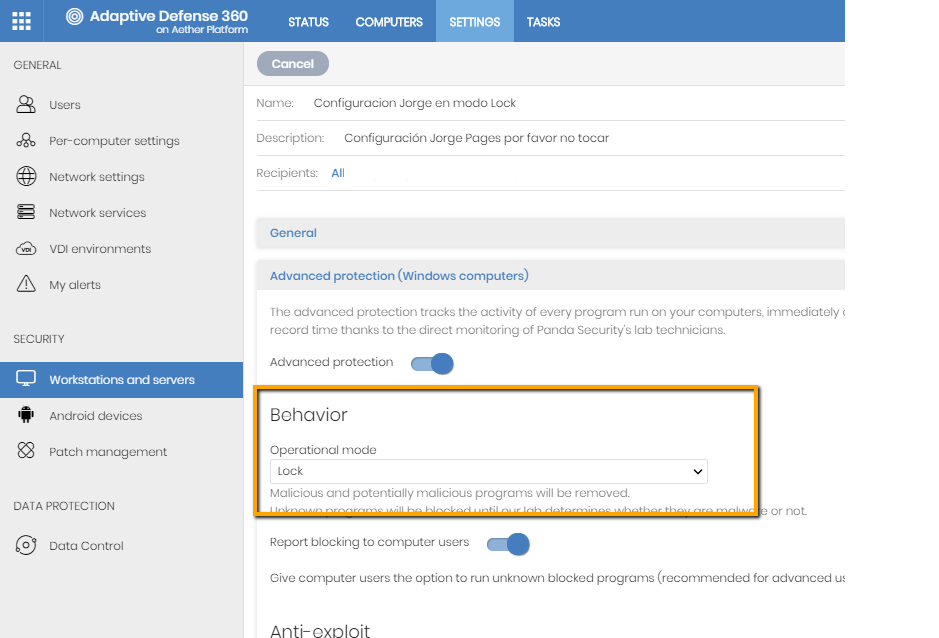 |
We want to emphasize the importance of protecting your systems from cyberattacks. In this specific case, we recommend patching all computers with RDP resources and ensure you install a suitable security solution to keep your infrastructure fully updated.
Security solutions such as Panda Patch Management, which manages vulnerabilities and their corresponding updates and patches, both for operating systems and hundreds of applications or Panda Systems Management, which manages, monitors and maintains all the devices in your organization in check are highly effective for this purpose.
How to patch the BlueKeep RDP Vulnerability (CVE-2019-0708): Panda Patch Management
Let’s see how the Panda Patch Management module integrated in Panda Adaptive Defense 360, helps you to find critical security vulnerabilities using their CVE-ID, and prevent them from being exploited by isolating the affected computers and installing the patch that fixes the flaw.
In this video we will show you how to prevent and patch BlueKeep: Windows Remote Desktop Services vulnerability.