Many travelers are hoping to go off-grid with their upcoming travels, but this doesn’t mean they want to be completely disconnected from reality — or the internet. The last thing travelers want to worry about is how to find Wi-Fi when traveling while they’re sitting on the beach, trekking through the mountains or eating a new culinary dish.
If you’re looking to surf the internet safely while on holiday or simply need Wi-Fi to get to your destination, our seven options below can help you get internet for travel.
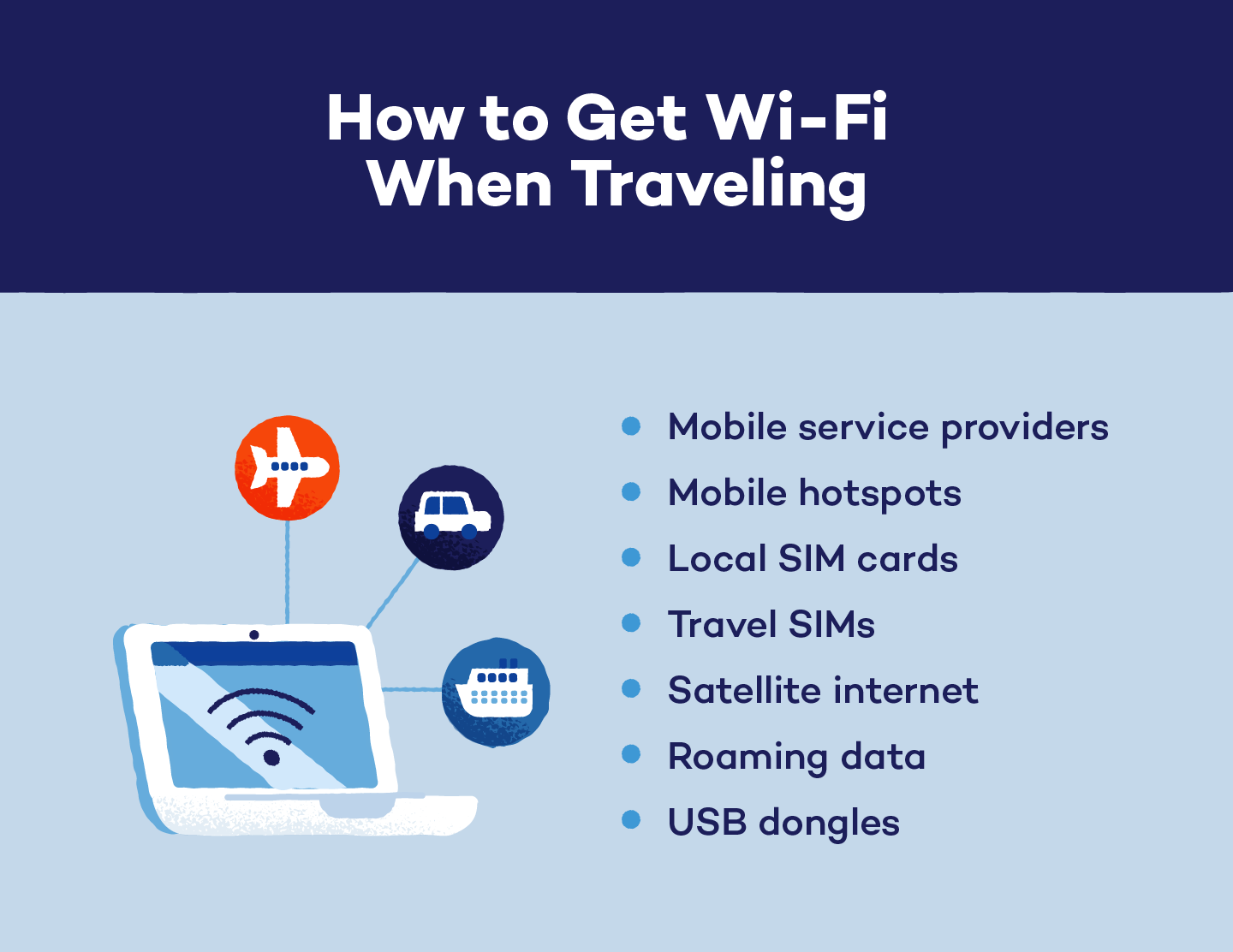
1. Mobile Service Providers
Before jetting, contact your mobile carrier to see what — if any — type of data plans they may offer for travelers. Most major cellular carriers in the U.S. have agreements with foreign telecom companies, so getting an international plan added to your account might help you avoid other costly options.
Some service providers also have hotspot options for smart devices, which can be used to connect additional devices to Wi-Fi when traveling. You can discuss this option with your carrier when inquiring about international plans.
2. Mobile Hotspots
Mobile hotspots are physical, standalone devices that can create local internet hotspots for users. These devices can also be used by RV travelers for better internet reception.
There are two ways you can get a mobile hotspot:
- You can rent a mobile hotspot where prices depend on the amount of data you want, where you are traveling and how long you will be gone.
- You can buy a mobile hotspot where prices depend on the make, model and amount of data you want.
Mobile hotspots are a great option for family vacations because they allow users to connect multiple devices at once. However, they can be expensive and they only work when devices are within range.
3. Local SIM Cards
As a more cost-effective solution, consider buying a local SIM card for the places you are traveling to. Usually, you will need to buy this when you arrive at your destination but it’s sometimes possible to buy SIM cards before you depart. Check your destination’s local regulations about SIM card purchases before pursuing this option.
4. Travel SIMs
Travel SIMs — or roaming SIMs — are specifically designed to provide users with internet for travel. These SIM cards don’t need to be switched in and out of a device while traveling because they can operate on more than one network. This option can be more expensive than purchasing a local SIM card, but it can also be a great solution for users with outrageous international plan prices.
5. Satellite Internet
If you need to get online while traveling by RV, boat or another large transport device, satellite internet is a potential internet solution. While satellite receivers need to be mounted to an object, need a clear view of the sky, and are often more expensive than other service options, they can provide internet for travel when mobile hotspots can’t.
6. Roaming Data
One of the easiest ways to get internet for travel is to use roaming data offered by a cell service provider. This can be costly — especially if you’re traveling for extended periods — but it’s usually instant and fairly reliable.
7. USB Dongles
If you are working abroad and need to connect to the internet, a USB dongle is a safe option. While these devices sometimes have limited speed and stability, they offer protected internet access for laptops and other desktop devices. Additionally, dongles need compatible SIM cards, so they aren’t always the most practical option.
Other Tips and Tricks For Getting Internet for Travel
Finding or carrying Wi-Fi when traveling comes with a few precautions. To keep your information safe when you’re away from home, follow these tips and tricks for traveling internet.
Avoid Public Wi-Fi Networks
You might feel tempted to join public Wi-Fi hotspots while away, but doing so can put you and your devices at risk because many public Wi-Fi networks are poorly managed. As a result, your traffic might be monitored by the network administrator or a hacker who has cracked the network.
Use a VPN
If you must connect to a public network, only do so if you have downloaded a reliable VPN. VPNs are designed to keep your online browsing secure and private, protecting your personal information and conversations.
Be Aware of Juice Jacking
Charging stations at airports and coffee shops may be compromised by malicious software. Make sure you have proper antivirus software or bring your own AC adapter to charge your devices. If you are ever asked to ‘trust’ a computer when charging your device on a public USB station, always hit ‘no’ and decline access.
Bring Backups
Backups — for both physical and digital items — are highly recommended when traveling. Keep important documents backed up to a secondary device or location, and pack spare charging cables and power banks in your luggage. If your devices are compromised or run out of battery, backups will keep you prepared.
Prepare Maps and Documents
While you may do everything you can to keep yourself connected to Wi-Fi when traveling, you may still be disconnected at some point. Prepare by pre-downloading maps of the area you are planning to visit and securing important documents behind encryptions and firewalls.
Traveling should be a time to relax or discover new places. The last thing you want to worry about is staying connected to friends and family or cybercriminals ruining your vacation. Protect your devices with a premium defense plan from Panda Security so you can enjoy Wi-Fi when traveling while keeping your mind at ease.
Sources: Booking.com







